Google Chrome Bug Could Let Hackers Bypass CSP Protection; Update Web Browsers
6.5 Medium
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
HIGH
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N
4.3 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:M/Au:N/C:N/I:P/A:N
If you haven’t recently updated your Chrome, Opera, or Edge web browser to the latest available version, it would be an excellent idea to do so as quickly as possible.
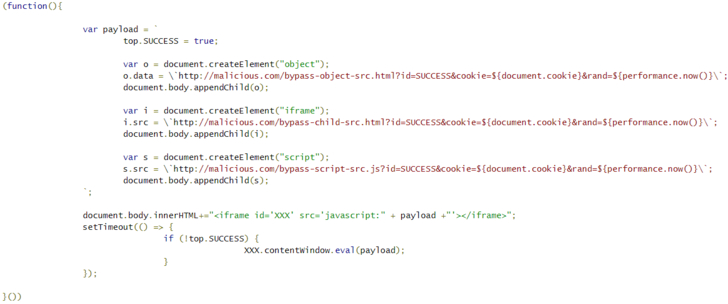
Cybersecurity researchers on Monday disclosed details about a zero-day flaw in Chromium-based web browsers for Windows, Mac and Android that could have allowed attackers to entirely bypass Content Security Policy (CSP) rules since Chrome 73.
Tracked as CVE-2020-6519 (rated 6.5 on the CVSS scale), the issue stems from a CSP bypass that results in arbitrary execution of malicious code on target websites.
According to PerimeterX, some of the most popular websites, including Facebook, Wells Fargo, Zoom, Gmail, WhatsApp, Investopedia, ESPN, Roblox, Indeed, TikTok, Instagram, Blogger, and Quora, were susceptible to the CSP bypass.
Interestingly, it appears that the same flaw was also highlighted by Tencent Security Xuanwu Lab more than a year ago, just a month after the release of Chrome 73 in March 2019, but was never addressed until PerimeterX reported the issue earlier this March.
After the findings were disclosed to Google, the Chrome team issued a fix for the vulnerability in Chrome 84 update (version 84.0.4147.89) that began rolling out on July 14 last month.
CSP is an extra layer of security that helps detect and mitigate certain types of attacks, including Cross-Site Scripting (XSS) and data injection attacks. With CSP rules, a website can mandate the victim’s browser to perform certain client-side checks with an aim to block specific scripts that are designed to exploit the browser’s trust of the content received from the server.
Given that CSP is the primary method used by website owners to enforce data security policies and prevent the execution of malicious scripts, a CSP bypass can effectively put user data at risk.
This is achieved by specifying the domains that the browser should consider to be valid sources of executable scripts, so that a CSP-compatible browser only executes scripts loaded in source files received from those allow-listed domains, ignoring all others.
The flaw discovered by Tencent and PerimeterX circumvents the configured CSP for a website by merely passing a malicious JavaScript code in the “src” property of an HTML iframe element.
It’s worth noting that websites like Twitter, Github, LinkedIn, Google Play Store, Yahoo’s Login Page, PayPal, and Yandex were not found vulnerable since the CSP policies were implemented using a nonce or hash to allow the execution of inline scripts.
“Having a vulnerability in Chrome’s CSP enforcement mechanism doesn’t directly mean that sites are breached, as the attackers also need to manage to get the malicious script called from the site (which is why the vulnerability was classified as medium severity),” PerimeterX’s Gal Weizman noted.
While the implications of the vulnerability remain unknown, users must update their browsers to the latest version to protect against such code execution. Website owners, for their part, are recommended to use nonce and hash capabilities of CSP for added security.
Besides this, the latest Chrome update 84.0.4147.125 for Windows, Mac, and Linux systems also patches 15 other security vulnerabilities, 12 of which are rated ‘high’ and two ‘low’ in severity.
6.5 Medium
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
HIGH
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N
4.3 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:M/Au:N/C:N/I:P/A:N