VMware Patches Important Bug Affecting ESXi, Workstation and Fusion Products
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
HIGH
Privileges Required
LOW
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:H/PR:L/UI:N/S:C/C:H/I:H/A:H
6.9 Medium
CVSS2
Access Vector
LOCAL
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:L/AC:M/Au:N/C:C/I:C/A:C
VMWare has shipped updates to Workstation, Fusion, and ESXi products to address an “important” security vulnerability that could be weaponized by a threat actor to take control of affected systems.
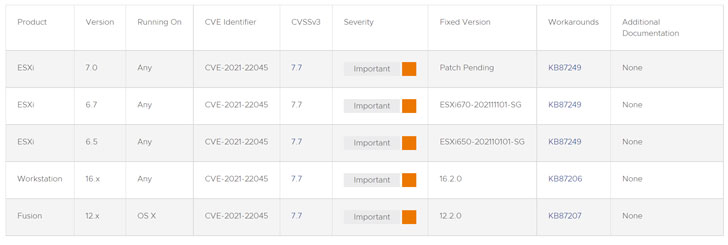
The issue relates to a heap-overflow vulnerability — tracked as CVE-2021-22045 (CVSS score: 7.7) — that, if successfully exploited, results in the execution of arbitrary code. The company credited Jaanus Kääp, a security researcher with Clarified Security, for reporting the flaw.
“A malicious actor with access to a virtual machine with CD-ROM device emulation may be able to exploit this vulnerability in conjunction with other issues to execute code on the hypervisor from a virtual machine,” VMware said in an advisory published on January 4. “Successful exploitation requires [a] CD image to be attached to the virtual machine.”
The error affects ESXi versions 6.5, 6.7, and 7.0; Workstation versions 16.x; and Fusion versions 12.x, with the company yet to release a patch for ESXi 7.0. In the interim, the company is recommending users to disable all CD-ROM/DVD devices on all running virtual machines to prevent any potential exploitation —
- Log in to a vCenter Server system using the vSphere Web Client.
- Right-click the virtual machine and click Edit Settings.
- Select the CD/DVD drive and uncheck “Connected” and “Connect at power on” and remove any attached ISOs.
With VMware’s virtualization solutions widely deployed across enterprises, it’s no surprise that its products have emerged as a popular choice for threat actors to stage a multitude of attacks against vulnerable networks. To mitigate the risk of infiltration, it’s recommended that organizations move quickly to apply the necessary updates.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
HIGH
Privileges Required
LOW
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:H/PR:L/UI:N/S:C/C:H/I:H/A:H
6.9 Medium
CVSS2
Access Vector
LOCAL
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:L/AC:M/Au:N/C:C/I:C/A:C