Cisco Issues Patches For 2 High-Severity IOS XR Flaws Under Active Attacks
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
7.8 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:N/I:N/A:C
Cisco yesterday released security patches for two high-severity vulnerabilities affecting its IOS XR software that were found exploited in the wild a month ago.
Tracked as CVE-2020-3566 andCVE-2020-3569, details for both zero-day unauthenticated DoS vulnerabilities were made public by Cisco late last month when the company found hackers actively exploiting Cisco IOS XR Software that is installed on a range of Cisco’s carrier-grade and data center routers.
Both DoS vulnerabilities resided in Cisco IOS XR Software’s Distance Vector Multicast Routing Protocol (DVMRP) feature and existed due to incorrect implementation of queue management for Internet Group Management Protocol (IGMP) packets on affected devices.
IGMP is a communication protocol typically used by hosts and adjacent routers to efficiently use resources for multicasting applications when supporting streaming content such as online video streaming and gaming.
“These vulnerabilities affect any Cisco device that is running any release of Cisco IOS XR Software if an active interface is configured under multicast routing and it is receiving DVMRP traffic,” Cisco said in an advisory.
“An administrator can determine whether multicast routing is enabled on a device by issuing the show igmp interface command.”
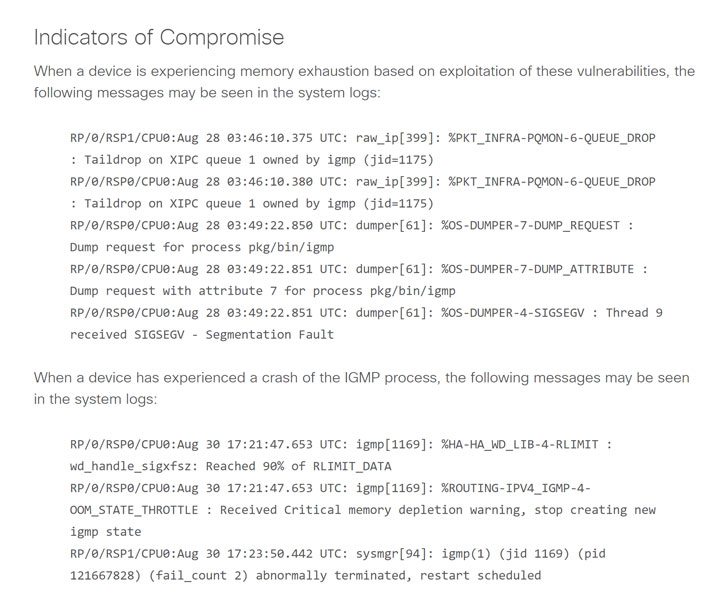
Successful exploitation of these vulnerabilities could allow remote unauthenticated hackers to send specially crafted IGMP packets to affected devices to either immediately crash the IGMP process or exhaust process memory and eventually crash.
The memory consumption may negatively result in instability of other processes running on the device, including routing protocols for both internal and external networks.
The vulnerabilities affect all Cisco devices running any release of Cisco IOS XR Software if an active interface is configured under multicast routing, and it is receiving DVMRP traffic.
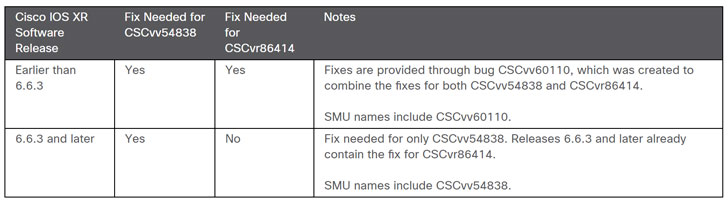
At the time Cisco initially made these vulnerabilities public, the company provided some mitigation to resolve the issues and block the active exploitation attempts, but now it has finally released Software Maintenance Upgrades (SMUs) to address the vulnerabilities completely.
“Although there are no workarounds for these vulnerabilities, there are multiple mitigations available to customers depending on their needs,” the company said.
“When considering mitigations, it should be understood that for the memory exhaustion case, the rate limiter and the access control methods are effective. For the immediate IGMP process crash case, only the access control method is effective.”
Cisco customers are highly recommended to make sure they are running the latest Cisco IOS XR Software release earlier than 6.6.3 and Cisco IOS XR Software release 6.6.3 and later.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
7.8 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:N/I:N/A:C