Microsoft Warns of Critical "PrintNightmare" Flaw Being Exploited in the Wild
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
Microsoft on Thursday officially confirmed that the “PrintNightmare” remote code execution (RCE) vulnerability affecting Windows Print Spooler is different from the issue the company addressed as part of its Patch Tuesday update released earlier this month, while warning that it has detected exploitation attempts targeting the flaw.
The company is tracking the security weakness under the identifier CVE-2021-34527, and has assigned it a severity rating of 8.8 on the CVSS scoring system. All versions of Windows contain the vulnerable code and are susceptible to exploitation.
“A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations,” Microsoft said in its advisory. “An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
“An attack must involve an authenticated user calling RpcAddPrinterDriverEx(),” the Redmond-based firm added. When reached by The Hacker News, the company said it had nothing to share beyond the advisory.
The acknowledgment comes after researchers from Hong Kong-based cybersecurity company Sangfor published a technical deep-dive of a Print Spooler RCE flaw to GitHub, along with a fully working PoC code, before it was taken down just hours after it went up.
The disclosures also set off speculation and debate about whether the June patch does or does not protect against the RCE vulnerability, with the CERT Coordination Center noting that “while Microsoft has released an update for CVE-2021-1675, it is important to realize that this update does NOT protect Active Directory domain controllers, or systems that have Point and Print configured with the NoWarningNoElevationOnInstall option configured.”
CVE-2021-1675, originally classified as an elevation of privilege vulnerability and later revised to RCE, was remediated by Microsoft on June 8, 2021.
The company, in its advisory, noted that PrintNightmare is distinct from CVE-2021-1675 for reasons that the latter resolves a separate vulnerability in RpcAddPrinterDriverEx() and that the attack vector is different.
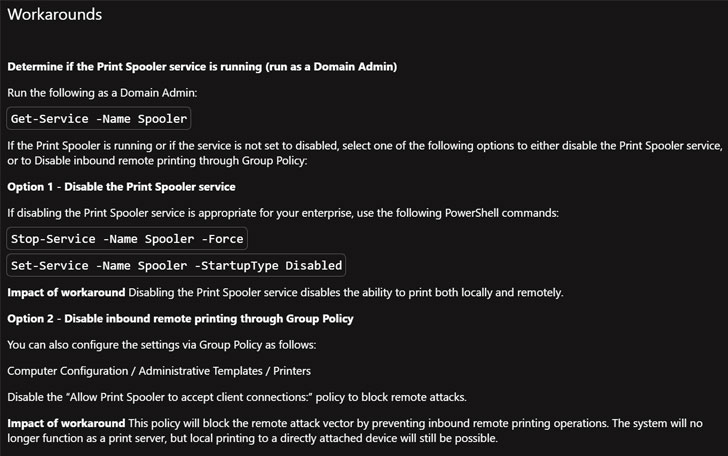
As workarounds, Microsoft is recommending users to disable the Print Spooler service or turn off inbound remote printing through Group Policy. To reduce the attack surface and as an alternative to completely disabling printing, the company is also advising to check membership and nested group membership, and reduce membership as much as possible, or completely empty the groups where possible.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C