NoxPlayer Supply-Chain Attack is Likely the Work of Gelsemium Hackers
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
A new cyber espionage group named Gelsemium has been linked to a supply chain attack targeting the NoxPlayer Android emulator that was disclosed earlier this year.
The findings come from a systematic analysis of multiple campaigns undertaken by the APT crew, with evidence of the earliest attack dating back all the way to 2014 under the codename Operation TooHash based on malware payloads deployed in those intrusions.
“Victims of these campaigns are located in East Asia as well as the Middle East and include governments, religious organizations, electronics manufacturers and universities,” cybersecurity firm ESET said in an analysis published last week.
“Gelsemium’s whole chain might appear simple at first sight, but the exhaustive configurations, implanted at each stage, modify on-the-fly settings for the final payload, making it harder to understand.”
Targeted countries include China, Mongolia, North and South Korea, Japan, Turkey, Iran, Iraq, Saudi Arabia, Syria, and Egypt.
Since its origins in the mid-2010s, Gelsemium has been found employing a variety of malware delivery techniques ranging from spear-phishing documents exploiting Microsoft Office vulnerabilities (CVE-2012-0158) and watering holes to a remote code execution flaw in Microsoft Exchange Server — likely CVE-2020-0688, which was addressed by the Windows maker in June 2020 — to deploy the China Chopper web shell.
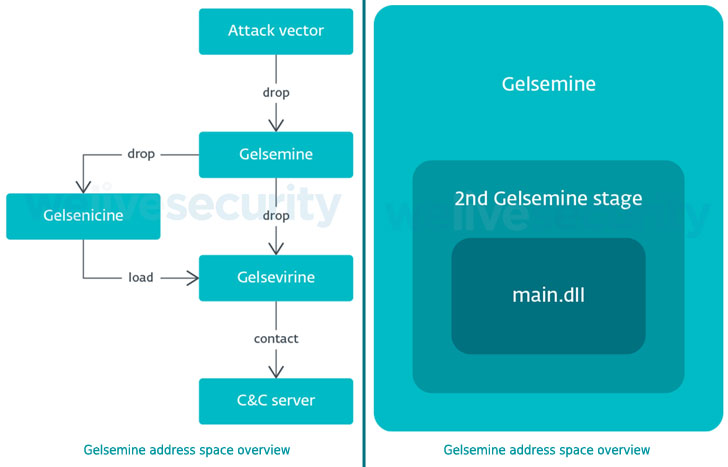
According to ESET, Gelsemium’s first stage is a C++ dropper named “Gelsemine,” which deploys a loader “Gelsenicine” onto the target system, which, in turn, retrieves and executes the main malware “Gelsevirine” that’s capable of loading additional plug-ins provided by the command-and-control (C2) server.
The adversary is said to have been behind a supply chain attack aimed at BigNox’s NoxPlayer, in a campaign dubbed “Operation NightScout,” in which the software’s update mechanism was compromised to install backdoors such asGh0st RATandPoisonIvy RAT to spy on its victims, capture keystrokes, and gather valuable information.
“Victims originally compromised by that supply chain attack were later being compromised by Gelsemine,” ESET researchers Thomas Dupuy and Matthieu Faou noted, with similarities observed between the trojanized versions of NoxPlayer and Gelsemium malware.
What’s more, another backdoor called Chrommme, which was detected on an unnamed organization’s machine also compromised by the Gelsemium group, used the same C2 server as that of Gelsevirine, raising the possibility that the threat actor may be sharing the attack infrastructure across its malware toolset.
“The Gelsemium biome is very interesting: it shows few victims (according to our telemetry) with a vast number of adaptable components,” the researchers concluded. “The plug-in system shows that developers have deep C++ knowledge.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C