Critical Flaws Uncovered in Pentaho Business Analytics Software
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
Multiple vulnerabilities have been disclosed in Hitachi Vantara’s Pentaho Business Analytics software that could be abused by malicious actors to upload arbitrary data files and even execute arbitrary code on the underlying host system of the application.
The security weaknesses were reported by researchers Alberto Favero from German cybersecurity firm Hawsec and Altion Malka from Census Labs earlier this year, prompting the company to issue necessary patches to address the issues.
Pentaho is a Java-based business intelligence platform that offers data integration, analytics, online analytical processing (OLAP), and mining capabilities, and counts major companies and organizations like Bell, CERN, Cipal, Logitech, Nasdaq, Telefonica, Teradata, and the National September 11 Memorial and Museum among its customers.
The list of flaws, which affect Pentaho Business Analytics versions 9.1 and lower, is as follows -
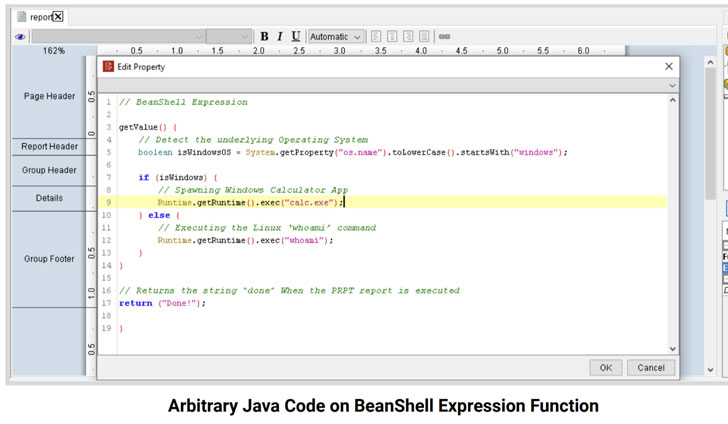
- CVE-2021-31599 (CVSS score: 9.9) - Remote Code Execution through Pentaho Report Bundles
- CVE-2021-31600 (CVSS score: 4.3) - Jackrabbit User Enumeration
- CVE-2021-31601 (CVSS score: 7.1) - Insufficient Access Control of Data Source Management
- CVE-2021-31602 (CVSS score: 5.3) - Authentication Bypass of Spring APIs
- CVE-2021-34684 (CVSS score: 9.8) - Unauthenticated SQL Injection
- CVE-2021-34685 (CVSS score: 2.7) - Bypass of Filename Extension Restrictions
Successful exploitation of the flaws could allow authenticated users with sufficient role permissions to upload and run Pentaho Report Bundles to run malicious code on the host server and exfiltrate sensitive application data, and circumvent filename extension restrictions enforced by the application and upload files of any type.
What’s more, they could also be leveraged by a low-privilege authenticated attacker to retrieve credentials and connection details of all Pentaho data sources, permitting the party to harvest and transmit data, in addition to enabling an unauthenticated user to execute arbitrary SQL queries on the backend database and retrieve data.
In light of the critical nature of the flaws and the risk they pose to the underlying system, users of the application are highly recommended to update to the latest version.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P