New APT Hacking Group Targets Microsoft IIS Servers with ASP.NET Exploits
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
A new highly capable and persistent threat actor has been targeting major high-profile public and private entities in the U.S. as part of a series of targeted cyber intrusion attacks by exploiting internet-facing Microsoft Internet Information Services (IIS) servers to infiltrate their networks.
Israeli cybersecurity firm Sygnia, which identified the campaign, is tracking the advanced, stealthy adversary under the moniker “Praying Mantis” or “TG2021.”
“TG1021 uses a custom-made malware framework, built around a common core, tailor-made for IIS servers. The toolset is completely volatile, reflectively loaded into an affected machine’s memory and leaves little-to-no trace on infected targets,” the researchers said. “The threat actor also uses an additional stealthy backdoor and several post-exploitations modules to perform network reconnaissance, elevate privileges, and move laterally within networks.”
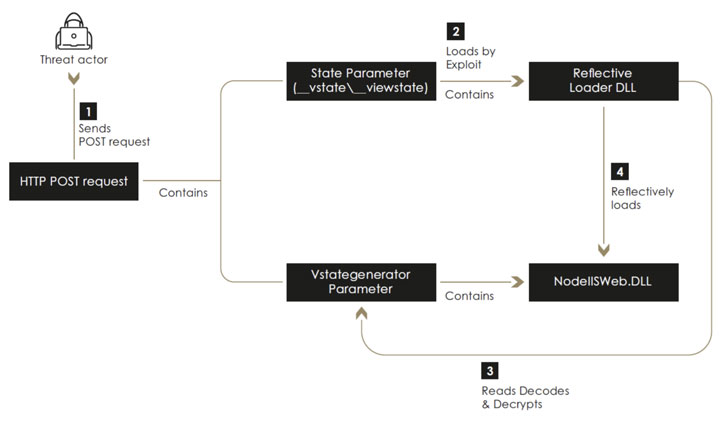
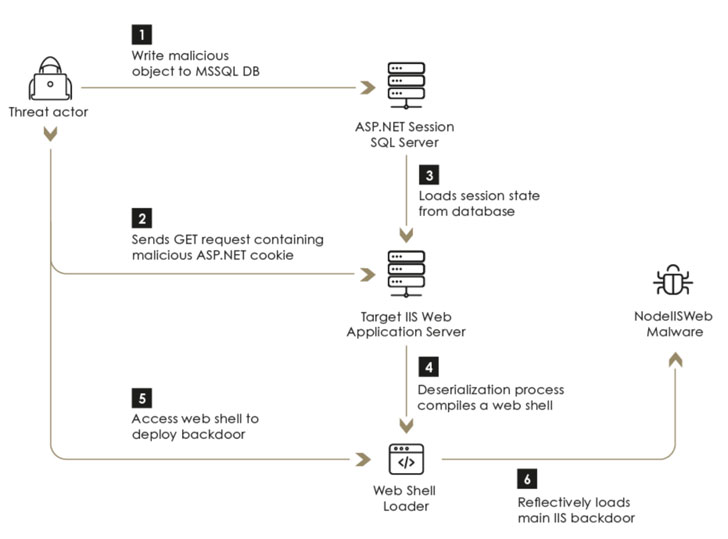
Besides exhibiting capabilities that show a significant effort to avoid detection by actively interfering with logging mechanisms and successfully evading commercial endpoint detection and response (EDR) systems, the threat actor has been known to leverage an arsenal of ASP.NET web application exploits to gain an initial foothold and backdoor the servers by executing a sophisticated implant named “NodeIISWeb” that’s designed to load custom DLLs as well as intercept and handle HTTP requests received by the server.
The vulnerabilities that are taken advantage of by the actor include:
- Checkbox Survey RCE Exploit (CVE-2021-27852)
- VIEWSTATE Deserialization Exploit
- Altserialization Insecure Deserialization
- Telerik-UI Exploit (CVE-2019-18935 and CVE-2017-11317)
Interestingly, Sygnia’s investigation into TG1021’s tactics, techniques, and procedures (TTPs) have unearthed “major overlaps” to those of a nation-sponsored actor named “Copy-Paste Compromises,” as detailed in an advisory released by the Australian Cyber Security Centre (ACSC) in June 2020, which described a cyber campaign targeting public-facing infrastructure primarily through the use of unpatched flaws in Telerik UI and IIS servers. However, a formal attribution is yet to be made.
“Praying Mantis, which has been observed targeting high-profile public and private entities in two major Western markets, exemplifies a growing trend of cyber criminals using sophisticated, nation-state attack methods to target commercial organizations,” the researchers said. “Continuous forensics activities and timely incident response are essential to identifying and effectively defending networks from attacks by similar threat actors.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P