F5 BIG-IP Found Vulnerable to Kerberos KDC Spoofing Vulnerability
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
Cybersecurity researchers on Wednesday disclosed a new bypass vulnerability (CVE-2021-23008) in the Kerberos Key Distribution Center (KDC) security feature impacting F5 Big-IP application delivery services.
“The KDC Spoofing vulnerability allows an attacker to bypass the Kerberos authentication to Big-IP Access Policy Manager (APM), bypass security policies and gain unfettered access to sensitive workloads,” Silverfort researchers Yaron Kassner and Rotem Zach said in a report. “In some cases this can be used to bypass authentication to the Big-IP admin console as well.”
Coinciding with the public disclosure, F5 Networks has released patches to address the weakness (CVE-2021-23008, CVSS score 8.1), with fixes introduced in BIG-IP APM versions 12.1.6, 13.1.4, 14.1.4, and 15.1.3. A similar patch for version 16.x is expected at a future date.
“We recommend customers running 16.x check the security advisory to assess their exposure and get details on mitigations for the vulnerability,” F5 told The Hacker News via email. As workarounds, the company recommends configuring multi-factor authentication (MFA), or deploying an IPSec tunnel between the affected BIG-IP APM system and the Active Directory servers.
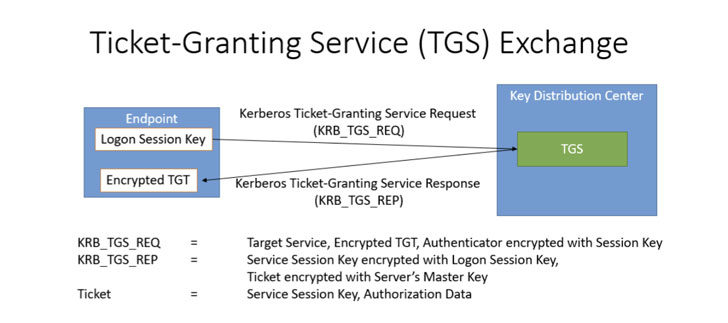
Kerberos is an authentication protocol that relies on a client-server model for mutual authentication and requires a trusted intermediary called Key Distribution Center (KDC) — a Kerberos Authentication Server (AS) or a Ticket Granting Server in this case — that acts as a repository of shared secret keys of all users as well as information about which users have access privileges to which services on which network servers.
Thus when a user, say Alice, wants to access a particular service on a server (Bob), Alice is prompted to provide her username and password to verify her identity, after which the AS checks if Alice has access privileges to Bob, and if so, issue a “ticket” permitting the user to use the service until its expiration time.
Also essential as part of the process is the authentication of KDC to the server, in the absence of which the security of the Kerberos gets compromised, thus allowing an attacker that has the ability to hijack the network communication between Big-IP and the domain controller (which is the KDC) to sidestep the authentication entirely.
In a nutshell, the idea is that when the Kerberos protocol is implemented the right way, an adversary attempting to impersonate the KDC cannot bypass the authentication protections. The spoofing attack, therefore, hinges on the possibility that there exist insecure Kerberos configurations so as to hijack the communication between the client and the domain controller, leveraging it to create a fraudulent KDC that diverts the traffic intended for the controller to the fake KDC, and subsequently authenticate itself to the client.
“A remote attacker can hijack a KDC connection using a spoofed AS-REP response,” F5 Networks noted in the alert. “For an APM access policy configured with AD authentication and SSO (single sign-on) agent, if a spoofed credential related to this vulnerability is used, depending how the back-end system validates the authentication token it receives, access will most likely fail. An APM access policy can also be configured for BIG-IP system authentication. A spoofed credential related to this vulnerability for an administrative user through the APM access policy results in local administrative access.”
This is the fourth such spoofing flaw uncovered by Silverfort after discovering similar issues in Cisco ASA (CVE-2020-3125), Palo Alto Networks PAN-OS (CVE-2020-2002), and IBM QRadar (CVE-2019-4545) last year.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P