Multiple Botnets Exploiting Critical Oracle WebLogic Bug — PATCH NOW
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
Multiple botnets are targeting thousands of publicly exposed and still unpatched Oracle WebLogic servers to deploy crypto miners and steal sensitive information from infected systems.
The attacks are taking aim at a recently patched WebLogic Server vulnerability, which was released by Oracle as part of its October 2020 Critical Patch Update and subsequently again in November (CVE-2020-14750) in the form of an out-of-band security patch.
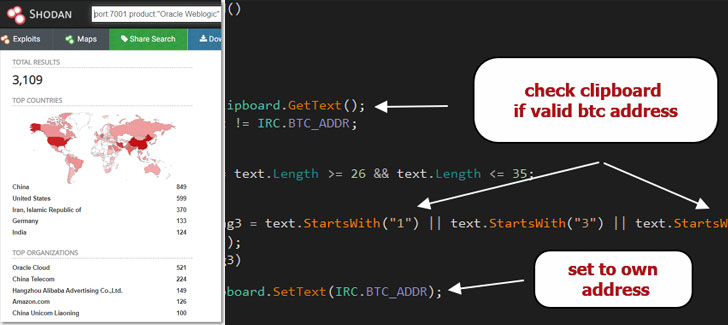
As of writing, about 3,000 Oracle WebLogic servers are accessible on the Internet-based on stats from the Shodan search engine.
Oracle WebLogic is a platform for developing, deploying, and running enterprise Java applications in any cloud environment as well as on-premises.
The flaw, which is tracked as CVE-2020-14882, has a CVSS score of 9.8 out of a maximum rating of 10 and affects WebLogic Server versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0.
Although the issue has been addressed, the release of proof-of-concept exploit code has made vulnerable Oracle WebLogic instances a lucrative target for threat actors to recruit these servers into a botnet that pilfers critical data and deploy second stage malware payloads.
According to Juniper Threat Labs, operators of the DarkIRC botnet are exploiting this RCE vulnerability to spread laterally across the network, download files, record keystrokes, steal credentials, and execute arbitrary commands on compromised machines.
The malware also acts as a Bitcoin clipper that allows them to change bitcoin wallet addresses copied to the clipboard to the operator’s bitcoin wallet address, allowing the attackers to reroute Bitcoin transactions.
What’s more, a threat actor by the name of “Freak_OG” has been selling the DarkIRC malware currently on hacking forums for $75 since August.
But it’s not just DarkIRC that’s exploiting the WebLogic Server vulnerability. In a separate campaign—spotted by ‘0xrb’ and detailed by researcher Tolijan Trajanovski—evidence has emerged of a botnet that propagates via the WebLogic flaw to deliver Monero cryptocurrency miner and Tsunami binaries.
Besides using SSH for lateral movement, the botnet has been found to achieve persistence through cron jobs, kill competing mining tools, and even uninstall Endpoint detection and response (EDR) tools from Alibaba and Tencent.
It’s recommended that users apply the October 2020 Critical Patch Update and the updates associated with CVE-2020-14750 as soon as possible to mitigate risks stemming from this flaw.
Oracle has also provided instructions to harden the servers by preventing external access to internal applications accessible on the Administration port.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C