New Argo CD Bug Could Let Hackers Steal Secret Info from Kubernetes Apps
7.7 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N
4 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
SINGLE
Confidentiality Impact
PARTIAL
Integrity Impact
NONE
Availability Impact
NONE
AV:N/AC:L/Au:S/C:P/I:N/A:N
Users of the Argo continuous deployment (CD) tool for Kubernetes are being urged to push through updates after a zero-day vulnerability was found that could allow an attacker to extract sensitive information such as passwords and API keys.
The flaw, tagged as CVE-2022-24348 (CVSS score: 7.7), affects all versions and has been addressed in versions 2.3.0, 2.2.4, and 2.1.9. Cloud security firm Apiiro has been credited with discovering and reporting the bug on January 30, 2022s.
Continuous deployment, also called continuous delivery, refers to a process that automatically deploys all code changes to the testing and/or production environment after they are tested and merged to a shared repository.
Argo CD is officially used by 191 organizations, including Alibaba Group, BMW Group, Deloitte, Gojek, IBM, Intuit, LexisNexis, Red Hat, Skyscanner, Swisscom, and Ticketmaster.
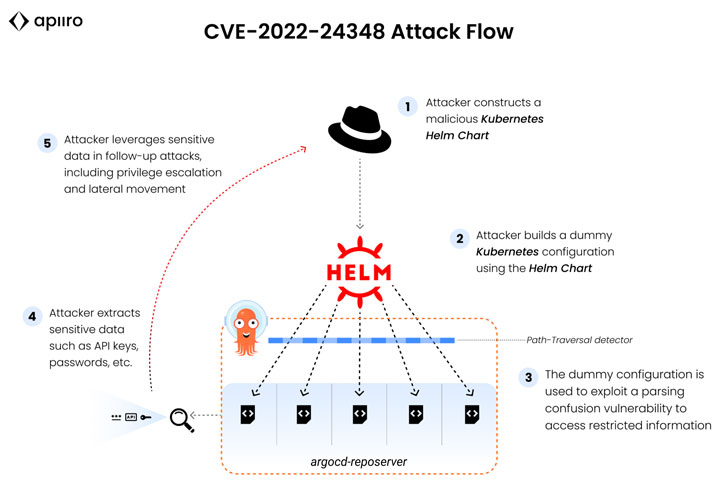
The path-traversal vulnerability “allows malicious actors to load a Kubernetes Helm Chart YAML file to the vulnerability and ‘hop’ from their application ecosystem to other applications’ data outside of the user’s scope,” Moshe Zioni, Apiiro’s VP of security research, said.
Bad actors can exploit the vulnerability by loading a malicious Kubernetes Helm Chart YAML file, a package manager which specifies a collection of Kubernetes resources required to deploy an application, onto the target system, allowing the retrieval of confidential information from other apps.
Successful exploitation of the defect could have serious consequences ranging from privilege escalation and sensitive information disclosure to lateral movement attacks and exfiltrate tokens from other applications.
Software supply chain has emerged as a major security threat in the wake of attacks exploiting SolarWinds, Kaseya, and Log4j in recent years. In July 2021, Intezer disclosed that attackers are taking advantage of misconfigured Argo Workflows instances to drop cryptominers onto Kubernetes (K8s) clusters.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.7 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N
4 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
SINGLE
Confidentiality Impact
PARTIAL
Integrity Impact
NONE
Availability Impact
NONE
AV:N/AC:L/Au:S/C:P/I:N/A:N