How Heartbleed Bug Exposes Your Passwords to Hackers
0.975 High
EPSS
Percentile
100.0%
Are you safe from the critical bug Heartbleed?? OpenSSL- the encryption technology used by millions of websites to encrypt the communication and is also used to protect our sensitive data such as e-mails, passwords or banking information.
But a tiny, but most critical flaw called “Heartbleed” in the widely used OpenSSL opened doors for the cyber criminals to extract sensitive data from the system memory.
WHAT IS HEARTBLEED?
SSL and TLS are known to provide communication security and privacy over the Internet for applications such as websites, email, instant messaging (IM), including some virtual private networks (VPNs).
Heartbleed is a critical bug (CVE-2014-0160) is in the popular OpenSSL cryptographic software library, that actually resides in the OpenSSL’s implementation of the TLS (transport layer security protocols) and DTLS (Datagram TLS) heartbeat extension (RFC6520).
This bug was independently discovered by a team of security engineers (Riku, Antti and Matti) at Codenomicon, while improving the SafeGuard feature in Codenomicon’s Defensics security testing tools, and Neel Mehta of Google Security, who first reported it to the OpenSSL team.
Software vulnerabilities may come and go, but this bug is more critical as it has left the large number of private keys and other secrets exposed to the Internet. The heartbleed bug can reveal the contents of a server’s memory, where the most sensitive data is stored, including the private data such as usernames, passwords, and credit card numbers.
This could allow attackers to retrieve private keys and ultimately decrypt the server’s encrypted traffic or even impersonate the server.
> “The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users.”
HEARTBLEED WORLDWIDE****IMPACT
OpenSSL is most widely used cryptographic library for Apache and nginx Web servers, which handles a service of Transport Layer Security (TLS) called Heartbeat, an extension added to TLS in 2012. The combined market share of just those two, Apache and nginx, out of the active sites on the Internet is over 66% according to Netcraft’s April 2014 Web Server Survey.
Moreover, OpenSSL is used to protect email servers (SMTP, POP and IMAP protocols), chat servers (XMPP protocol), virtual private networks (SSL VPNs), network appliances and wide variety of client side software. Many large consumer sites are also saved by their conservative choice of SSL/TLS termination equipment and software. OpenSSL is also very popular in client software and somewhat popular in networked appliances which have most inertia in getting updates.
Security researcher 'Robert Graham’ scanned the Internet and found that more than 600,000 servers are vulnerable to heartbleed flaw, including Yahoo.com, imgur.com, flickr.com, hidemyass.com. [List]
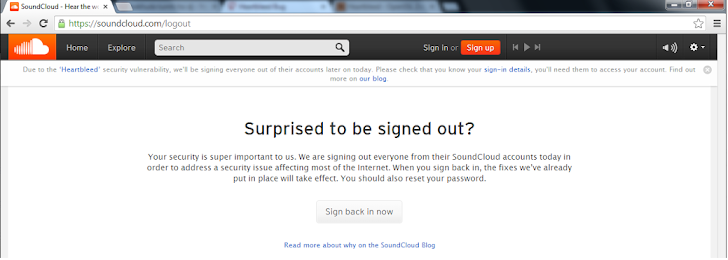
Because of Heartbleed bug, the Canada Revenue Agency was forced to shut down its electronic tax collection service yesterday and apparently, World’s biggest audio platform SoundCloud also logged out its users for fixing this flaw.
Yahoo, which has more than 800 million users around the world, also has been exposed by the bug.
** ** HOW HEARTBLEED WORKS?
It is not a problem with the TLS/SSL technologies that encrypt the Internet, neither with how OpenSSL works. It is just a dumb coding mistake.
Using Heartbeats extension two computers make sure the other is still alive by sending data back and forth to each other. The client (user) sends its heartbeat to the server (website), and the server hands it right back. If by chance anyone of them goes down during the transaction, the other one will know using heartbeat sync mechanism.
When that heartbeat is sent, a small amount of the server’s short-term memory of about 64 kilobytes comes in reply from server and an attacker is supposed to grab it, that can leak sensitive data such as message contents, user credentials, session keys and server private keys. By sending heartbleed requests multiple times, an attacker is able to fetch more memory contents from the server.
This means, everything and anything in the memory such as SSL private keys, user keys used for your usernames and passwords, instant messages, emails and business critical documents and communication, and many more is vulnerable to cyber criminals. At this phase, you have to assume that it is all compromised.
About two-thirds of web servers rely on OpenSSL, means the information passing through hundreds of thousands of websites could be vulnerable.
So far, Security experts have found no direct evidence that anyone has managed to use the bug to steal information. The vulnerability has been fixed in OpenSSL v1.0.1g.
Major websites, including Gmail and YouTube, Facebook, Tumblr, Yahoo and Dropbox have fixed the problem, but there are still thousands of websites who are yet to fix the problem. Users are advised to change their passwords on only those affected websites, that tell you they’ve fixed the problem. READ MORE on how to protect yourself from Heartbleed bug.
Related Important Articles: