Adobe Releases Critical Security Updates for Acrobat, Reader and Photoshop CC
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
0.022 Low
EPSS
Percentile
88.3%
Adobe has just released new versions of its Acrobat DC, Reader and Photoshop CC for Windows and macOS users that patch 48 vulnerabilities in its software.
A total of 47 vulnerabilities affect Adobe Acrobat and Reader applications, and one critical remote code execution flaw has been patched in Adobe Photoshop CC.
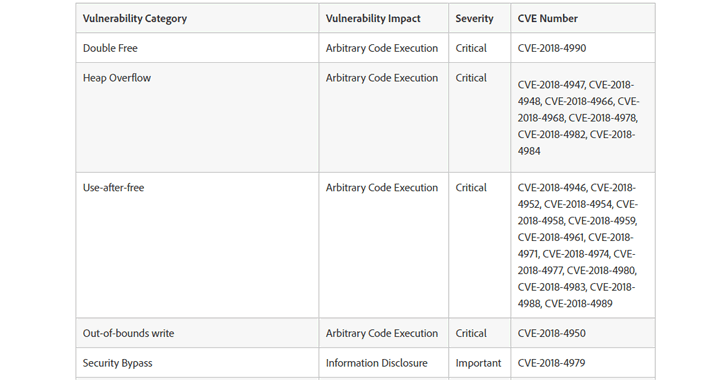
Out of 47, Adobe Acrobat and Reader affect with 24 critical vulnerabilities—categorized as Double Free, Heap Overflow, Use-after-free, Out-of-bounds write, Type Confusion, and Untrusted pointer dereference—which if exploited, could allow arbitrary code execution in the context of the targeted user.
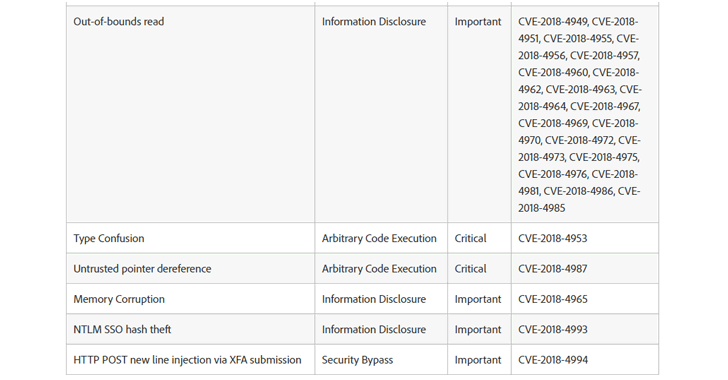
Rest of the 23 flaws, including Security Bypass, Out-of-bounds read, Memory Corruption, NTLM SSO hash theft, and HTTP POST newline injection via XFA submission, are marked as important and can lead to information disclosure or security bypass.
The above-listed vulnerabilities impact the Windows and macOS versions of Acrobat DC (Consumer and Classic 2015), Acrobat Reader DC (Consumer and Classic 2015), Acrobat 2017, and Acrobat Reader 2017.
The latest Adobe Acrobat and Reader patches have been given a priority rating of “1,” which means the flaws are either being exploited in the wild or more likely to be exploited in the wild. So, users are highly recommended to update their software as soon as possible.
The flaws have been addressed in Acrobat DC and Acrobat Reader DC version 2018.011.20040, Acrobat 2017 and Acrobat Reader DC 2017 version 2017.011.30080, as well as Acrobat Reader DC (Classic 2015) and Acrobat DC (Classic 2015) version 2015.006.30418.
Security Patch for Adobe Photoshop CC
Adobe has also released security patches for the Windows and macOS versions of Photoshop CC to address a critical vulnerability, categorized as “out-of-bounds write” issue, which can be exploited to execute arbitrary code in the context of the current user.
The vulnerability (CVE-2018-4946) impacts Photoshop CC 2018 version 19.1.3 and earlier 19.x versions, as well as Photoshop CC 2017 version 18.1.3 and earlier 18.x versions.
The company credited researcher Giwan Go of Trend Micro’s Zero Day Initiative for reporting the flaw, which has been addressed with the release of Photoshop CC 2018 version 19.1.4 and Photoshop CC 2017 version 18.1.4.
This update has been given a priority rating of “3,” which means the attackers have not targeted the vulnerability.
Adobe recommends end users and administrators to install the latest security updates as soon as possible.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
0.022 Low
EPSS
Percentile
88.3%