BlackByte Ransomware Abuses Vulnerable Windows Driver to Disable Security Solutions
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
7.2 High
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:L/AC:L/Au:N/C:C/I:C/A:C
In yet another case of bring your own vulnerable driver (BYOVD) attack, the operators of the BlackByte ransomware are leveraging a flaw in a legitimate Windows driver to bypass security solutions.
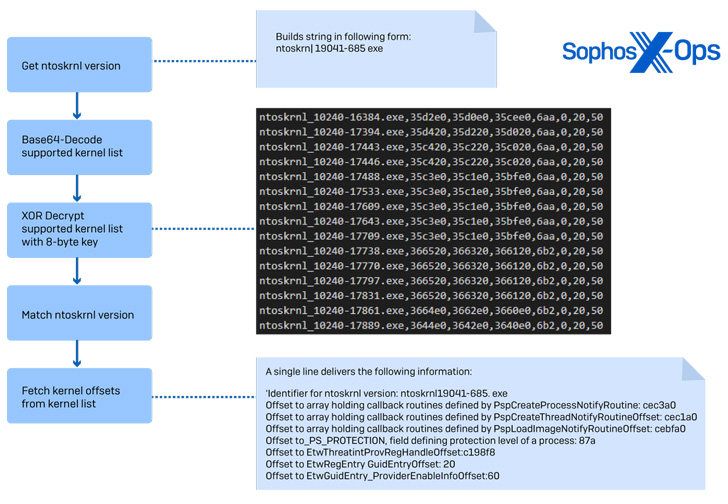
“The evasion technique supports disabling a whopping list of over 1,000 drivers on which security products rely to provide protection,” Sophos threat researcher Andreas Klopsch said in a new technical write-up.
BYOVD is an attack technique that involves threat actors abusing vulnerabilities in legitimate, signed drivers to achieve successful kernel-mode exploitation and seize control of compromised machines.
Weaknesses in signed drivers have been increasingly co-opted by nation-state threat groups in recent years, including Slingshot, InvisiMole, APT28, and most recently, the Lazarus Group.
BlackByte, believed to be an offshoot of the now-discontinued Conti group, is part of the big game cybercrime crews, which zeroes in on large, high-profile targets as part of its ransomware-as-a-service (RaaS) scheme.
According to the cybersecurity firm, recent attacks mounted by the group have taken advantage of a privilege escalation and code execution flaw (CVE-2019-16098, CVSS score: 7.8) affecting the Micro-Star MSI Afterburner RTCore64.sys driver to disable security products.
What’s more, an analysis of the ransomware sample has uncovered multiple similarities between the EDR bypass implementation and that of a C-based open source tool called EDRSandblast, which is designed to abuse vulnerable signed drivers to evade detection.
BlackByte is the latest ransomware family to embrace the BYOVD method to achieve its goals, after RobbinHood and AvosLocker, both of which have weaponized bugs in gdrv.sys (CVE-2018-19320) and asWarPot.sys to terminate processes associated with endpoint protection software.
To protect against BYOVD attacks, it’s recommended to keep track of the drivers installed on the systems and ensure they are up-to-date, or opt to blocklist drivers known to be exploitable.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
7.2 High
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:L/AC:L/Au:N/C:C/I:C/A:C