New 'Retbleed' Speculative Execution Attack Affects AMD and Intel CPUs
5.6 Medium
CVSS3
Attack Vector
LOCAL
Attack Complexity
HIGH
Privileges Required
LOW
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.1/AV:L/AC:H/PR:L/UI:N/S:C/C:H/I:N/A:N
1.9 Low
CVSS2
Access Vector
LOCAL
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
NONE
Availability Impact
NONE
AV:L/AC:M/Au:N/C:P/I:N/A:N
Security researchers have uncovered yet another vulnerability affecting numerous older AMD and Intel microprocessors that could bypass current defenses and result in Spectre-based speculative-execution attacks.
Dubbed Retbleed by ETH Zurich researchers Johannes Wikner and Kaveh Razavi, the issue is tracked as CVE-2022-29900 (AMD) and CVE-2022-29901 (Intel), with the chipmakers releasing software mitigations as part of a coordinated disclosure process.
Retbleed is also the latest addition to a class of Spectre attacks known as Spectre-BTI (CVE-2017-5715 or Spectre-V2), which exploit the side effects of an optimization technique called speculative execution by means of a timing side channel to trick a program into accessing arbitrary locations in its memory space and leak private information.
Speculative execution attempts to fill the instruction pipeline of a program by predicting which instruction will be executed next in order to gain a performance boost, while also undoing the results of the execution should the guess turn out to be wrong.
Attacks like Spectre take advantage of the fact that these erroneously executed instructions — a result of the misprediction — are bound to leave traces of the execution in the cache, resulting in a scenario where a rogue program can trick the processor into executing incorrect code paths and infer secret data pertaining to the victim.
Put differently, Spectre is an instance of transient execution attack, which relies on hardware design flaws to “influence” which instruction sequences are speculatively executed and leak encryption keys or passwords from within the victim’s memory address space.
This, in turn, is achieved through microarchitectural side channels like Flush+Reload that measures the time taken to perform memory reads from the cache that’s shared with the victim, but not before flushing some of the shared memory, resulting in either fast or slow reads depending on whether the victim accessed the monitored cache line since it was evicted.
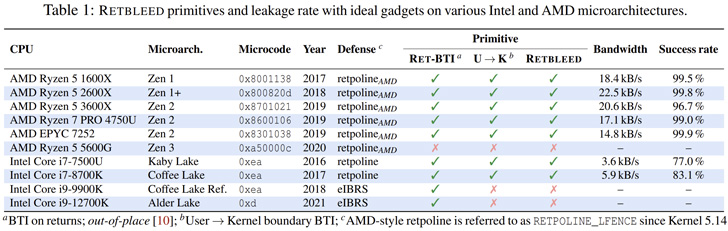
While safeguards like Retpoline (aka “return trampoline”) have been devised to prevent branch target injection (BTI), Retbleed is designed to get around this countermeasure and achieve speculative code execution.
“Retpolines work by replacing indirect jumps [branches where the branch target is determined at runtime] and calls with returns,” the researchers explained.
“Retbleed aims to hijack a return instruction in the kernel to gain arbitrary speculative code execution in the kernel context. With sufficient control over registers and/or memory at the victim return instruction, the attacker can leak arbitrary kernel data.”
The core idea, in a nutshell, is to treat return instructions as an attack vector for speculation execution and force the statements to be predicted like indirect branches, effectively undoing protections offered by Retpoline.
As a new line of defense, AMD has introduced what’s referred to as Jmp2Ret, while Intel has recommended using enhanced Indirect Branch Restricted Speculation (eIBRS) to address the potential vulnerability even if Retpoline mitigations are in place.
“Windows operating system uses IBRS by default, so no update is required,” Intel said in an advisory, noting it worked with the Linux community to make available software updates for the shortcoming.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
5.6 Medium
CVSS3
Attack Vector
LOCAL
Attack Complexity
HIGH
Privileges Required
LOW
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.1/AV:L/AC:H/PR:L/UI:N/S:C/C:H/I:N/A:N
1.9 Low
CVSS2
Access Vector
LOCAL
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
NONE
Availability Impact
NONE
AV:L/AC:M/Au:N/C:P/I:N/A:N