PoC Released for Outlook Flaw that Microsoft Patched 6 Month After Discovery
5.4 Medium
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
REQUIRED
Scope
CHANGED
Confidentiality Impact
LOW
Integrity Impact
LOW
Availability Impact
NONE
CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N
3.5 Low
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
SINGLE
Confidentiality Impact
NONE
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:M/Au:S/C:N/I:P/A:N
0.001 Low
EPSS
Percentile
18.7%
As we reported two days ago, Microsoft this week released an updated version of its Outlook app for Android that patches a severe remote code execution vulnerability (CVE-2019-1105) that impacted over 100 million users.
However, at that time, very few details of the flaw were available in the advisory, which just revealed that the earlier versions of the email app contained a cross-site scripting (XSS) flaw that could allow attackers to run scripts in the context of the current user just by sending a specially crafted email to the victims.
Now, Bryan Appleby from F5 Networks, one of the security researchers who reported this issue independently to Microsoft, released more details and proof-of-concept for the Outlook vulnerability that he reported to the tech giant almost six months ago.
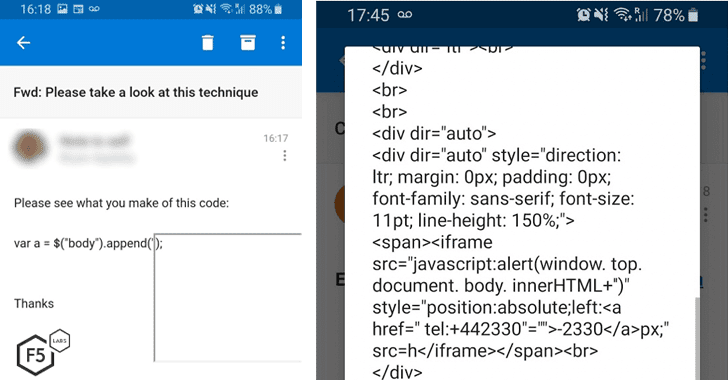
In a blog post published Friday, Appleby revealed that while exchanging some JavaScript code with his friends over an email, he accidentally discovered a cross-site scripting (XSS) issue that could allow an attacker to embed an iframe into the email.
In other words, the vulnerability resided in the way email server parses HTML entities in the email messages.
Though JavaScript running inside an iframe can only access the content within it, Appleby found that executing JavaScript code inside the injected iframe can allow the attacker to read app-related content in the context of logged-in Outlook user, including their cookies, tokens and even some contents of their email inbox.
The vulnerability, Appleby said, allowed him to “steal data from the app—I could use it to read and extract the HTML.”
> “This kind of vulnerability could be exploited by an attacker sending an email with JavaScript in it. The server escapes that JavaScript and does not see it because it’s within an iframe. When delivered, the mail client automatically undoes the escaping, and the JavaScript runs on the client device. Bingo – remote code execution,” Appleby explains.
> “This code can do whatever the attacker desires, up to and including stealing information and/or sending data back out. An attacker can send you an email and just by you reading it, they could steal the contents of your inbox. Weaponized, this can turn into a very nasty piece of malware.”
Appleby responsibly reported his findings to Microsoft on 10 December 2018, and the company confirmed the vulnerability on 26 March 2019 when he shared a universal PoC with the tech giant.
Microsoft patched the vulnerability and released a fix just 2 days ago—that’s almost 6 months after the initial vulnerability disclosure. The company says it is currently not aware of any attacks in the wild related to this issue.
Besides Appleby, security researchers Sander Vanrapenbusch, Tom Wyckhuys, Eliraz Duek from CyberArk and Gaurav Kumar also reported the same issue to Microsoft separately in recent months.
Gaurav Kumar also shared a video with The Hacker News that demonstrates the vulnerability in action, as shown above.
Once again, if your Android device is not yet updated automatically, you are advised to update your Outlook app from Google Play Store manually.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
5.4 Medium
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
REQUIRED
Scope
CHANGED
Confidentiality Impact
LOW
Integrity Impact
LOW
Availability Impact
NONE
CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N
3.5 Low
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
SINGLE
Confidentiality Impact
NONE
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:M/Au:S/C:N/I:P/A:N
0.001 Low
EPSS
Percentile
18.7%