New UnRAR Vulnerability Could Let Attackers Hack Zimbra Webmail Servers
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
HIGH
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:L/Au:N/C:N/I:P/A:N
A new security vulnerability has been disclosed in RARlab’s UnRAR utility that, if successfully exploited, could permit a remote attacker to execute arbitrary code on a system that relies on the binary.
The flaw, assigned the identifier CVE-2022-30333, relates to a path traversal vulnerability in the Unix versions of UnRAR that can be triggered upon extracting a maliciously crafted RAR archive.
Following responsible disclosure on May 4, 2022, the shortcoming was addressed by RarLab as part of version 6.12 released on May 6. Other versions of the software, including those for Windows and Android operating systems, are not impacted.
“An attacker is able to create files outside of the target extraction directory when an application or victim user extracts an untrusted archive,” SonarSource researcher Simon Scannell said in a Tuesday report. “If they can write to a known location, they are likely to be able to leverage it in a way leading to the execution of arbitrary commands on the system.”
It’s worth pointing out that any software that utilizes an unpatched version of UnRAR to extract untrusted archives is affected by the flaw.
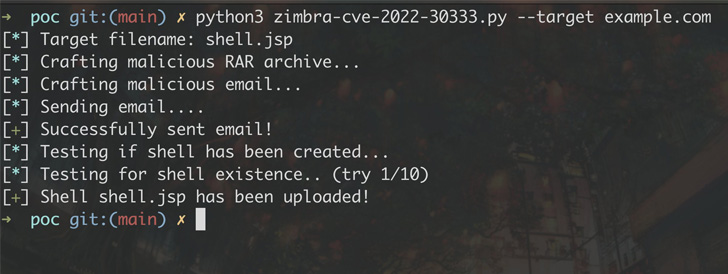
This also includes Zimbra collaboration suite, wherein the vulnerability could lead to pre-authenticated remote code execution on a vulnerable instance, giving the attacker complete access to an email server and even abuse it to access or overwrite other internal resources within the organization’s network.
Image Source: Simon Scannell
The vulnerability, at its heart, relates to a symbolic link attack in which a RAR archive is crafted such that it contains a symlink that’s a mix of both forward slashes and backslashes (e.g., “…\…\…\tmp/shell”) so as to bypass current checks and extract it outside of the expected directory.
More specifically, the weakness has to do with a function that’s designed to convert backslashes (‘') to forward slashes (’/') so that a RAR archive created on Windows can be extracted on a Unix system, effectively altering the aforementioned symlink to “…/…/…/tmp/shell.”
By taking advantage of this behavior, an attacker can write arbitrary files anywhere on the target filesystem, including creating a JSP shell in Zimbra’s web directory and execute malicious commands.
“The only requirement for this attack is that UnRAR is installed on the server, which is expected as it is required for RAR archive virus-scanning and spam-checking,” Scannell noted.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.5 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
HIGH
Availability Impact
NONE
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N
5 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:L/Au:N/C:N/I:P/A:N