Hackers Exploit Zero-Day Bugs in Draytek Devices to Target Enterprise Networks
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
Cybersecurity researchers with Qihoo 360’s NetLab today unveiled details of two recently spotted zero-day cyberattack campaigns in the wild targeting enterprise-grade networking devices manufactured by Taiwan-based DrayTek.
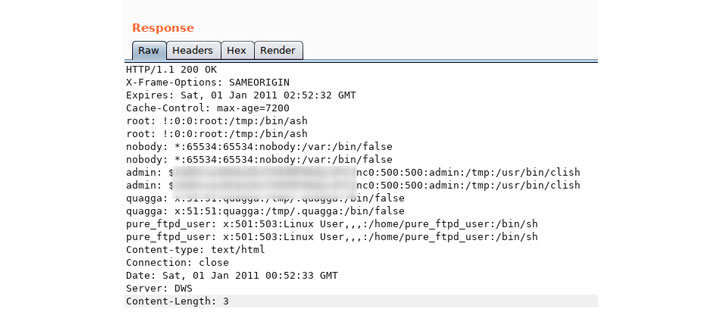
According to the report, at least two separate groups of hackers exploited two critical remote command injection vulnerabilities (CVE-2020-8515) affecting DrayTek Vigor enterprise switches, load-balancers, routers and VPN gateway devices to eavesdrop on network traffic and install backdoors.
The zero-day attacks started somewhere at the end of last November or at the beginning of December and are potentially still ongoing against thousands of publicly exposed DrayTek switches,Vigor 2960, 3900, 300B devices that haven’t yet been patched with the latest firmware updates released last month.
The zero-day vulnerabilities in question can be exploited by any unauthorized remote attackers to inject and execute arbitrary commands on the system, as also detailed by a separate researcher on his blog.
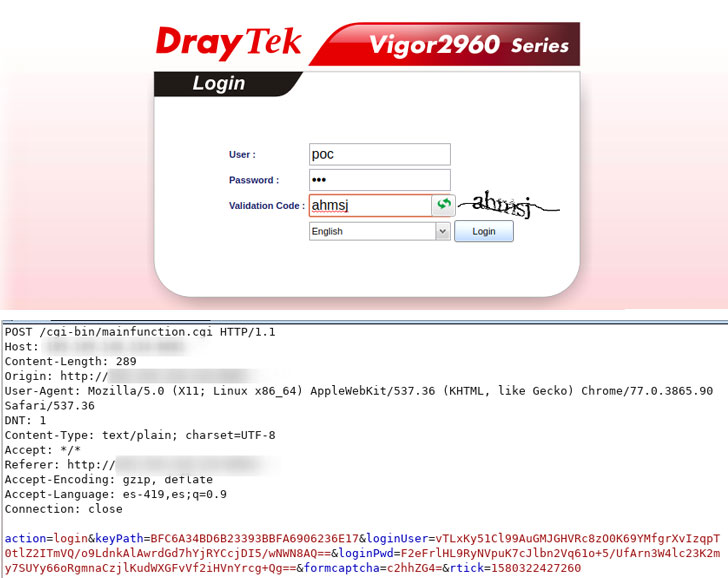
“The two 0-day vulnerability command injection points are keyPath and rtick, located in the /www/cgi-bin/mainfunction.cgi, and the corresponding Web Server program is /usr/sbin/lighttpd,” the report says.
NetLab researchers have not yet attributed both attacks to any specific group, but it did confirm that while the first group simply spied on the network traffic, the second group of attackers used rtick command injection vulnerability to create:
- the web-session backdoor that never expires,
- SSH backdoor on TCP ports 22335 and 32459,
- system backdoor account with user “wuwuhanhan” and password “caonimuqin.”
To be noted, if you have just recently installed the patched firmware, or installing now, it won’t remove backdoor accounts automatically in case you’re already compromised.
“We recommend that DrayTek Vigor users check and update their firmware in a timely manner and check whether there is a tcpdump process, SSH backdoor account, Web Session backdoor, etc. on their systems.”
“If you have remote access enabled on your router, disable it if you don’t need it, and use an access control list if possible,” the company suggests.
The list of affected firmware versions are as follow:
- Vigor2960 < v1.5.1
- Vigor300B < v1.5.1
- Vigor3900 < v1.5.1
- VigorSwitch20P2121 <= v2.3.2
- VigorSwitch20G1280 <= v2.3.2
- VigorSwitch20P1280 <= v2.3.2
- VigorSwitch20G2280 <= v2.3.2
- VigorSwitch20P2280 <= v2.3.2
Affected companies and individuals are highly recommended to install the latest firmware updates to completely protect their valuable networks against malware and emerging online threats.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C