Sudo Bug Lets Non-Privileged Linux and macOS Users Run Commands as Root
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
4.6 Medium
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:L/AC:L/Au:N/C:P/I:P/A:P
Joe Vennix of Apple security has found another significant vulnerability in sudo utility that under a specific configuration could allow low privileged users or malicious programs to execute arbitrary commands with administrative (‘root’) privileges on Linux or macOS systems.
Sudo is one of the most important, powerful, and commonly used utilities that comes as a core command pre-installed on macOS and almost every UNIX or Linux-based operating system.
Sudo has been designed to let users run apps or commands with the privileges of a different user without switching environments.
Sudo Vulnerability (CVE-2019-18634)
The newly discovered privilege escalation vulnerability, tracked as CVE-2019-18634, in question stems from a stack-based buffer overflow issue that resides in Sudo versions before 1.8.26.
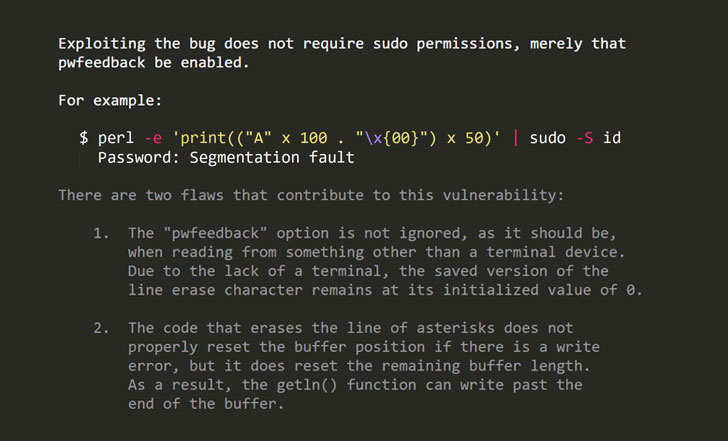
According to Vennix, the flaw can only be exploited when the “pwfeedback” option is enabled in the sudoers configuration file, a feature that provides visual feedback, an asterisk (*), when a user inputs password in the terminal.
To be noted, the pwfeedback feature is not enabled by default in the upstream version of sudo or many other packages. However, some Linux distributions, such as Linux Mint and Elementary OS, do enable it in their default sudoers files.
Besides this, when pwfeedback is enabled, the vulnerability can be exploited by any user, even without sudo permissions.
“The bug can be reproduced by passing a large input to sudo via a pipe when it prompts for a password,” Sudo developer Todd C. Miller explained. “Because the attacker has complete control of the data used to overflow the buffer, there is a high likelihood of exploitability.”
Check If You’re Affected and Apply Patches
To determine if your sudoers configuration is affected, you can run “sudo -l” command on your Linux or macOS terminal to find whether the “pwfeedback” option is enabled and listed in the “Matching Defaults entries” output.
If enabled, you can disable the vulnerable component by changing “Defaults pwfeedback” to “Defaults !pwfeedback” in the sudoers configuration file to prevent the exploitation of the privilege escalation vulnerability.
Vennix responsibly reported the vulnerability to the maintainers of Sudo, who late last week released sudo version 1.8.31 with a patch.
“While the logic bug is also present in sudo versions 1.8.26 through 1.8.30 it is not exploitable due to a change in EOF handling introduced in sudo 1.8.26,” Miller said.
Apple has also released a patch update for macOS High Sierra 10.13.6, macOS Mojave 10.14.6, macOS Catalina 10.15.2 last week.
Joe Vennix last year reported a similar impact vulnerability in Sudo that could have been exploited by an attacker to run commands as root just by specifying the user ID “-1” or “4294967295.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
4.6 Medium
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:L/AC:L/Au:N/C:P/I:P/A:P