Flaw in Microsoft Outlook Lets Hackers Easily Steal Your Windows Password
6.5 Medium
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N
4.3 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
NONE
Availability Impact
NONE
AV:N/AC:M/Au:N/C:P/I:N/A:N
0.032 Low
EPSS
Percentile
90.1%
A security researcher has disclosed details of an important vulnerability in Microsoft Outlook for which the company released an incomplete patch this month—almost 18 months after receiving the responsible disclosure report.
The Microsoft Outlook vulnerability (CVE-2018-0950) could allow attackers to steal sensitive information, including users’ Windows login credentials, just by convincing victims to preview an email with Microsoft Outlook, without requiring any additional user interaction.
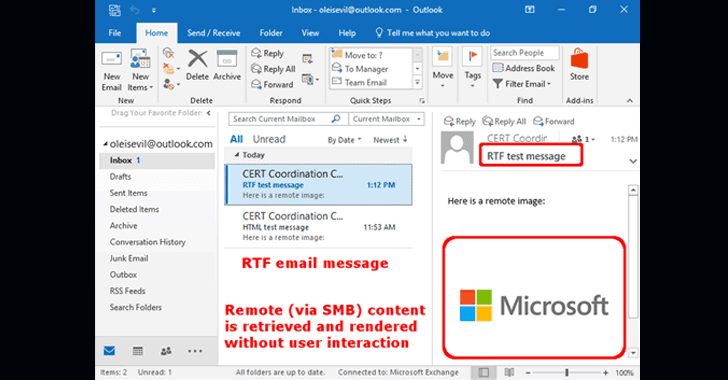
The vulnerability, discovered by Will Dormann of the CERT Coordination Center (CERT/CC), resides in the way Microsoft Outlook renders remotely-hosted OLE content when an RTF (Rich Text Format) email message is previewed and automatically initiates SMB connections.
A remote attacker can exploit this vulnerability by sending an RTF email to a target victim, containing a remotely-hosted image file (OLE object), loading from the attacker-controlled SMB server.
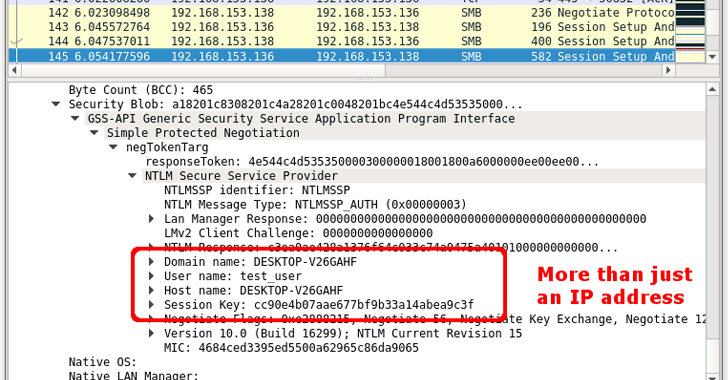
Since Microsoft Outlook automatically renders OLE content, it will initiate an automatic authentication with the attacker’s controlled remote server over SMB protocol using single sign-on (SSO), handing over the victim’s username and NTLMv2 hashed version of the password, potentially allowing the attacker to gain access to the victim’s system.
“This may leak the user’s IP address, domain name, username, hostname, and password hash. If the user’s password is not complex enough, then an attacker may be able to crack the password in a short amount of time,” the US-CERT explains.
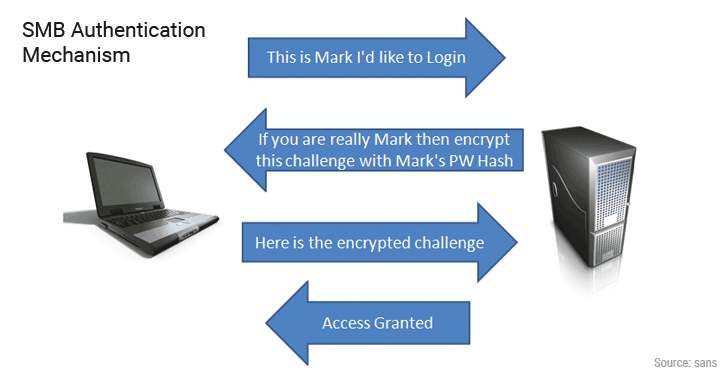
If you are thinking, why would your Windows PC automatically hand over your credentials to the attacker’s SMB server?
This is how authentication via the Server Message Block (SMB) protocol works in combination with the NTLM challenge/response authentication mechanism, as described in the following image.
Dormann reported the vulnerability to Microsoft in November 2016, and in an attempt to patch the issue, the company released an incomplete fix in its April 2018 patch Tuesday update—that’s almost 18 months of the reporting.
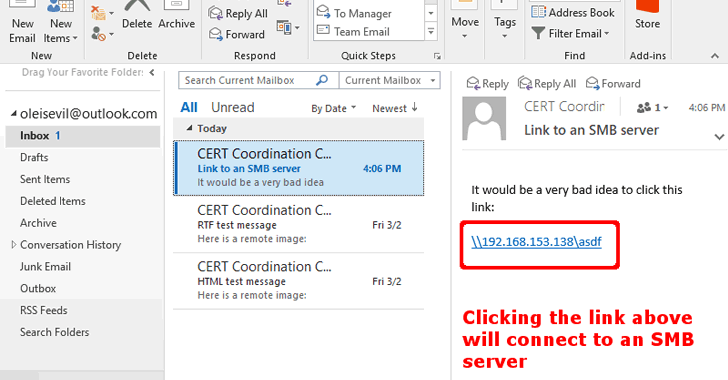
The security patch only prevents Outlook from automatically initiating SMB connections when it previews RTF emails, but the researcher noted that the fix does not prevent all SMB attacks.
“It is important to realize that even with this patch, a user is still a single click away from falling victim to the types of attacks described above,” Dormann said. "For example, if an email message has a UNC-style link that begins with “\", clicking the link initiates an SMB connection to the specified server.”
If you have already installed the latest Microsoft patch update, that’s great, but attackers can still exploit this vulnerability. So, Windows users, especially network administrators at corporates, are advised to follow the below-mentioned steps to mitigate this vulnerability.
- Apply the Microsoft update for CVE-2018-0950, if you have not yet.
- Block specific ports (445/tcp, 137/tcp, 139/tcp, along with 137/udp and 139/udp) used for incoming and outgoing SMB sessions.
- Block NT LAN Manager (NTLM) Single Sign-on (SSO) authentication.
- Always use complex passwords, that cannot be cracked easily even if their hashes are stolen (you can use password managers to handle this task).
- Most important, don’t click on suspicious links provided in emails.
6.5 Medium
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
NONE
Availability Impact
NONE
CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:N
4.3 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
NONE
Availability Impact
NONE
AV:N/AC:M/Au:N/C:P/I:N/A:N
0.032 Low
EPSS
Percentile
90.1%