Critical Code Execution Flaw Found in LIVE555 Streaming Library
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.003 Low
EPSS
Percentile
65.0%
Security researchers have discovered a serious code execution vulnerability in the LIVE555 streaming media library—which is being used by popular media players, along with a number of embedded devices capable of streaming media.
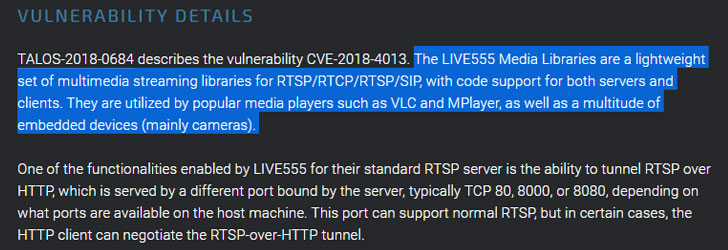
LIVE555 streaming media, developed and maintained by Live Networks, is a set of C++ libraries companies and application developers use to stream multimedia over open standard protocols like RTP/RTCP, RTSP or SIP.
The LIVE555 streaming media libraries support streaming, receiving, and processing of various video formats such as MPEG, H.265, H.264, H.263+, VP8, DV, and JPEG video, and several audio codecs such as MPEG, AAC, AMR, AC-3, and Vorbis.
UPDATE: LIVE555 streaming media library supports both server and client, and is internally being used by many well-known media software such as VLC and MPlayer, security researchers at Talos mentioned in the advisory.
Though researchers didn’t specify if the vulnerable component (a server-side library) is being used by the popular VLC player, team at VLC today contacted THN and clarified that their media player application is using LIVE555 streaming media at the client-side only.
The code execution vulnerability, tracked as CVE-2018-4013 and discovered by researcher Lilith Wyatt of Cisco Talos Intelligence Group, resides in the HTTP packet-parsing functionality of the LIVE555 RTSP, which parses HTTP headers for tunneling RTSP over HTTP.
> “A specially crafted packet can cause a stack-based buffer overflow, resulting in code execution,” Cisco Talos’ security advisory says. “An attacker can send a packet to trigger this vulnerability.”
To exploit this vulnerability, all an attacker needs to do is create and send “a packet containing multiple ‘Accept:’ or ‘x-sessioncookie’ strings” to the vulnerable application, which will trigger a stack buffer overflow in the ‘lookForHeader’ function, leading to arbitrary code execution.
Cisco Talos team confirmed the vulnerability in Live Networks LIVE555 Media Server version 0.92, but the team believes the security issue may also be present in the earlier version of the product.
Cisco Talos responsibly reported the vulnerability to Live Networks on October 10 and publicly disclosed the security issue on October 18 after the vendor released security patches on October 17.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
0.003 Low
EPSS
Percentile
65.0%