Unpatched GPS Tracker Bugs Could Let Attackers Disrupt Vehicles Remotely — The Hacker News
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning of a handful of unpatched security vulnerabilities in MiCODUS MV720 Global Positioning System (GPS) trackers outfitted in over 1.5 million vehicles that could lead to remote disruption of critical operations.
“Successful exploitation of these vulnerabilities may allow a remote actor to exploit access and gain control of the global positioning system tracker,” CISA said. “These vulnerabilities could impact access to a vehicle fuel supply, vehicle control, or allow locational surveillance of vehicles in which the device is installed.”
Available on sale for $20 and manufactured by the China-based MiCODUS, the company’s tracking devices are employed by major organizations in 169 countries spanning aerospace, energy, engineering, government, manufacturing, nuclear power plant, and shipping sectors.
The top countries with the most users include Chile, Australia, Mexico, Ukraine, Russia, Morocco, Venezuela, Brazil, Poland, Italy, Indonesia, Uzbekistan, and South Africa.
The issues, which were identified during the course of a security audit by BitSight, could also be potentially abused to track individuals without their knowledge, disable vehicles, and even pose national security implications in light of the fact that militaries and law enforcement agencies use the trackers for real-time monitoring.
“A nation-state adversary could potentially exploit the tracker’s vulnerabilities to gather intelligence on military-related movements including supply routes, regular troop movements, and recurring patrols,” BitSight researchers pointed out.
The list of flaws that were disclosed to MiCODUS in September 2021 is below -
- CVE-2022-2107 (CVSS score: 9.8) - Use of a hard-coded master password that could enable an unauthenticated attacker to carry out adversary-in-the-middle (AitM) attacks and seize control of the tracker.
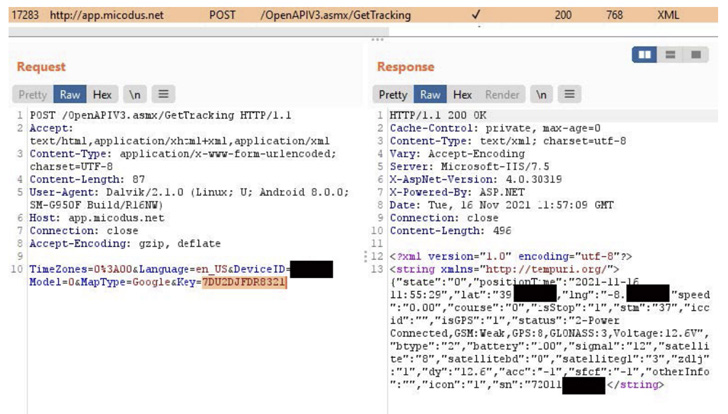
- CVE-2022-2141 (CVSS score: 9.8) - Broken authentication scheme in the API server that enables an attacker to control all traffic between the GPS tracker and the original server and gain control.
- No assigned CVE (CVSS score: 8.1) - Use of a preconfigured default password “123456” that allows attackers to access any GPS tracker at random.
- CVE-2022-2199 (CVSS score: 7.5) - A reflected cross-site scripting (XSS) vulnerability in the web server that could lead to the execution of arbitrary JavaScript code in the web browser.
- CVE-2022-34150 (CVSS score: 7.1) - An access control vulnerability stemming from Insecure Direct Object Reference (IDOR) that could result in the exposure of sensitive information.
- CVE-2022-33944 (CVSS score: 6.5) - A case of authenticated IDOR vulnerability that could be leveraged to generate Excel reports about device activity.
In a nutshell, the flaws could be weaponized to obtain access to location, routes, fuel cutoff commands as well as the ability to disarm various features such as alarms.
But with no workaround in sight, users of the GPS tracker in question are advised to take steps to minimize exposure or alternatively cease using the devices and disable them altogether until a fix is made available by the company.
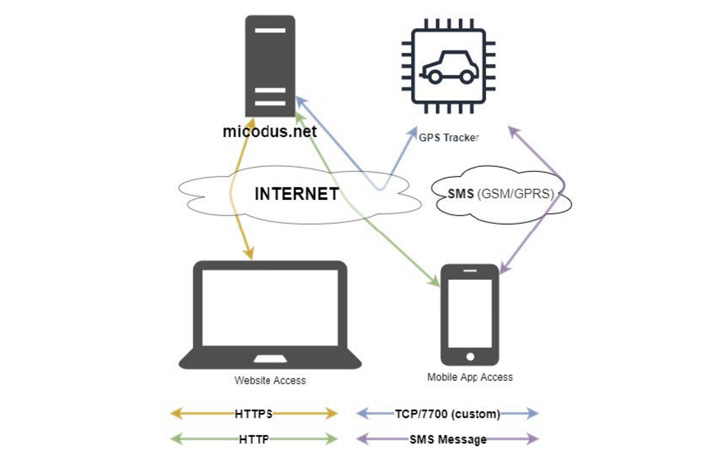
“Having a centralized dashboard to monitor GPS trackers with the ability to enable or disable a vehicle, monitor speed, routes and leverage other features is useful to many individuals and organizations,” the researchers said. “However, such functionality can introduce serious security risks.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.