Kaseya Rules Out Supply-Chain Attack; Says VSA 0-Day Hit Its Customers Directly
EPSS
Percentile
98.5%
U.S. technology firm Kaseya, which is firefighting the largest ever supply-chain ransomware strike on its VSA on-premises product, ruled out the possibility that its codebase was unauthorizedly tampered with to distribute malware.
While initial reports raised speculations that REvil, the ransomware gang behind the attack, might have gained access to Kaseya’s backend infrastructure and abused it to deploy a malicious update to VSA servers running on client premises, in a modus operandi similar to that of the devastating SolarWinds hack, it has since emerged that a never-before-seen security vulnerability (CVE-2021-30116) in the software was leveraged to push ransomware to Kaseya’s customers.
“The attackers were able to exploit zero-day vulnerabilities in the VSA product to bypass authentication and run arbitrary command execution,” the Miami-headquartered company noted in the incident analysis. “This allowed the attackers to leverage the standard VSA product functionality to deploy ransomware to endpoints. There is no evidence that Kaseya’s VSA codebase has been maliciously modified.”
In other words, while successful zero-day exploitation on Kaseya VSA software by itself isn’t a supply-chain attack, taking advantage of the exploit to compromise managed service providers (MSPs) and breach their customers would constitute as one.
It’s, however, unclear as to how the hackers learned of the vulnerabilities. The details of those flaws have not yet been publicly released, although Huntress Labs revealed that “Cybercriminals have exploited an arbitrary file upload and code injection vulnerability and have high confidence an authentication bypass was used to gain access into these servers.”
Image Source: Cybereason
About 60 MSPs and 1,500 downstream businesses around the world have been paralyzed by the ransomware attack, according to the company’s CEO Fred Voccola, most of which have been small concerns, like dental practices, architecture firms, plastic surgery centers, and libraries.
Hackers associated with the Russia-linked REvil ransomware-as-a-service (RaaS) group initially demanded $70 million in Bitcoins to release a decryptor tool for restoring all the affected businesses’ data, although they have swiftly lowered the asking price to $50 million, suggesting a willingness to negotiate their demands in return for a lesser amount.
“REvil ransomware has been advertised on underground forums for three years and it is one of the most prolific RaaS operations,” Kaspersky researchers said Monday, adding “the gang earned over $100 million from its operations in 2020.”
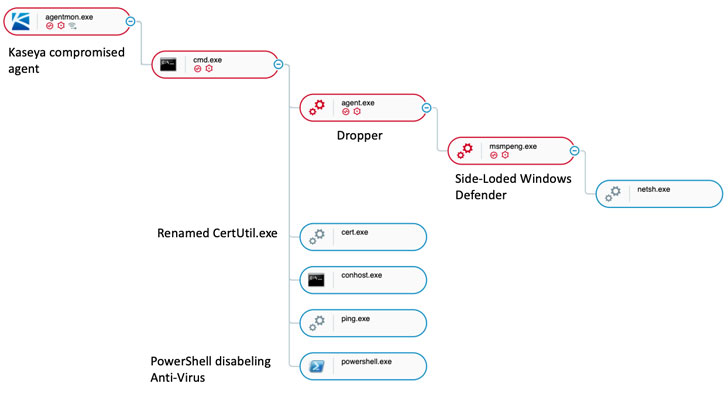
The attack chain worked by first deploying a malicious dropper via a PowerShell script which was executed through Kaseya’s VSA software.
“This script disables Microsoft Defender for Endpoint protection features and then uses the certutil.exe utility to decode a malicious executable (agent.exe) that drops a legitimate Microsoft binary (MsMpEng.exe, an older version of Microsoft Defender) and malicious library (mpsvc.dll), which is the REvil ransomware. This library is then loaded by the legitimate MsMpEng.exe by utilizing the DLL side-loading technique,” the researchers added.
The incident has also led the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to offer mitigation guidance, urging businesses to enable multi-factor authentication, limit communication with remote monitoring and management (RMM) capabilities to known IP address pairs, and place administrative interfaces of RMM behind a virtual private network (VPN) or a firewall on a dedicated administrative network.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.