Critical Flaw Reported in Popular Evernote Extension for Chrome Users
6.1 Medium
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
CHANGED
Confidentiality Impact
LOW
Integrity Impact
LOW
Availability Impact
NONE
CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
4.3 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:M/Au:N/C:N/I:P/A:N
0.001 Low
EPSS
Percentile
38.7%
Cybersecurity researchers discover a critical flaw in the popular Evernote Chrome extension that could have allowed hackers to hijack your browser and steal sensitive information from any website you accessed.
Evernote is a popular service that helps people taking notes and organize their to-do task lists, and over 4,610,000 users have been using its** Evernote Web Clipper Extension** for Chrome browser.
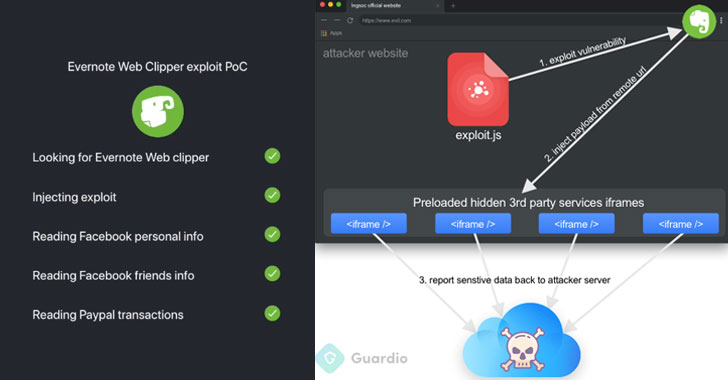
Discovered by Guardio, the vulnerability (CVE-2019-12592) resided in the ways Evernote Web Clipper extension interacts with websites, iframes and inject scripts, eventually breaking the browser’s same-origin policy (SOP) and domain-isolation mechanisms.
According to researchers, the vulnerability could allow an attacker-controlled website to execute arbitrary code on the browser in the context of other domains on behalf of users, leading to a Universal Cross-site Scripting (UXSS or Universal XSS) issue.
> “A full exploit that would allow loading a remote hacker controlled script into the context of other websites can be achieved via a single, simple window.postMessage command,” the researchers said.
> “By abusing Evernote’s intended injection infrastructure, the malicious script will be injected into all target frames in the page regardless of cross-origin constraints.”
As shown in the video demonstration, the researchers also developed a Proof-of-Concept (PoC) exploit that can inject a customized payload on targeted websites, and steal cookies, credentials, and other private information from an unsuspecting user.
No doubt extensions add a lot of useful features to your web browser, but at the same time, the idea of trusting 3rd-party code is much more dangerous than most people realize.
Since extensions run in your web browser, they often require the ability to make network requests, access and change the content of web pages you visit, which poses a massive threat to your privacy and security, doesn’t matter if you have installed it from the official Firefox or Chrome stores.
> “While the app author intends to provide better user experience, extensions usually have permissions to access a trove of sensitive resources and pose a much greater security risk than traditional websites,” the researchers warned.
Guardio team responsibly reported this issue to Evernote late last month, who then released an updated, patched version of its Evernote Web Clipper extension for Chrome users.
Since Chrome Browser periodically, usually after every 5 hours, checks for new versions of installed extensions and updates them without requiring user intervention, you need to make sure your browser is running the latest Evernote version 7.11.1 or later.
6.1 Medium
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
CHANGED
Confidentiality Impact
LOW
Integrity Impact
LOW
Availability Impact
NONE
CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
4.3 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:M/Au:N/C:N/I:P/A:N
0.001 Low
EPSS
Percentile
38.7%