REvil Used 0-Day in Kaseya Ransomware Attack, Demands $70 Million Ransom
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
Amidst the massive supply-chain ransomware attack that triggered an infection chain compromising thousands of businesses on Friday, new details have emerged about how the notorious Russia-linked REvil cybercrime gang may have pulled off the unprecedented hack.
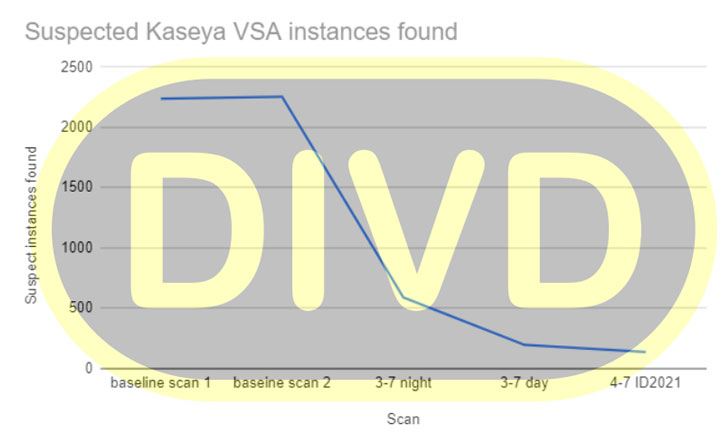
The Dutch Institute for Vulnerability Disclosure (DIVD) on Sunday revealed it had alerted Kaseya to a number of zero-day vulnerabilities in its VSA software (CVE-2021-30116) that it said were being exploited as a conduit to deploy ransomware. The non-profit entity said the company was in the process of resolving the issues as part of a coordinated vulnerability disclosure when the July 2 attacks took place.
More specifics about the flaws were not shared, but DIVD chair Victor Gevers hinted that the zero-days are trivial to exploit. At least 1,000 businesses are said to have been affected by the attacks, with victims identified in no less than 17 countries, including the U.K., South Africa, Canada, Argentina, Mexico, Indonesia, New Zealand, and Kenya, according to ESET.
Kaseya VSA is a cloud-based IT management and remote monitoring solution for managed service providers (MSPs), offering a centralized console to monitor and manage endpoints, automate IT processes, deploy security patches, and control access via two-factor authentication.
REvil Demands $70 Million Ransom
Active since April 2019, REvil (aka Sodinokibi) is best known for extorting $11 million from the meat-processor JBS early last month, with the ransomware-as-a-service business accounting for about 4.6% of attacks on the public and private sectors in the first quarter of 2021.
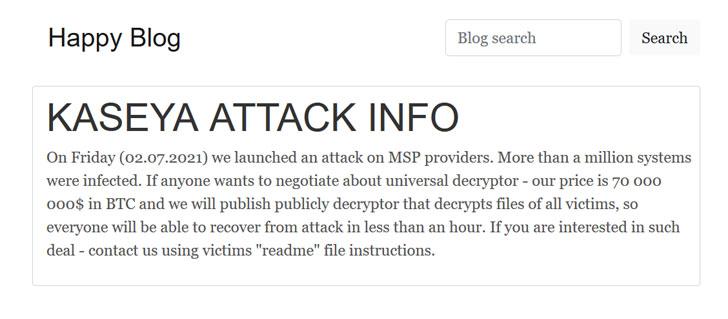
The group is now asking for a record $70 million ransom payment to publish a universal decryptor that can unlock all systems that have been crippled by file-encrypting ransomware.
“On Friday (02.07.2021) we launched an attack on MSP providers. More than a million systems were infected. If anyone wants to negotiate about universal decryptor – our price is 70,000,000$ in BTC and we will publish publicly decryptor that decrypts files of all victims, so everyone will be able to recover from attack in less than an hour,” the REvil group posted on their dark web data leak site.
Kaseya, which has enlisted the help of FireEye to help with its investigation into the incident, said it intends to “bring our SaaS data centers back online on a one-by-one basis starting with our E.U., U.K., and Asia-Pacific data centers followed by our North American data centers.”
On-premises VSA servers will require the installation of a patch prior to a restart, the company noted, adding it’s in the process of readying the fix for release on July 5.
CISA Issues Advisory
The development has prompted the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to issue an advisory, urging customers to download the Compromise Detection Tool that Kaseya has made available to identify any indicators of compromise (IoC), enable multi-factor authentication, limit communication with remote monitoring and management (RMM) capabilities to known IP address pairs, and place administrative interfaces of RMM behind a virtual private network (VPN) or a firewall on a dedicated administrative network.
“Less than ten organizations [across our customer base] appear to have been affected, and the impact appears to have been restricted to systems running the Kaseya software,” Barry Hensley, Chief Threat Intelligence Officer at Secureworks, told The Hacker News via email.
“We have not seen evidence of the threat actors attempting to move laterally or propagate the ransomware through compromised networks. That means that organizations with wide Kaseya VSA deployments are likely to be significantly more affected than those that only run it on one or two servers.”
By compromising a software supplier to target MSPs, who, in turn, provide infrastructure or device-centric maintenance and support to other small and medium businesses, the development once again underscores the importance of securing the software supply chain, while also highlighting how hostile agents continue to advance their financial motives by combining the twin threats of supply chain attacks and ransomware to strike hundreds of victims at once.
“MSPs are high-value targets — they have large attack surfaces, making them juicy targets to cybercriminals,” said Kevin Reed, chief information security officer at Acronis. “One MSP can manage IT for dozens to a hundred companies: instead of compromising 100 different companies, the criminals only need to hack one MSP to get access to them all.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P