Researcher Claims Hotspot Shield VPN Service Exposes You on the Internet
0.026 Low
EPSS
Percentile
90.4%
Virtual Private Network (VPN) is one of the best solutions you can have to protect your privacy and data on the Internet, but you should be more vigilant while choosing a VPN service which truly respects your privacy.
If you are using the popular VPN service Hotspot Shield for online anonymity and privacy, you may inadvertently be leaking your real IP address and other sensitive information.
Developed by AnchorFree GmbH, Hotspot Shield is a VPN service available for free on Google Play Store and Apple Mac App Store with an estimated 500 million users around the world.
The service promises to “secure all online activities,” hide users’ IP addresses and their identities and protect them from tracking by transferring their internet and browsing traffic through its encrypted channel.
However, an ‘alleged’ information disclosure vulnerability discovered in Hotspot Shield results in the exposure of users data, like the name of Wi-Fi network name (if connected), their real IP addresses, which could reveal their location, and other sensitive information.
The vulnerability, assigned CVE-2018-6460, has been discovered and reported to the company by an independent security researcher, Paulos Yibelo, but he made details of the vulnerability to the public on Monday after not receiving a response from the company.
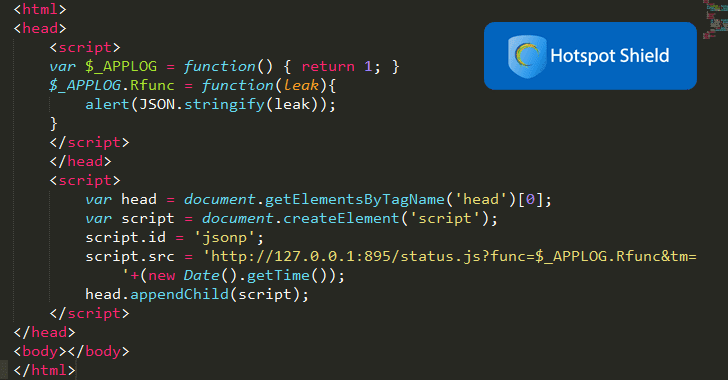
According to the researcher claims, the flaw resides in the local web server (runs on a hardcoded host 127.0.0.1 and port 895) that Hotspot Shield installs on the user’s machine.
This server hosts multiple JSONP endpoints, which are surprisingly accessible to unauthenticated requests as well that in response could reveal sensitive information about the active VPN service, including its configuration details.
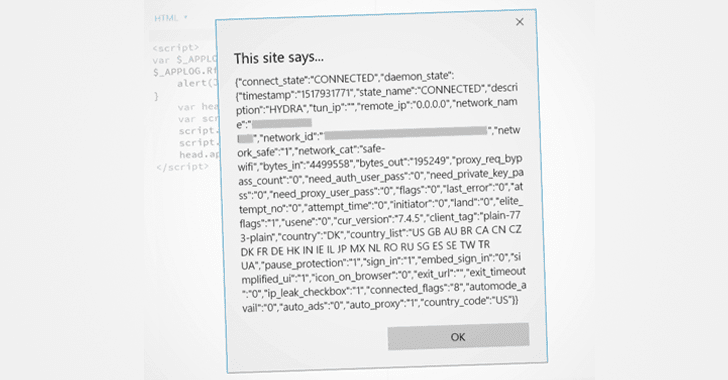
> “https://localhost:895/status.js generates a sensitive JSON response that reveals whether the user is connected to VPN, to which VPN he/she is connected to what and what their real IP address is & other system juicy information. There are other multiple endpoints that return sensitive data including configuration details,” Yibelo claims.
> “User-controlled input is not sufficiently filtered: an unauthenticated attacker can send a POST request to /status.js with the parameter func=$_APPLOG.Rfunc and extract sensitive information about the machine,” the vulnerability description reads.
Yibelo has also publicly released a proof-of-concept (PoC) exploit code—just a few lines of JavaScript code—that could allow an unauthenticated, remote attacker to extract sensitive information and configuration data.
However, ZDNet reporter Zack Whittaker tries to verify researcher’s claim and found that the PoC code only revealed the Wi-Fi network name and country, but not the real IP address.
In a statement, AnchorFree spokesperson acknowledged the vulnerability but denied the disclosure of real IP address as claimed by Yibelo.
> “We have found that this vulnerability does not leak the user’s real IP address or any personal information, but may expose some generic information such as the user’s country,” the spokesperson told ZDNet.
The researcher also claims that he was able to leverage this vulnerability to achieve remote code execution.
Hotspot Shield also made headlines in August last year, when the Centre for Democracy and Technology (CDT), a US non-profit advocacy group for digital rights, accused the service of allegedly tracking, intercepting and collecting its customers’ data.