Hackers Increasingly Using 'Browser-in-the-Browser' Technique in Ukraine Related Attacks
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
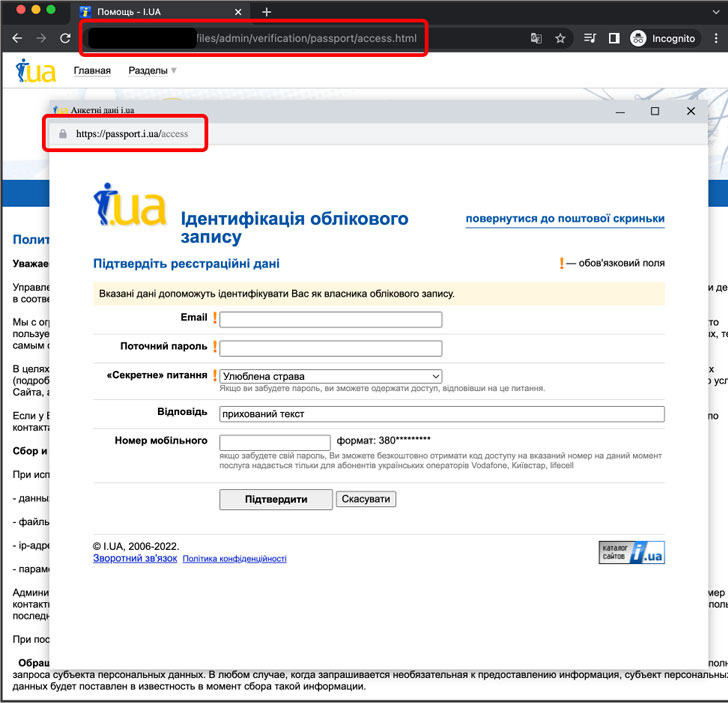
A Belarusian threat actor known as Ghostwriter (aka UNC1151) has been spotted leveraging the recently disclosed browser-in-the-browser (BitB) technique as part of their credential phishing campaigns exploiting the ongoing Russo-Ukrainian conflict.
The method, which masquerades as a legitimate domain by simulating a browser window within the browser, makes it possible to mount convincing social engineering campaigns.
“Ghostwriter actors have quickly adopted this new technique, combining it with a previously observed technique, hosting credential phishing landing pages on compromised sites,” Google’s Threat Analysis Group (TAG) said in a new report, using it to siphon credentials entered by unsuspected victims to a remote server.
Among other groups using the war as a lure in phishing and malware campaigns to deceive targets into opening fraudulent emails or links include Mustang Panda and Scarab as well as nation-state actors from Iran, North Korea, and Russia.
Also included in the list is Curious Gorge, a hacking crew that TAG has attributed to China’s People’s Liberation Army Strategic Support Force (PLASSF), which has orchestrated attacks against government and military organizations in Ukraine, Russia, Kazakhstan, and Mongolia.
A third set of attacks observed over the past two-week period originated from a Russia-based hacking group known as COLDRIVER (aka Callisto). TAG said that the actor staged credential phishing campaigns targeting multiple U.S.-based NGOs and think tanks, the military of a Balkans country, and an unnamed Ukrainian defense contractor.
“However, for the first time, TAG has observed COLDRIVER campaigns targeting the military of multiple Eastern European countries, as well as a NATO Centre of Excellence,” TAG researcher Billy Leonard said. “These campaigns were sent using newly created Gmail accounts to non-Google accounts, so the success rate of these campaigns is unknown.”
Viasat breaks down February 24 Attack
The disclosure comes as U.S.-based telecommunications firm Viasat spilled details of a “multifaceted and deliberate” cyber attack against its KA-SAT network on February 24, 2022, coinciding with Russia’s military invasion of Ukraine.
The attack on the satellite broadband service disconnected tens of thousands of modems from the network, impacting several customers in Ukraine and across Europe and affecting the operations of 5,800 wind turbines belonging to the German company Enercon in Central Europe.
“We believe the purpose of the attack was to interrupt service,” the company explained. “There is no evidence that any end-user data was accessed or compromised, nor customer personal equipment (PCs, mobile devices, etc.) was improperly accessed, nor is there any evidence that the KA-SAT satellite itself or its supporting satellite ground infrastructure itself were directly involved, impaired or compromised.”
Viasat linked the attack to a “ground-based network intrusion” that exploited a misconfiguration in a VPN appliance to gain remote access to the KA-SAT network and execute destructive commands on the modems that “overwrote key data in flash memory,” rendering them temporarily unable to access the network.
Russian dissidents targeted with Cobalt Strike
The relentless attacks are the latest in a long list of malicious cyber activities that have emerged in the wake of the continuing conflict in Eastern Europe, with government and commercial networks suffering from a string of disruptive data wiper infections in conjunction with a series of ongoing distributed denial-of-service (DDoS) attacks.
This has also taken the form of compromising legitimate WordPress sites to inject rogue JavaScript code with the goal of carrying out DDoS attacks against Ukrainian domains, according to researchers from the MalwareHunterTeam.
But it’s not just Ukraine. Malwarebytes Labs this week laid out specifics of a new spear-phishing campaign targeting Russian citizens and government entities in an attempt to deploy pernicious payloads on compromised systems.
“The spear phishing emails are warning people that use websites, social networks, instant messengers and VPN services that have been banned by the Russian Government and that criminal charges will be laid,” Hossein Jazi said. “Victims are lured to open a malicious attachment or link to find out more, only to be infected with Cobalt Strike.”
The malware-laced RTF documents contain an exploit for the widely abused MSHTML remote code execution vulnerability (CVE-2021-40444), leading to the execution of a JavaScript code that spawns a PowerShell command to download and execute a Cobalt Strike beacon retrieved from a remote server.
Another cluster of activity potentially relates to a Russian threat actor tracked as Carbon Spider (aka FIN7), which has employed a similar maldocs-oriented attack vector that’s engineered to drop a PowerShell-based backdoor capable of fetching and running a next-stage executable.
Malwarebytes also said it has detected a “significant uptick in malware families being used with the intent of stealing information or otherwise gaining access in Ukraine,” including Hacktool.LOIC, Ainslot Worm, FFDroider, Formbook, Remcos, and Quasar RAT.
“While these families are all relatively common in the cybersecurity world, the fact that we witnessed spikes almost exactly when Russian troops crossed the Ukrainian border makes these developments interesting and unusual,” Adam Kujawa, director of Malwarebytes Labs, said in a statement shared with The Hacker News.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P