14 New Security Flaws Found in BusyBox Linux Utility for Embedded Devices
EPSS
Percentile
87.8%
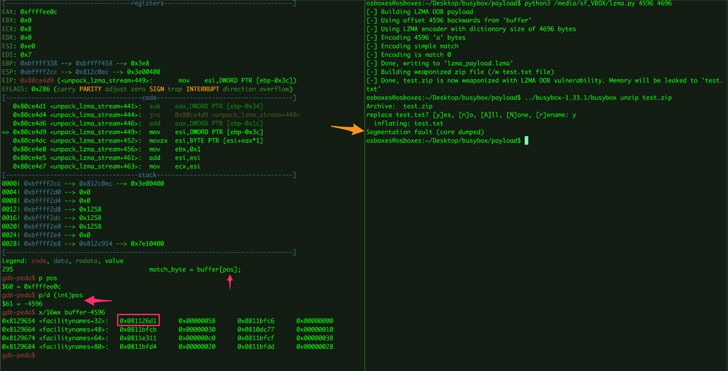
Cybersecurity researchers on Tuesday disclosed 14 critical vulnerabilities in the BusyBox Linux utility that could be exploited to result in a denial-of-service (DoS) condition and, in select cases, even lead to information leaks and remote code execution.
The security weaknesses, tracked from CVE-2021-42373 through CVE-2021-42386, affect multiple versions of the tool ranging from 1.16-1.33.1, DevOps company JFrog and industrial cybersecurity company Claroty said in a joint report.
Dubbed “the Swiss Army Knife of Embedded Linux,” BusyBox is a widely used software suite combining a variety of common Unix utilities or applets (e.g., cp, ls, grep) into a single executable file that can run on Linux systems such as programmable logic controllers (PLCs), human-machine interfaces (HMIs), and remote terminal units (RTUs).
A quick list of the flaws and the applets they impact is below —
- man - CVE-2021-42373
- lzma/unlzma - CVE-2021-42374
- ash - CVE-2021-42375
- hush - CVE-2021-42376, CVE-2021-42377
- awk - CVE-2021-42378, CVE-2021-42379, CVE-2021-42380, CVE-2021-42381, CVE-2021-42382, CVE-2021-42383, CVE-2021-42384, CVE-2021-42385, CVE-2021-42386
Triggered by supplying untrusted data via command line to the vulnerable applets, successful exploitation of the flaws could result in denial-of-service, inadvertent disclosure of sensitive information, and potentially code execution. The weaknesses have since been addressed in BusyBox version 1.34.0, which was released on August 19, following responsible disclosure.
“These new vulnerabilities that we’ve disclosed only manifest in specific cases, but could be extremely problematic when exploitable,” said Shachar Menashe, senior director of security research at JFrog. “The proliferation of BusyBox makes this an issue that needs to be addressed by security teams. As such, we encourage companies to upgrade their BusyBox version, or make sure they are not using any of the affected applets.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.