ALERT — New 21Nails Exim Bugs Expose Millions of Email Servers to Hacking
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
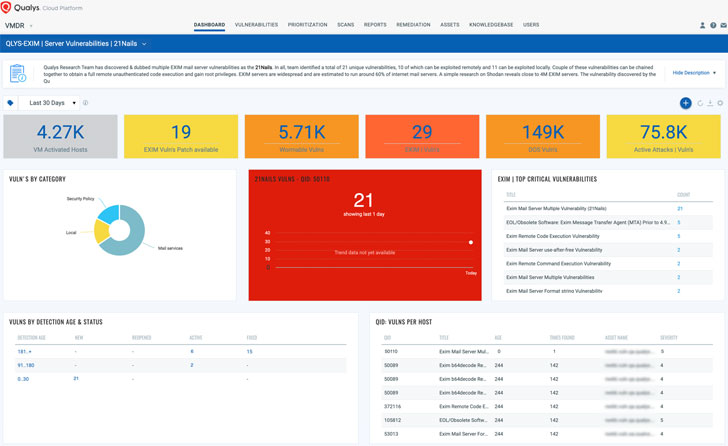
The maintainers of Exim have released patches to remediate as many as 21 security vulnerabilities in its software that could enable unauthenticated attackers to achieve complete remote code execution and gain root privileges.
Collectively named '21Nails,’ the flaws include 11 vulnerabilities that require local access to the server and 10 other weaknesses that could be exploited remotely. The issues were discovered by Qualys and reported to Exim on Oct. 20, 2020.
“Some of the vulnerabilities can be chained together to obtain a full remote unauthenticated code execution and gain root privileges on the Exim Server,” Bharat Jogi, senior manager at Qualys, said in a public disclosure. “Most of the vulnerabilities discovered by the Qualys Research Team for e.g. CVE-2020-28017 affects all versions of Exim going back all the way to 2004.”
Exim is a popular mail transfer agent (MTA) used on Unix-like operating systems, with over 60% of the publicly reachable mail servers on the Internet running the software. A Shodan search reveals nearly four million Exim servers that are exposed online.
Exim Mail Server Multiple Vulnerabilities (21Nails) from Qualys, Inc. on Vimeo.
A quick summary of the 21 bugs is listed below. If successfully exploited, they could be used to tweak email settings and even add new accounts on the compromised mail servers. Technical specifics about the flaws can be accessed here.
Local vulnerabilities:
- CVE-2020-28007: Link attack in Exim’s log directory
- CVE-2020-28008: Assorted attacks in Exim’s spool directory
- CVE-2020-28014: Arbitrary file creation and clobbering
- CVE-2021-27216: Arbitrary file deletion
- CVE-2020-28011: Heap buffer overflow in queue_run()
- CVE-2020-28010: Heap out-of-bounds write in main()
- CVE-2020-28013: Heap buffer overflow in parse_fix_phrase()
- CVE-2020-28016: Heap out-of-bounds write in parse_fix_phrase()
- CVE-2020-28015: New-line injection into spool header file (local)
- CVE-2020-28012: Missing close-on-exec flag for privileged pipe
- CVE-2020-28009: Integer overflow in get_stdinput()
Remote vulnerabilities:
- CVE-2020-28017: Integer overflow in receive_add_recipient()
- CVE-2020-28020: Integer overflow in receive_msg()
- CVE-2020-28023: Out-of-bounds read in smtp_setup_msg()
- CVE-2020-28021: New-line injection into spool header file (remote)
- CVE-2020-28022: Heap out-of-bounds read and write in extract_option()
- CVE-2020-28026: Line truncation and injection in spool_read_header()
- CVE-2020-28019: Failure to reset function pointer after BDAT error
- CVE-2020-28024: Heap buffer underflow in smtp_ungetc()
- CVE-2020-28018: Use-after-free in tls-openssl.c
- CVE-2020-28025: Heap out-of-bounds read in pdkim_finish_bodyhash()
In light of the recent Microsoft Exchange server hacks, it’s imperative the patches are applied immediately, as email servers have emerged as a lucrative target for espionage campaigns. In the past, flaws in Exim software have been actively exploited by bad actors to mount a variety of attacks, including deploying a Linux worm to install cryptocurrency miners on affected servers.
Last May, the U.S. National Security Agency (NSA) warned that Russian military operatives, publicly known as Sandworm Team, were taking advantage of a remote code execution vulnerability tracked as CVE-2019-10149 (aka The Return of the WIZard) to “add privileged users, disable network security settings, execute additional scripts for further network exploitation” at least since August 2019.
The NSA called it an “attacker’s dream access.”
“Mail Transfer Agents are interesting targets for attackers because they are usually accessible over the internet,” Jogi said. “Once exploited, they could modify sensitive email settings on the mail servers, allow adversaries to create new accounts on the target mail servers.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C