Microsoft Warns of Another Unpatched Windows Print Spooler RCE Vulnerability
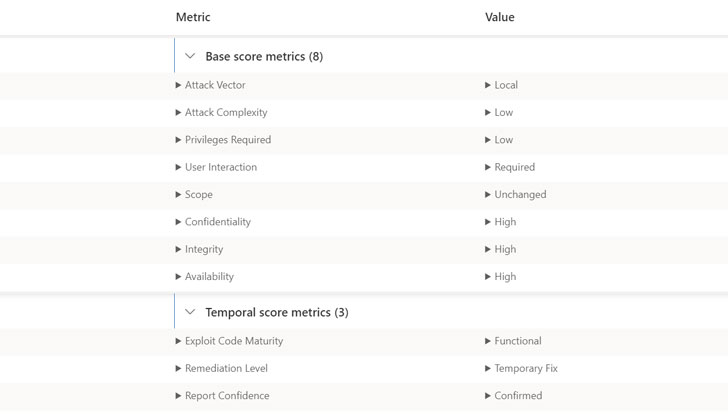
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
A day after releasing Patch Tuesday updates, Microsoft acknowledged yet another remote code execution vulnerability in the Windows Print Spooler component, adding that it’s working to remediate the issue in an upcoming security update.
Tracked as CVE-2021-36958 (CVSS score: 7.3), the unpatched flaw is the latest to join a list of bugs collectively known as PrintNightmare that have plagued the printer service and come to light in recent months. Victor Mata of FusionX, Accenture Security, who has been credited with reporting the flaw, said the issue was disclosed to Microsoft in December 2020.
“A remote code execution vulnerability exists when the Windows Print Spooler service improperly performs privileged file operations,” the company said in its out-of-band bulletin, echoing the vulnerability details for CVE-2021-34481. “An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.”
It’s worth noting that the Windows maker has since released updates to change the default Point and Print default behavior, effectively barring non-administrator users from installing or updating new and existing printer drivers using drivers from a remote computer or server without first elevating themselves to an administrator.
As workarounds, Microsoft is recommending users to stop and disable the Print Spooler service to prevent malicious actors from exploiting the vulnerability. The CERT Coordination Center, in a vulnerability note, is also advising users to block outbound SMB traffic to prevent connecting to a malicious shared printer.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C