Critical Bugs in Control Web Panel Expose Linux Servers to RCE Attacks
Researchers have disclosed details of two critical security vulnerabilities in Control Web Panel that could be abused as part of an exploit chain to achieve pre-authenticated remote code execution on affected servers.
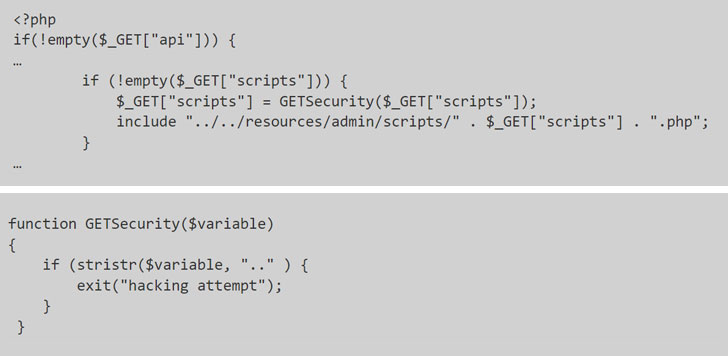
Tracked as CVE-2021-45467, the issue concerns a case of a file inclusion vulnerability, which occurs when a web application is tricked into exposing or running arbitrary files on the web server.
Control Web Panel, previously CentOS Web Panel, is an open-source Linux control panel software used for deploying web hosting environments.
Specifically, the issue arises when two of the unauthenticated PHP pages used in the application — “/user/login.php” and “/user/index.php” — fail to adequately validate a path to a script file, according to Octagon Networks’ Paulos Yibelo, who discovered and reported the flaws.
This means that in order to exploit the vulnerability, all an attacker has to do is to alter the include statement, which is used to include the content of one PHP file into another PHP file, to inject malicious code from a remote resource and achieve code execution.
Interestingly, while the application had protections in place to flag efforts to switch to a parent directory (denoted by “…”) as a “hacking attempt” it did nothing to prevent the PHP interpreter from accepting a specially crafted string such as “.$00.” and effectively achieving a full bypass.
This not only allows a bad actor to access restricted API endpoints, it can be used in conjunction with an arbitrary file write vulnerability (CVE-2021-45466) to gain full remote code execution on the server as follows —
- Send a null byte powered file inclusion payload to add malicious API key
- Use API key to write to a file (CVE-2021-45466)
- Use step #1 to include the file we just wrote into (CVE-2021-45467)
Following responsible disclosure, the flaws have since been addressed by the CWP maintainers along with updates shipped earlier this month.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.