Iranian Hackers Exploiting VMware RCE Bug to Deploy 'Core Impact' Backdoor
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
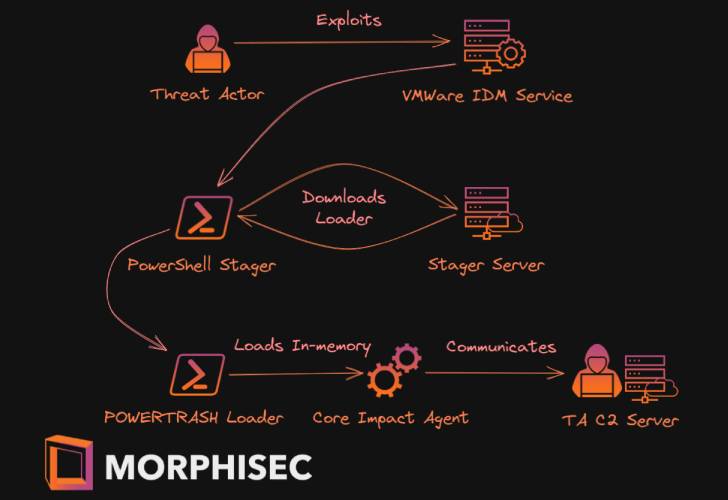
An Iranian-linked threat actor known as Rocket Kitten has been observed actively exploiting a recently patched VMware vulnerability to gain initial access and deploy the Core Impact penetration testing tool on vulnerable systems.
Tracked as CVE-2022-22954 (CVSS score: 9.8), the critical issue concerns a case of remote code execution (RCE) vulnerability affecting VMware Workspace ONE Access and Identity Manager.
While the issue was patched by the virtualization services provider on April 6, 2022, the company cautioned users of confirmed exploitation of the flaw occurring in the wild a week later.
“A malicious actor exploiting this RCE vulnerability potentially gains an unlimited attack surface,” researchers from Morphisec Labs said in a new report. “This means highest privileged access into any components of the virtualized host and guest environment.”
Attack chains exploiting the flaw involve the distribution of a PowerShell-based stager, which is then used to download a next-stage payload called PowerTrash Loader that, in turn, injects the penetration testing tool, Core Impact, into memory for follow-on activities.
“The widespread use of VMWare identity access management combined with the unfettered remote access this attack provides is a recipe for devastating breaches across industries,” the researchers said.
“VMWare customers should also review their VMware architecture to ensure the affected components are not accidentally published on the internet, which dramatically increases the exploitation risks.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C