Iranian Hackers Exploit Log4j Vulnerability to Deploy PowerShell Backdoor
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
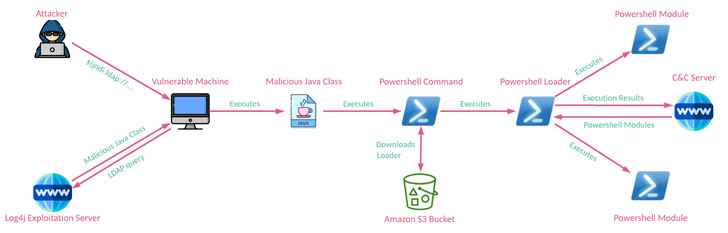
An Iranian state-sponsored actor has been observed scanning and attempting to abuse the Log4Shell flaw in publicly-exposed Java applications to deploy a hitherto undocumented PowerShell-based modular backdoor dubbed “CharmPower” for follow-on post-exploitation.
“The actor’s attack setup was obviously rushed, as they used the basic open-source tool for the exploitation and based their operations on previous infrastructure, which made the attack easier to detect and attribute,” researchers from Check Point said in a report published this week.
The Israeli cybersecurity company linked the attack to a group known as APT35, which is also tracked using the codenames Charming Kitten, Phosphorus, and TA453, citing overlaps with toolsets previously identified as infrastructure used by the threat actor.
Log4Shell aka CVE-2021-44228 (CVSS score: 10.0) concerns a critical security vulnerability in the popular Log4j logging library that, if successfully exploited, could lead to remote execution of arbitrary code on compromised systems.
The ease of the exploitation coupled with the widespread use of Log4j library has created a vast pool of targets, even as the shortcoming has attracted swarms of bad actors, who have seized on the opportunity to stage a dizzying array of attacks since its public disclosure last month.
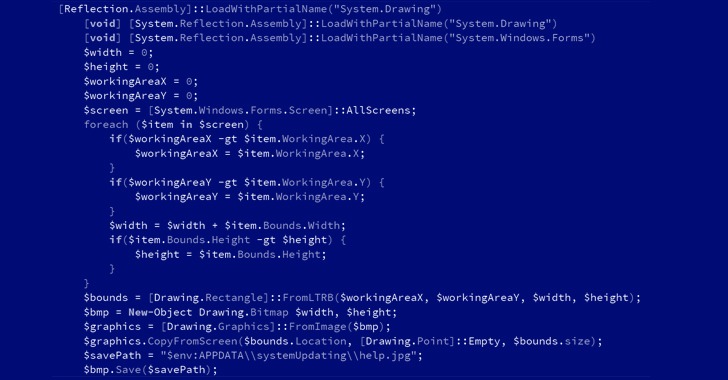
While Microsoft previously pointed out APT35’s efforts to acquire and modify the Log4j exploit, the latest findings show that the hacking group has operationalized the flaw to distribute the PowerShell implant capable of retrieving next-stage modules and exfiltrating data to a command-and-control (C2) server.
CharmPower’s modules also support a variety of intelligence gathering functionality, including features to gather system information, list installed applications, take screenshots, enumerate running processes, execute commands sent from the C2 server, and clean up any signs of evidence created by these components.
The disclosure comes as Microsoft and the NHS cautioned that internet-facing systems running VMware Horizon are being targeted to deploy web shells and a new strain of ransomware called NightSky, with the tech giant connecting the latter to a China-based operator dubbed DEV-0401, which has also deployed LockFile, AtomSilo, and Rook ransomware in the past.
What’s more, Hafnium, another threat actor group operating out of China, has also been observed utilizing the vulnerability to attack virtualization infrastructure to extend their typical targeting, Microsoft noted.
“Judging by their ability to take advantage of the Log4j vulnerability and by the code pieces of the CharmPower backdoor, the actors are able to change gears rapidly and actively develop different implementations for each stage of their attacks,” the researchers said.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C