This New Android Malware Can Gain Root Access to Your Smartphones
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
7.2 High
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:L/AC:L/Au:N/C:C/I:C/A:C
An unidentified threat actor has been linked to a new Android malware strain that features the ability to root smartphones and take complete control over infected smartphones while simultaneously taking steps to evade detection.
The malware has been named “AbstractEmu” owing to its use of code abstraction and anti-emulation checks undertaken to thwart analysis right from the moment the apps are opened. Notably, the global mobile campaign is engineered to target and infect as many devices as possible indiscriminately.
Lookout Threat Labs said it found a total of 19 Android applications that posed as utility apps and system tools like password managers, money managers, app launchers, and data saving apps, seven of which contained the rooting functionality. Only one of the rogue apps, called Lite Launcher, made its way to the official Google Play Store, attracting a total of 10,000 downloads before it was purged.
The apps are said to have been prominently distributed via third-party stores such as the Amazon Appstore and the Samsung Galaxy Store, as well as other lesser-known marketplaces like Aptoide and APKPure.
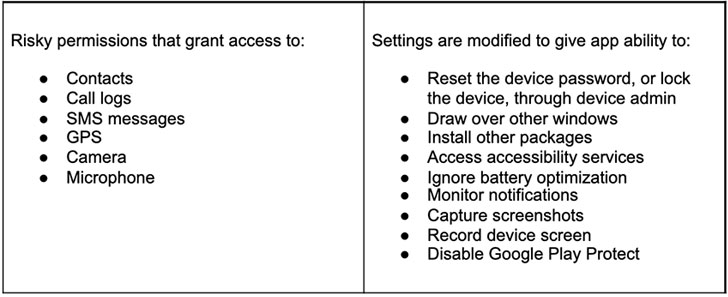
“While rare, rooting malware is very dangerous. By using the rooting process to gain privileged access to the Android operating system, the threat actor can silently grant themselves dangerous permissions or install additional malware — steps that would normally require user interaction,” Lookout researchers said. “Elevated privileges also give the malware access to other apps’ sensitive data, something not possible under normal circumstances.”
Once installed, the attack chain is designed to leverage one of five exploits for older Android security flaws that would allow it to gain root permissions and take over the device, extract sensitive data, and transmit to a remote attack-controlled server —
- CVE-2015-3636 (PongPongRoot)
- CVE-2015-1805 (iovyroot)
- CVE-2019-2215 (Qu1ckr00t)
- CVE-2020-0041, and
- CVE-2020-0069
Lookout attributed the mass distributed rooting malware campaign to a “well-resourced group with financial motivation,” with telemetry data revealing that Android device users in the U.S. were the most impacted. The ultimate objective of the infiltrations remains unclear as yet.
“Rooting Android or jailbreaking iOS devices are still the most invasive ways to fully compromise a mobile device,” the researchers said, adding “mobile devices are perfect tools for cyber criminals to exploit, as they have countless functionalities and hold an immense amount of sensitive data.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
LOW
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
7.2 High
CVSS2
Access Vector
LOCAL
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:L/AC:L/Au:N/C:C/I:C/A:C