Flaw in 4GEE WiFi Modem Could Leave Your Computer Vulnerable
0.001 Low
EPSS
Percentile
39.8%
A high-severity vulnerability has been discovered in 4G-based wireless 4GEE Mini modem sold by mobile operator EE that could allow an attacker to run a malicious program on a targeted computer with the highest level of privileges in the system.
The vulnerability—discovered by 20-year-old Osanda Malith, a Sri Lankan security researcher at ZeroDayLab—can be exploited by a low privileged user account to escalate privileges on any Windows computer that had once connected to the EE Mini modem via USB.
This, in turn, would allow an attacker to gain full system access to the targeted remote computer and thereby, perform any malicious actions, such as installing malware, rootkits, keylogger, or stealing personal information.
4G Mini WiFi modem is manufactured by Alcatel and sold by EE, a mobile operator owned by BT Group— Britain’s largest digital communications company that serves over 31 million connections across its mobile, fixed and wholesale networks.
How Does the Attack Work?
The local privilege escalation flaw, tracked as CVE-2018-14327, resides in the driver files installed by EE 4G Mini WiFi modem on a Windows system and originates because of folder permissions, allowing any low privileged user to “read, write, execute, create, delete do anything inside that folder and it’s subfolders.”
For successful exploitation of the vulnerability, all an attacker or malware just needs to do is replace “ServiceManager.exe” file from the driver folder with a malicious file to trick the vulnerable driver into executing it with higher SYSTEM privileges after reboot.
Malith also posted a video demonstration showing that how attackers can exploit this flaw to escalate their privileges on a Windows machine to gain a reverse shell.
> “An attacker can plant a reverse shell from a low privileged user account and by restarting the computer, the malicious service will be started as “NT AUTHORITY\SYSTEM” by giving the attacker full system access to the remote PC,” he explains in his blog.
Patch Your 4G Wi-Fi Mini Modems
The researcher reported the vulnerability to EE and Alcatel in July, and the company acknowledged the issue and rolled out a firmware patch earlier this month to address the vulnerability.
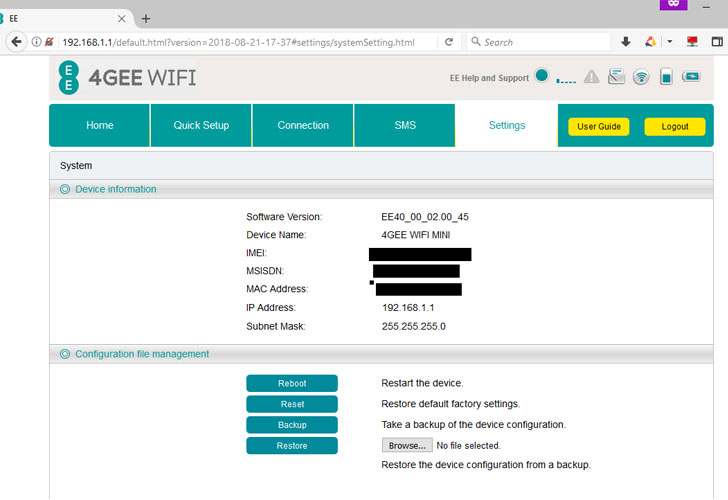
If you own a G-based wireless 4GEE Mini modem from EE, you are advised to update the firmware modem to the latest “EE40_00_02.00_45” version and remove previous vulnerable versions.
Follow these simple steps to update your 4GEE Mini modem to the latest patch update:
- Go to your router’s default gateway: https://192.168.1.1.
- Click on the “Check for Update” to update your firmware.
- Once updated to the patched software version EE40_00_02.00_45, remove the previously installed software version from your computer.
For more details on the vulnerability, you can head on to Malith’s blog, and the detailed advisory released by ZeroDayLab.