New Chrome 0-day Under Active Attacks – Update Your Browser Now
6.5 Medium
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H
4.3 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:N/I:N/A:P
Attention readers, if you are using Google Chrome browser on your Windows, Mac, or Linux computers, you need to update your web browsing software immediately to the latest version Google released earlier today.
Google released Chrome version 86.0.4240.111 today to patch several security high-severity issues, including a zero-day vulnerability that has been exploited in the wild by attackers to hijack targeted computers.
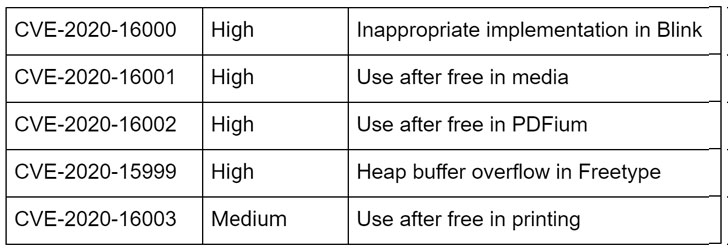
Tracked as CVE-2020-15999, the actively exploited vulnerability is a type of memory-corruption flaw called heap buffer overflow in Freetype, a popular open source software development library for rendering fonts that comes packaged with Chrome.
The vulnerability was discovered and reported by security researcher Sergei Glazunov of Google Project Zero on October 19 and is subject to a seven-day public disclosure deadline due to the flaw being under active exploitation.
Glazunov also immediately reported the zero-day vulnerability to FreeType developers, who then developed an emergency patch to address the issue on October 20 with the release of FreeType 2.10.4.
Without revealing technical details of the vulnerability, the technical lead for Google’s Project Zero Ben Hawkes warned on Twitter that while the team has only spotted an exploit targeting Chrome users, it’s possible that other projects that use FreeType might also be vulnerable and are advised to deploy the fix included in FreeType version 2.10.4.
“While we only saw an exploit for Chrome, other users of freetype should adopt the fix discussed here: https://savannah.nongnu.org/bugs/?59308 – the fix is also in today’s stable release of FreeType 2.10.4,” Hawkes writes.
According to details shared by Glazunov, the vulnerability exists in the FreeType’s function “Load_SBit_Png,” which processes PNG images embedded into fonts. It can be exploited by attackers to execute arbitrary code just by using specifically crafted fonts with embedded PNG images.
“The issue is that libpng uses the original 32-bit values, which are saved in png_struct. Therefore, if the original width and/or height are greater than 65535, the allocated buffer won’t be able to fit the bitmap,” Glazunov explained.
Glazunov also published a font file with a proof-of-concept exploit.
Google released Chrome 86.0.4240.111 as Chrome’s “stable” version, which is available to all users, not just to opted-in early adopters, saying that the company is aware of reports that “an exploit for CVE-2020-15999 exists in the wild,” but did not reveal further details of the active attacks.
Besides the FreeType zero-day vulnerability, Google also patched four other flaws in the latest Chrome update, three of which are high-risk vulnerabilities—an inappropriate implementation bug in Blink, a use after free bug in Chrome’s media, and use after free bug in PDFium—and one medium-risk use after free issue in browser’s printing function.
Although the Chrome web browser automatically notifies users about the latest available version, users are recommended to manually trigger the update process by going to “Help → About Google Chrome” from the menu.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
6.5 Medium
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H
4.3 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
NONE
Integrity Impact
NONE
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:N/I:N/A:P