Citrix Releases Patches for Critical ADC Vulnerability Under Active Attack
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P
Citrix has finally started rolling out security patches for a critical vulnerability in ADC and Gateway software that attackers started exploiting in the wild earlier this month after the company announced the existence of the issue without releasing any permanent fix.
I wish I could say, “better late than never,” but since hackers don’t waste time or miss any opportunity to exploit vulnerable systems, even a short window of time resulted in the compromise of hundreds of Internet exposed Citrix ADC and Gateway systems.
As explained earlier on The Hacker News, the vulnerability, tracked as CVE-2019-19781, is a path traversal issue that could allow unauthenticated remote attackers to execute arbitrary code on several versions of Citrix ADC and Gateway products, as well as on the two older versions of Citrix SD-WAN WANOP.
Rated critical with CVSS v3.1 base score 9.8, the issue was discovered by Mikhail Klyuchnikov, a security researcher at Positive Technologies, who responsibly reported it to Citrix in early December.
The vulnerability is actively being exploited in the wild since last week by dozens of hacking groups and individual attackers—thanks to the public release of multiple proofs-of-concept exploit code.
According to cyber security experts, as of today, there are over 15,000 publicly accessible vulnerable Citrix ADC and Gateway servers that attackers can exploit overnight to target potential enterprise networks.
FireEye experts found an attack campaign where someone was compromising vulnerable Citrix ADCs to install a previously-unseen payload, dubbed “NotRobin,” that scans systems for cryptominers and malware deployed by other potential attackers and removes them to maintain exclusive backdoor access.
> #Citrix released a free tool that analyzes available log sources and system forensic artifacts to identify whether an ADC appliance has potentially been compromised using CVE-2019-19781 security flaw.
You can find the tool and instructions here: <https://t.co/eewijzI2l9>[#infosec](<https://twitter.com/hashtag/infosec?src=hash&ref_src=twsrc^tfw>) <https://t.co/YKMwgPzmYE>
>
> — The Hacker News (@TheHackersNews) January 22, 2020
“This actor exploits NetScaler devices using CVE-2019-19781 to execute shell commands on the compromised device,” FireEye said.
“FireEye believes that the actor behind NOTROBIN has been opportunistically compromising NetScaler devices, possibly to prepare for an upcoming campaign. They remove other known malware, potentially to avoid detection by administrators.”
Citrix Patch Timeline: Stay Tuned for More Software Updates!
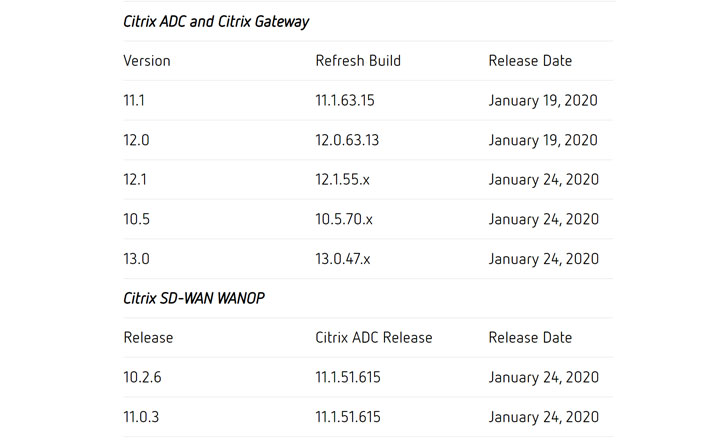
Last week Citrix announced a timeline, promising to release patched firmware updates for all supported versions of ADC and Gateway software before the end of January 2020, as shown in the chart.
As part of its first batch of updates, Citrix today released permanent patches for ADC versions 11.1 and 12.0 that also apply to “ADC and Gateway VPX hosted on ESX, Hyper-V, KVM, XenServer, Azure, AWS, GCP or on a Citrix ADC Service Delivery Appliance (SDX).”
“It is necessary to upgrade all Citrix ADC and Citrix Gateway 11.1 instances (MPX or VPX) to build 11.1.63.15 to install the security vulnerability fixes. It is necessary to upgrade all Citrix ADC and Citrix Gateway 12.0 instances (MPX or VPX) to build 12.0.63.13 to install the security vulnerability fixes,” Citrix said in its advisory.
“We urge customers to install these fixes immediately,” the company said. “If you have not already done so, you need to apply the previously supplied mitigation to ADC versions 12.1, 13, 10.5, and SD-WAN WANOP versions 10.2.6 and 11.0.3 until the fixes for those versions are available.”
The company also warned that customers with multiple ADC versions in production must apply the correct version of patch to each system separately.
Besides installing available patches for supported versions and applying the recommended mitigation for unpatched systems, Citrix ADC administrators are also advised to monitor their device logs for attacks.
**UPDATE —**Citrix on Thursday also released second batch of permanent security patches for critical RCE vulnerability affecting ADC and Gateway versions 12.1 and 13.0.
9.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
7.5 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:L/Au:N/C:P/I:P/A:P