Chinese Hackers Targeted Dozens of Industrial Enterprises and Public Institutions
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C
Over a dozen military-industrial complex enterprises and public institutions in Afghanistan and Europe have come under a wave of targeted attacks since January 2022 to steal confidential data by simultaneously making use of six different backdoors.
Russian cybersecurity firm Kaspersky attributed the attacks “with a high degree of confidence” to a China-linked threat actor tracked by Proofpoint as TA428, citing overlaps in tactics, techniques, and procedures (TTPs).
TA428, also known by the names Bronze Dudley, Temp.Hex, and Vicious Panda, has a history of striking entities in Ukraine, Russia, Belarus, and Mongolia. It’s believed to share connections with another hacking group called Mustang Panda (aka Bronze President).
Targets of the latest cyber espionage campaign included industrial plants, design bureaus and research institutes, government agencies, ministries and departments in several East European countries and Afghanistan.
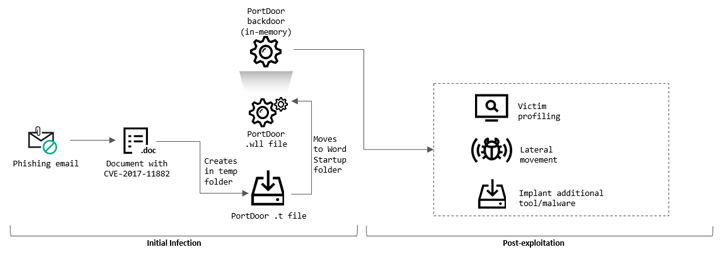
Attack chains entail penetrating the enterprise IT networks using carefully crafted phishing emails, including some that referenced non-public information pertaining to the organizations, to trick recipients into opening rogue Microsoft Word documents.
These decoy files come with exploits for a 2017 memory corruption flaw in the Equation Editor component (CVE-2017-11882) that could lead to the execution of arbitrary code in the affected systems, ultimately leading to the deployment of a backdoor called PortDoor.
PortDoor was notably employed in spear-phishing attacks mounted by Chinese state-sponsored hackers in April 2021 to break into the systems of a defense contractor that designs submarines for the Russian Navy.
The use of six different implants, Kaspersky noted, is likely an attempt on the part of the threat actors to establish redundant channels for controlling infected hosts should one of them get detected and removed from the networks.
The intrusions culminate with the attacker hijacking the domain controller and gaining complete control of all of the organization’s workstations and servers, leveraging the privileged access to exfiltrate files of interest in the form of compressed ZIP archives to a remote server located in China.
Other backdoors utilized in the attacks include nccTrojan, Cotx, DNSep, Logtu, and a previously undocumented malware dubbed as CotSam, so named owing to its similarities with Cotx. Each provides extensive functionality for commandeering the systems and harvesting sensitive data.
Also incorporated in the attacks is Ladon, a hacking framework the lateral movement that also enables the adversary to scan for devices in the network as well as exploit security vulnerabilities in them to execute malicious code.
“Spear-phishing remains one of the most relevant threats to industrial enterprises and public institutions,” Kaspersky said. “The attackers used primarily known backdoor malware, as well as standard techniques for lateral movement and antivirus solution evasion.”
“At the same time, they were able to penetrate dozens of enterprises and even take control of the entire IT infrastructure, and IT security solutions of some of the organizations attacked.”
The findings arrive a little over two months after the Twisted Panda actors were observed targeting research institutes in Russia and Belarus to drop a bare-bones backdoor called Spinner.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
7.8 High
CVSS3
Attack Vector
LOCAL
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
9.3 High
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:M/Au:N/C:C/I:C/A:C