Imperva Thwarts 2.5 Million RPS Ransom DDoS Extortion Attacks
9.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
NONE
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N
6.4 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:P/A:N
Cybersecurity company Imperva on Friday said it recently mitigated a ransom distributed denial-of-service (DDoS) attack targeting an unnamed website that peaked at 2.5 million requests per second (RPS).
“While ransom DDoS attacks are not new, they appear to be evolving and becoming more interesting with time and with each new phase,” Nelli Klepfish, security analyst at Imperva, said. “For example, we’ve seen instances where the ransom note is included in the attack itself embedded into a URL request.”
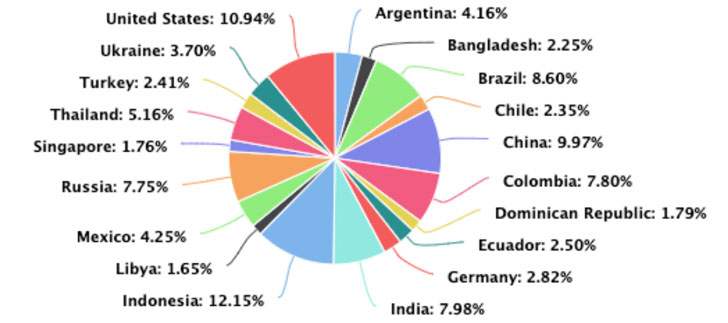
The top sources of the attacks came from Indonesia, followed by the U.S., China, Brazil, India, Colombia, Russia, Thailand, Mexico, and Argentina.
Distributed denial-of-service (DDoS) attacks are a subcategory of denial-of-service (DoS) attacks in which an army of connected online devices, known as a botnet, is used to overwhelm a target website with fake traffic in an attempt to render it unavailable to legitimate users.
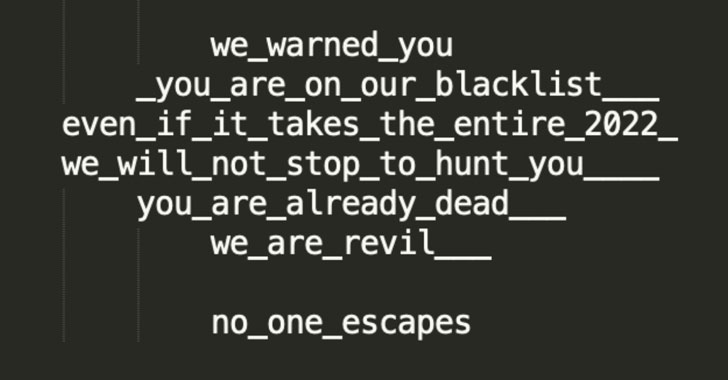
The California-headquartered firm said that the affected entity received multiple ransom notes included as part of the DDoS attacks, demanding the company make a bitcoin payment to stay online and avoid losing “hundreds of millions in market cap.”
In an interesting twist, the attackers are calling themselves REvil, the infamous ransomware-as-a-service cartel that suffered a major setback after a number of its operators were arrested by Russian law enforcement authorities earlier this January.
“It is not clear however whether the threats were really made by the original REvil group or by an imposter,” Klepfish noted.
Attack origins
The 2.5 million RPS attack is said to have lasted less than a minute, with one of the sister sites operated by the same company sustaining a similar attack that lasted approximately 10 minutes, even as the tactics employed were constantly changed to avert possible mitigation.
Evidence gathered by Imperva points to the DDoS attacks originating from the Mēris botnet, which has continued to leverage a now-addressed security vulnerability in Mikrotik routers (CVE-2018-14847) to strike targets, including Yandex last September.
“The types of sites the threat actors are after appear to be business sites focusing on sales and communications,” Klepfish said. “Targets tend to be U.S.- or Europe-based with the one thing they all have in common being that they are all exchange-listed companies and the threat actors use this to their advantage by referring to the potential damage a DDoS attack could do to the company stock price.”
The findings come as malicious actors have been spotted weaponizing a new amplification technique called TCP Middlebox Reflection for the very first time in the wild to hit banking, travel, gaming, media, and web hosting industries with a flood of fake traffic.
The ransom DDoS attack is also the second botnet-related activity averted by Imperva since the start of the year, what with the company detailing a web scraping attack that targeted an unidentified job listing platform in late January.
“The attacker used a large-scale botnet, generating no less than 400 million bot requests from nearly 400,000 unique IP addresses over four days with the intent of harvesting job seekers’ profiles,” the security firm said.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
9.1 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
NONE
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
NONE
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:N
6.4 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
LOW
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
NONE
AV:N/AC:L/Au:N/C:P/I:P/A:N