The Origin of Threat Hunting
2011 Article “Become a Hunter”
The term “threat hunting” has been popular with marketers from security companies for about five years. Yesterday Anton Chuvakin asked about the origin of the term.
I appear to have written the first article describing threat hunting in any meaningful way. It was published in the July-August 2011 issue of Information Security Magazine and was called “Become a Hunter.” I wrote it in the spring of 2011, when I was director of incident response for GE-CIRT. Relevant excerpts include:
"To best counter targeted attacks, one must conduct counter-threat operations (CTOps). In other words, defenders must actively hunt intruders in their enterprise. These intruders can take the form of external threats who maintain persistence or internal threats who abuse their privileges. Rather than hoping defenses will repel invaders, or that breaches will be caught by passive alerting mechanisms, CTOps practitioners recognize that defeating intruders requires actively detecting and responding to them. CTOps experts then feed the lessons learned from finding and removing attackers into the software development lifecycle (SDL) and configuration and IT management processes to reduce the likelihood of future incidents…
In addition to performing SOC work, CTOps requires more active, unstructured, and creative thoughts and approaches. **One way to characterize this more vigorous approach to detecting and responding to threats is the term “hunting.”****In the mid-2000s, the Air Force popularized the term “hunter-killer” for a missions whereby teams of security experts performed “friendly force projection” on their networks.**They combed through data from systems and in some cases occupied the systems themselves in order to find advanced threats.The concept of “hunting” (without the slightly more aggressive term “killing”) is now gaining ground in the civilian world.
2013 Book “The Practice of NSM”
If the SOC is characterized by a group that reviews alerts for signs of intruder action, the CIRT is recognized by the likelihood that senior analysts are taking junior analysts on “hunting trips.” A senior investigator who has discovered a novel or clever way to possibly detect intruders guides one or more junior analysts through data and systems looking for signs of the enemy. Upon validating the technique (and responding to any enemy actions), the hunting team should work to incorporate the new detection method into the repeatable processes used by SOC-type analysts. This idea of developing novel methods, testing them into the wild, and operationalizing them is the key to fighting modern adversaries."
The “hunting trips” I mentioned were activities that our GE-CIRT incident handlers – David Bianco, Ken Bradley, Tim Crothers, Tyler Hudak, Bamm Visscher, and Aaron Wade – were conducting. Aaron in particular was a driving force for hunting methodology.
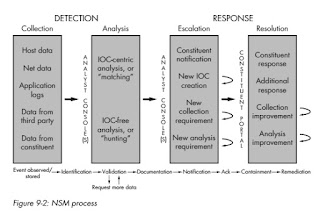
I also discussed hunting in chapter 9 of my 2013 book The Practice of Network Security Monitoring, contrasting it with “matching” as seen in figure 9-2. (If you want to save 30% off the book at No Starch, use discount code “NSM101.”)
The question remains: from where did I get the term “hunt”? My 2011 article stated “In the mid-2000s, the Air Force popularized the term “hunter-killer.” My friend Doug Steelman, a veteran of the Air Force, NSA, and Cyber Command, provided a piece of the puzzle on Twitter. He posted a link to a 2009 presentation by former NSA Vulnerability and Analysis Operations (VAO) chief Tony Sager, a friend of this blog.
July 2009 Presentation by Tony Sager
In the mid-2000s I was attending an annual conference held by NSA called the Red Team/Blue Team Symposium, or ReBl for short. ReBl took place over a week’s time at the Johns Hopkins University Applied Physics Lab in Laurel, MD. If you Google for the conference you will likely find WikiLeaks emails from the HBGary breach.
It was a mix of classified and unclassified presentations on network defense. During these presentations I heard the term “APT” for the first time. I also likely heard about the “hunt” missions the Air Force was conducting, in addition to probably hearing Tony Sager’s presentation mentioning a “hunt” focus.
That is as far back as I can go, but at least we have a decent understanding where I most likely first heard the term “threat hunting” in use by practitioners. Happy hunting!
Copyright 2003-2018 Richard Bejtlich and TaoSecurity (taosecurity.blogspot.com and www.taosecurity.com)