
Cybersecurity considerations to have when shopping for holiday gifts
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
7.4 High
AI Score
Confidence
High
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
0.001 Low
EPSS
Percentile
49.1%

As I wrote about last week, there are holiday shopping-related scams already popping up all over the place.
But another aspect of security that many shoppers don't consider this time of year is the security of the products they're buying, even through a legitimate online marketplace.
This is a glaring issue with home security cameras and Wi-Fi-connected doorbells, but I can't imagine these are particularly popular holiday gifts. With virtually everything being connected to the internet somehow these days, everything is a potential security risk if you're buying a new piece of technology.
Take smartwatches, for example. Apple Watches and Samsung Galaxy watches are always popular on everyone's wishlists this time of year because they're high-priced items you normally wouldn't buy for yourself. Many shoppers might be looking for a deal this time of year and not looking to spend hundreds on the gift, so any sort of cheaper alternative could be appealing.
I searched for "smart watches" on Amazon, and the results page displayed four different watches from four different vendors as their "Top Results," none of which were Samsung and Apple. Well-known vendors are certainly not immune to security issues or vulnerabilities, but at least users can be confident that any known vulnerabilities will be disclosed and patched by these companies as they pop up.
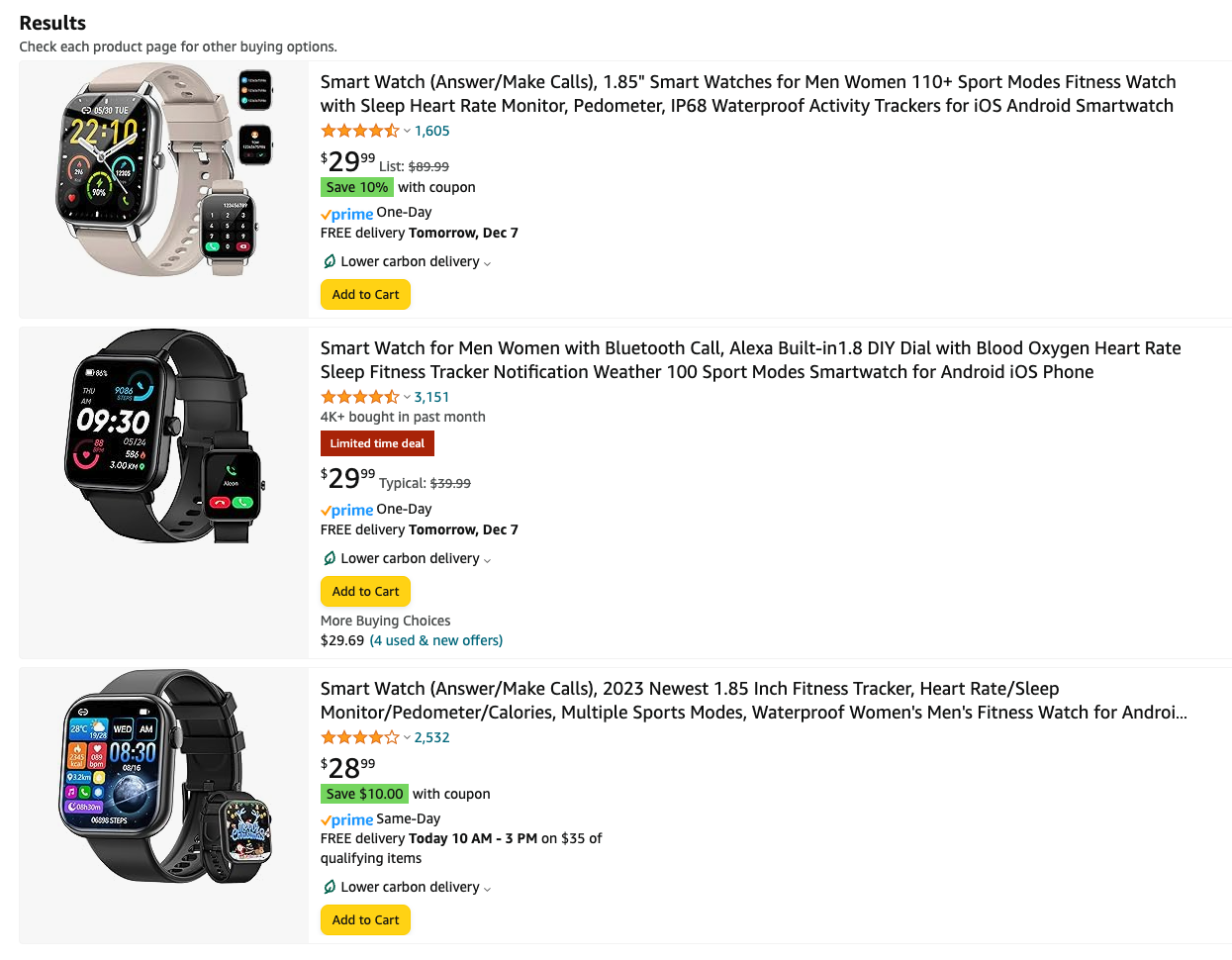
The top result is for a $29.99 smartwatch that offers sleep tracking, blood pressure monitoring, dozens of different workout modes, step tracking, and more. However, there are a few security flags for me right up front with this deal (after all, if it seems too good to be true, it probably is). Amazon states the seller is a company called "Nerunsa," but a quick search did not turn up any legitimate information on who this company is, where they're based, or the sort of security bona fides you'd be hoping for. The only search results are for the company's Amazon store page and a few eBay listings for people reselling the watch in question.
The app that's listed as supporting the watch is called "GloryFit" on the Google Play and Apple app stores, and its privacy policy is equally vague. It states that the app will collect all the suspected information for someone using a smartwatch – phone calls, text messages, GPS location, personal information, health information, etc. But, the policy states that, when the user accepts the privacy policy, "You hereby consent to our process and disclose personal information to our affiliated companies (which are in the communications, social media, technology and cloud businesses) and to Third Party Service Providers for the purposes of this Privacy Policy." And it's not particularly clear what those other companies do, exactly – Google was no help here, either.
Apple Air Tags are also another popular tech gift every year and are usually featured in major retailers' Black Friday sales. I personally have my own concerns about any type of tracking tag coming into my house, but that's for another column.
On Walmart, which is increasingly trying to compete with Amazon by offering more products online, I searched for "smart tag" and found three results that appeared ahead of Apple's legitimate Air Tags. The second-most-popular result is for a "Bluetooth Tracker and Item Locator" that's only $15.98, compared to $86.88 for a four-pack of Apple's. This tracker is listed as being made by "AILIUTOP," which also remains elusive on the internet and does not seem to have any sort of legitimate contact information available to the public. Their store page on Walmart indicates the seller offers many types of products, from clothing to home goods and more.
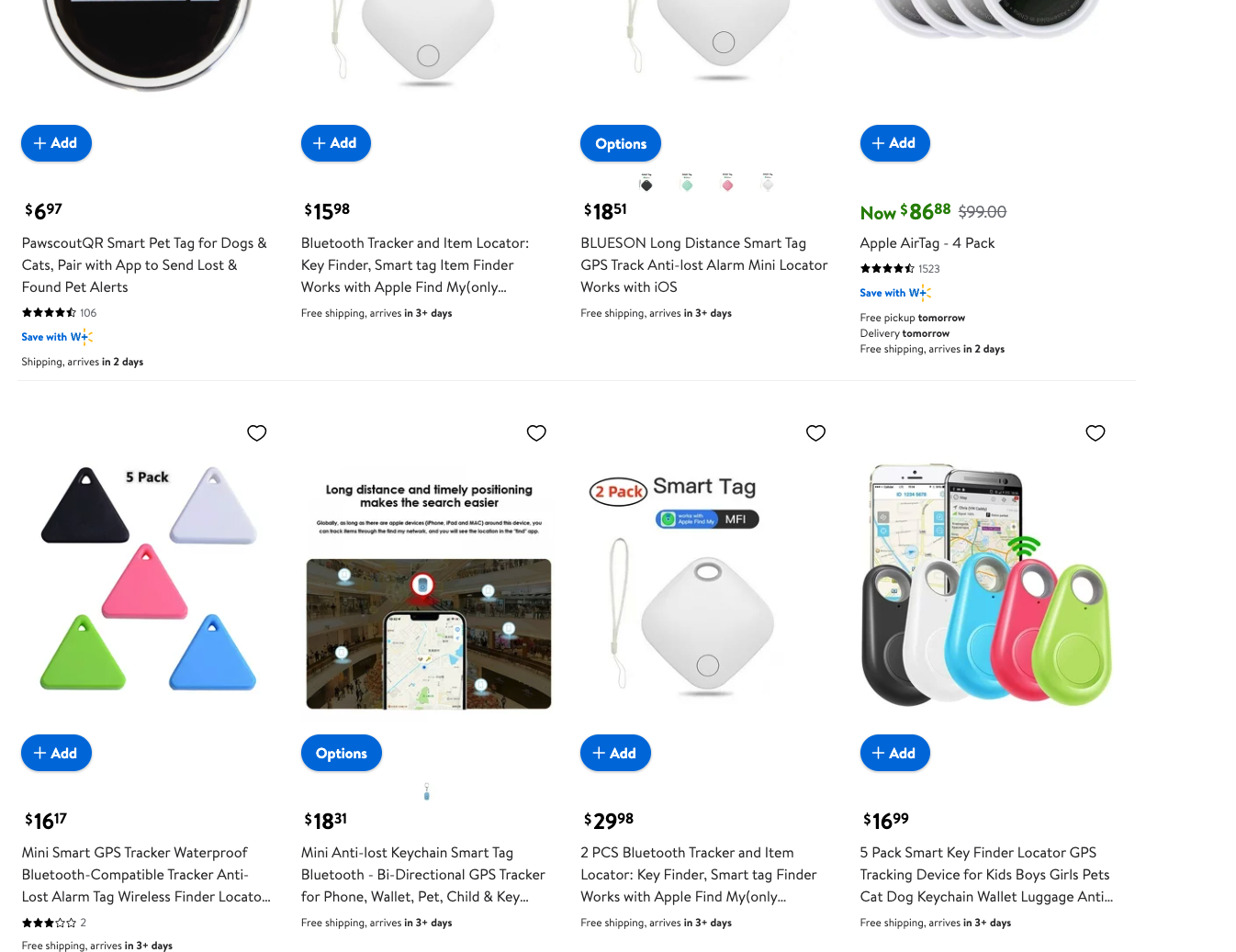
This seems like a good bargain as a gift for someone who is always losing their keys or wallet or wants to make sure their bicycle is secure when they lock it up somewhere. But purchasing these types of "smart" devices with so much uncertainty poses a few issues.
If you do experience some sort of security failure or issue, there is no easy way to contact any of these vendors through the traditional means that the average user would go searching for. These vendors have no clear history of responsibly disclosing vulnerabilities, releasing security updates, or testing their products' security before release.
When these types of gifts are dealing with such high-profile information like your personal information, health data, or physical location, users should be confident that their information is being stored correctly and securely, or at least there's a way to contact the vendor should they have any questions.
When searching for holiday gifts online, make sure you're buying from a trusted vendor, or if you haven't heard of the vendor before, take a few extra minutes just to look them up, read their app's privacy policy, or even read the reviews to make sure there's no clear sign of bot activity like repetitive words or phrases or using the same photo for multiple reviews.
The one big thing
The 2023 Cisco Talos Year in Review is now available to download. Once again, the Talos team has meticulously combed through a massive amount of data to analyze the major trends that have shaped the threat landscape in 2023. Global conflict influenced a lot of these trends, altering the tactics and approaches of many threat actors. In operations ranging from espionage to cybercrime, we've seen geopolitical events have a significant impact on the way these are carried out.
Why do I care?
The Year in Review report includes new data and telemetry from Talos about attacker trends, popular malware seen in the wild, and much more. Despite the accelerated pace of many threat actor campaigns and the geopolitical events that shaped them, our report shows that the defensive community's diligence, inventiveness and collaborative efforts are helping to push adversaries back.
So now what?
Download our full report here, bookmark the Year in Review landing page for future content we have planned around the report, and listen to the Beers with Talos episode that covers the details of the report.
Top security headlines of the week
More than six million people are reportedly victims of a large data breach at DNA and genealogy testing firm 23andMe. The breach is larger than initially expected, with more than 5.5 million users who opted into the company's "DNA Relatives" feature, which allows customers to automatically share some of their data with other users. Another 1 million-plus users had their family tree information accessed. The attackers accessed the accounts because of password reuse from users, likely who used easy-to-guess login information or passwords they used across multiple other accounts. 23andMe was not the target of the initial breach, nor was a company account the source of the compromised credentials. Security experts are urging users to move away from traditional username-and-password login methods as these types of attacks happen more often, instead moving toward multi-factor authentication or passwordless logins. (TechCrunch, Wall Street Journal)
Apple released emergency fixes for two zero-day vulnerabilities in its WebKit browser engine that have already been exploited in the wild. The company reported that the flaws are being exploited on devices running on iOS versions before iOS 16.7.1 (released on Oct. 10, 2023). There are new patches available, which users should install immediately, in iOS, iPadOS, macOS Sonoma and the Safari web browser. The two vulnerabilities tracked as CVE-2023-42916 and CVE-2023-42917, leave affected devices vulnerable to adversaries accessing sensitive information on targeted devices. CVE-2023-42917 could also allow an attacker to execute arbitrary code on the targeted machine. (SC Magazine, Decipher)
Security researchers say a new threat actor known as "AeroBlade" compromised a U.S. aerospace company for more than a year. The actor reportedly started testing their malware and infection chain on the targeted network in September 2022 and executed malware on the network in July 2023. The activity sat undetected for months due to anti-analysis techniques. It is currently unknown what actions, if any, the actor carried out during that time or if they compromised any user or customer data. The initial infection began with a Microsoft Word lure document with the title, ""SOMETHING WENT WRONG Enable Content to load the document." The ensuing malicious Microsoft Word template (DOTM) file then loaded a DLL that served as a reverse shell. Researchers say the attacker's intent was likely to steal data from the target to sell it, potentially supply it to international competitors, or use it to extort the target into paying a ransom. (Dark Reading, Bleeping Computer)
Can't get enough Talos?
Security journalists from Decipher bring you the headlines, including new U.S. government sanctions on threat actor groups in our latest Threat Spotlight video.
Then, Hazel chats to Talos security researcher Joe Marshall to discuss the Talos 2023 Year in Review, and Project PowerUp, the story of how Cisco Talos worked with a multi-national, multi-company coalition of volunteers and experts to help "keep the lights on" in Ukraine, by injecting a measure of stability in Ukraine's power transmission grid.
Upcoming events where you can find Talos
"Power of the Platform" by Cisco** (Dec. 5 & 7)**
Virtual (Please note: This presentation will only be given in German)
_The annual IT event at the end of the year where Cisco experts, including Gergana Karadzhova-Dangela from Cisco Talos Incident Response, discuss the future-oriented topics in the implementation of digitalization together with you. _
What Threats Kept Us Up in 2023: A Year in Review and a Look Ahead** (Dec. 13, 11 a.m. PT)**
Virtual
Each year brings new threats that take advantage of increasingly complex security environments. Whether it's Volt Typhoon targeting critical infrastructure organizations across the United States or ALPHV launching an attack against casino giant MGM, threat actors are becoming bolder and more evasive. That's why it's never been more important to leverage broad telemetry sources, deep network insights and threat intelligence to respond effectively and recover faster from sophisticated attacks. Join Amy Henderson, Director of Strategic Planning and Communications at Cisco Talos and Briana Farro, Director of XDR Product Management at Cisco, as they discuss some of the top threat trends and threats we have seen this past year and how to leverage security technology like XDR and network insights to fight against them.
NIS2 Directive: Why Organizations Must Act Now to Ensure Compliance and Security** (Jan. 11, 2024, 10 a.m. GMT)**
Virtual
_The NIS2 Directive is a crucial step toward securing Europe's critical infrastructure and essential services in an increasingly interconnected world. Organizations must act now to prepare for the new requirements, safeguard their operations, and maintain a robust cybersecurity posture. Gergana Karadzhova-Dangela from Cisco Talos Incident Response and other Cisco experts will talk about how organizations can best prepare for the coming regulations. _
Most prevalent malware files from Talos telemetry over the past week
SHA 256: bea312ccbc8a912d4322b45ea64d69bb3add4d818fd1eb7723260b11d76a138a **MD5:**200206279107f4a2bb1832e3fcd7d64c **Typical Filename:**lsgkozfm.bat **Claimed Product:**N/A Detection Name: Win.Dropper.Scar::tpd
SHA 256: 4c3c7be970a08dd59e87de24590b938045f14e693a43a83b81ce8531127eb440 **MD5:**ef6ff172bf3e480f1d633a6c53f7a35e **Typical Filename:**iizbpyilb.bat **Claimed Product:**N/A Detection Name: Trojan.Agent.DDOH
SHA 256: 5e537dee6d7478cba56ebbcc7a695cae2609010a897d766ff578a4260c2ac9cf **MD5: **2cfc15cb15acc1ff2b2da65c790d7551 **Typical Filename:**rcx4d83.tmp **Claimed Product:**N/A Detection Name: Win.Dropper.Pykspa::tpd
SHA 256: 8664e2f59077c58ac12e747da09d2810fd5ca611f56c0c900578bf750cab56b7 **MD5:**0e4c49327e3be816022a233f844a5731 **Typical Filename:**aact.exe **Claimed Product:**AAct x86 Detection Name: PUA.Win.Tool.Kmsauto::in03.talos
SHA 256:77c2372364b6dd56bc787fda46e6f4240aaa0353ead1e3071224d454038a545e
MD5: 040cd888e971f2872d6d5dafd52e6194 **Typical Filename:**streamer.exe **Claimed Product:**Ultra Virus Killer Detection Name: PUA.Win.Virus.Ultra::95.sbx.tg
8.8 High
CVSS3
Attack Vector
NETWORK
Attack Complexity
LOW
Privileges Required
NONE
User Interaction
REQUIRED
Scope
UNCHANGED
Confidentiality Impact
HIGH
Integrity Impact
HIGH
Availability Impact
HIGH
CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
7.4 High
AI Score
Confidence
High
6.8 Medium
CVSS2
Access Vector
NETWORK
Access Complexity
MEDIUM
Authentication
NONE
Confidentiality Impact
PARTIAL
Integrity Impact
PARTIAL
Availability Impact
PARTIAL
AV:N/AC:M/Au:N/C:P/I:P/A:P
0.001 Low
EPSS
Percentile
49.1%