UNAUTHENTICATED START OF TELNETD ON TENDA AC15 ROUTER
0.007 Low
EPSS
Percentile
80.5%
INTRODUCTION
We previously showed how the Tenda AC15 router was vulnerable to an unauthenticated remote code execution vulnerability via a stack based buffer overflow. Writing exploits like that can be incredibly interesting, but sometimes, all you need is a GET request to get root.
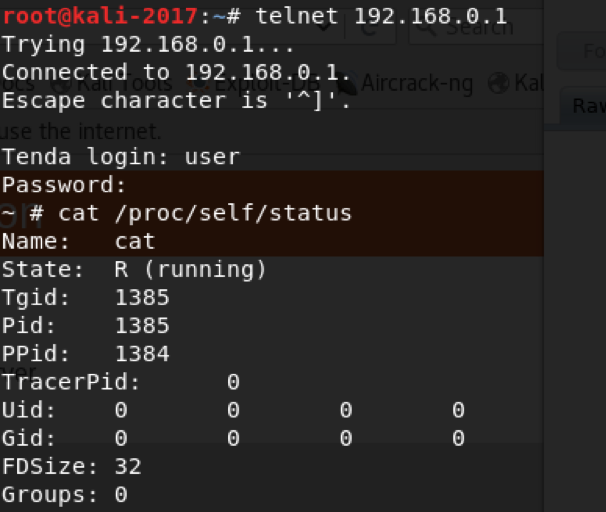
In this post we will outline another vulnerability that allows an unauthenticated remote user to start a telnetd service on the device which, when coupled with hard coded backdoor accounts, gets us root.
SHORT AND SWEET
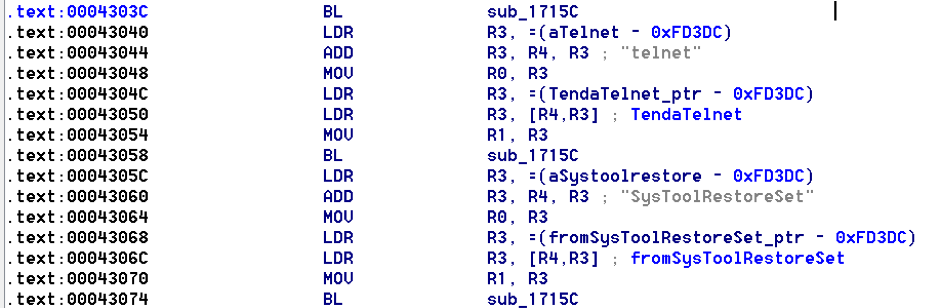
The httpd binary responsible for the web service contains a form hard coded into the binary itself (by this we mean that it isn’t present in the webroot).
In sub_42478 we have a registering of handlers for different URL’s, one of which is simply “telnet”:
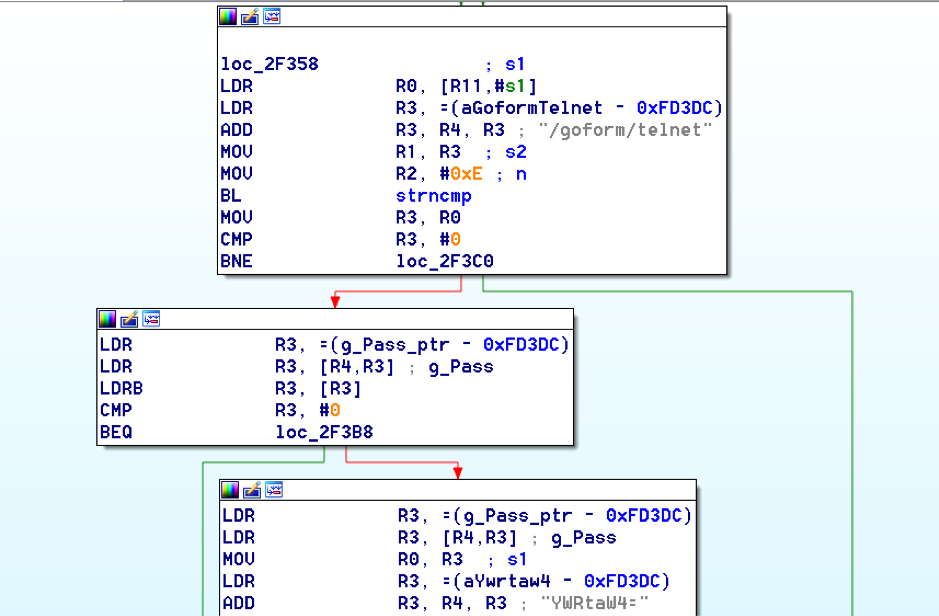
In R7WebsSecurityHandler we then have the code that handles parsing requests, it contains the following block:
Put simply, we are able to make a request to this URL (/goform/telnet) and start a telnet daemon on the device. Combined with CVE-2018-5768 this allows for root compromise.
TIMELINE
-
Vulnerability discovered and first reported by Fidus’ UK Penetration Testing Team- 14/1/2018
-
Second attempt to make contact, further informing the vendor of the severity of the vulnerability – 18/1/2018
-
CVE’s assigned by Mitre.org – 19/1/2018
-
Livechat attempt to contact vendor – 19/1/2018
-
Another attempt to contact vendor 23/1/2018
-
Further attempt to contact vendor, confirming 5 CVE’s had been assigned to their product – 31/1/2018
-
Final contact attempted & warning of public disclosure – 8/2/2018
-
Public disclosure – 19/3/2018