Node.js arbitrary file read Vulnerability(CVE-2017-14849)
EPSS
Percentile
99.5%
Author: niubl@TSRC
1. Vulnerability description
2017 9 November 28, the company scanner found a business there is an example of the arbitrary file read vulnerability, the team follow-up analysis found that this is the Node. js and Express the common result of a Common Vulnerability. As we prepare to inform the official, The found Node. js official website to 9 on 29, shows the vulnerability announcement, and the corresponding CVE number for CVE-2017-14849。
1.1 关于Node.js
Node. js is a Javascript Runtime Environment(runtime), released in 2009 for 5 months, by Ryan Dahl developed, in essence, is the Chrome V8 engine package. Node. js for some of the special cases for optimization, to provide an alternative API, such that a V8 in a non-browser environment run better.
1.2 about Express
Express is a concise and flexible node.js Web application framework, providing a range of powerful features to help you create a variety of Web applications. Express does not node.js the existing characteristics of the secondary abstraction, we are just on the top of it extended the Web application the desired functionality. Rich the HTTP tool from the Connect framework middleware with the take with the use, create a robust, friendly API is quick and easy.
1.3 vulnerability
Node.js 8.5.0 + Express 3.19.0-3.21.2
Node.js 8.5.0 + Express 4.11.0-4.15.5
2. Vulnerability demo
- 安装Node.js 8.5.0
- 下载并解压express-4.15.5.zip
- expresss-4.15.5 directory execute npm install
- expresss-4.15.5/examples/static-files directory in the implementation of nodejs index.js
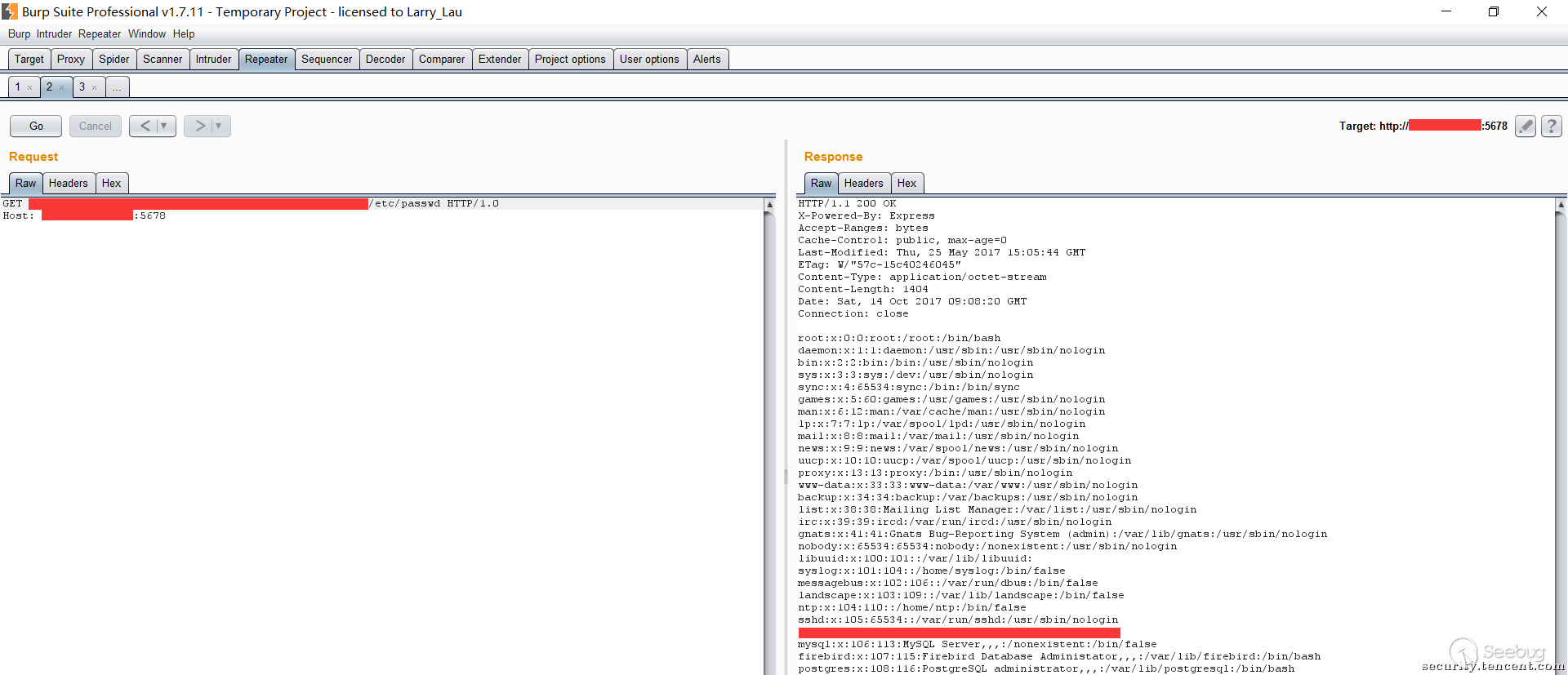
- The use of POC tests, web listening to the 5678 port, default 3000 the following figure
3. Vulnerability analysis
Express reliance on the Send component, Send component 0. 11. 0-0. 15. 6 version of the pipe()function, as shown:
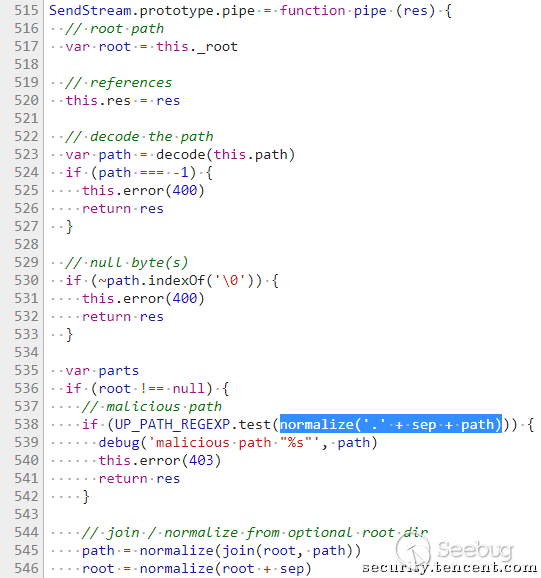
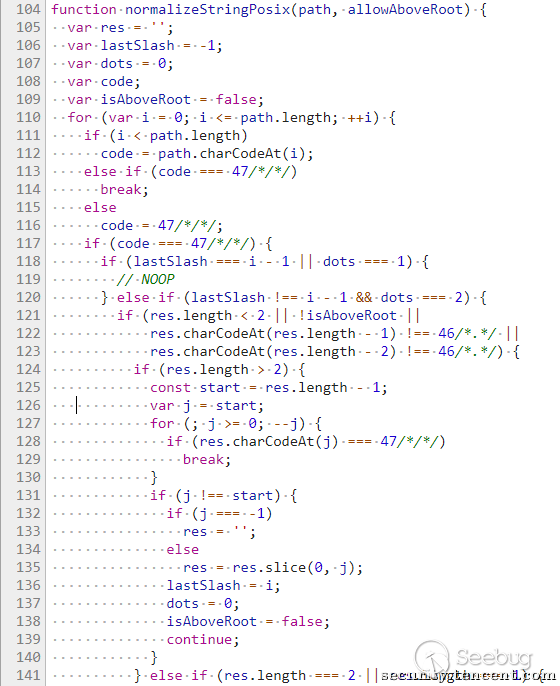
The Send module by normalize('.' + sep + path) standardized path path, and not assigned to a path, but merely determine the whether there is a directory jump characters. If we can bypass the directory jump character of the judgment, you can put the directory jump character into 545 the rows of the join(root, path) function, jump to we want to jump to the directory, this is the Send module of a bug has now been fixed.
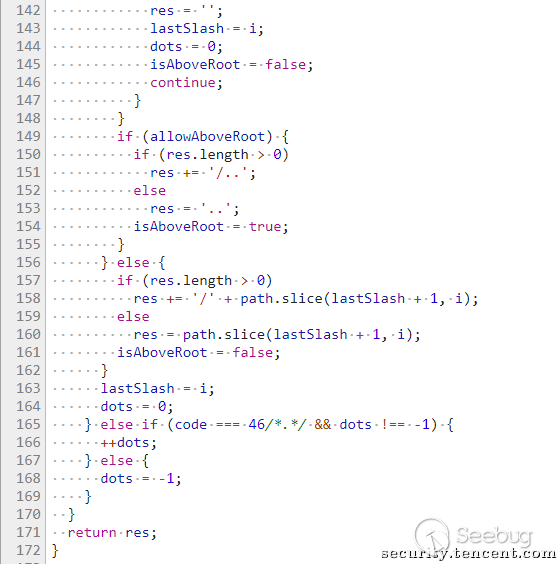
再来看Node.js that Node.js 8.5.0 the path. js file in the normalizeStringPosix function has been modified, so that it can be the path to do the following standardization: assert. strictEqual(path. posix. normalize('bar/foo../..'), 'bar'); New modifications brought to the problem, by stepping through we found that, by foo../../and directory jump characters together is injected into the path, foo../../you can put variables isAboveRoot set to false code 161 rows, and in the code 135 line put your own delete; variable isAboveRoot for the false case, can be in the foo../../both sides set the same number of jump characters, make them the same in code 135 line to remove yourself, so that you can construct a A with a jump character, but by normalizeStringPosix function after normalization will all automatically remove the payload, the payload with the above-mentioned Send module bug will be able to successfully return the one we want the physical path, and finally in the Send module reads and returns the file.normalizeStringPosix function as shown below: